Hello, aspiring ethical hackers. In our previous blogpost, you learnt about threat intelligence. In this article, you will learn everything you need to know about Security Information & Event Management or SIEM solutions and its role in threat intelligence.
What is SIEM?
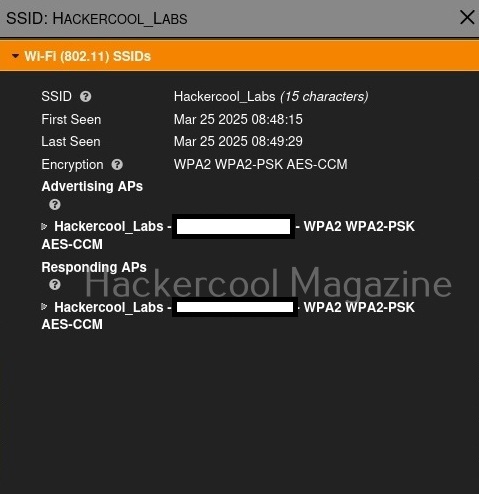
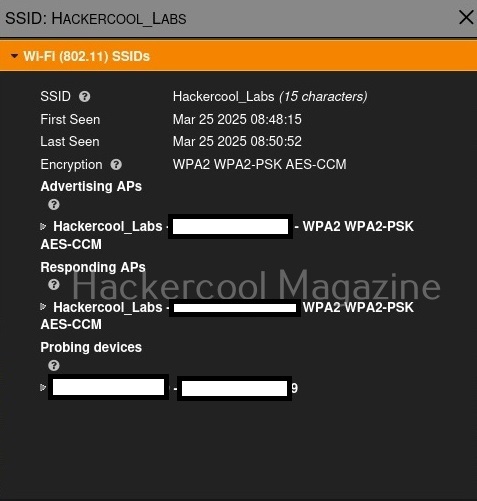
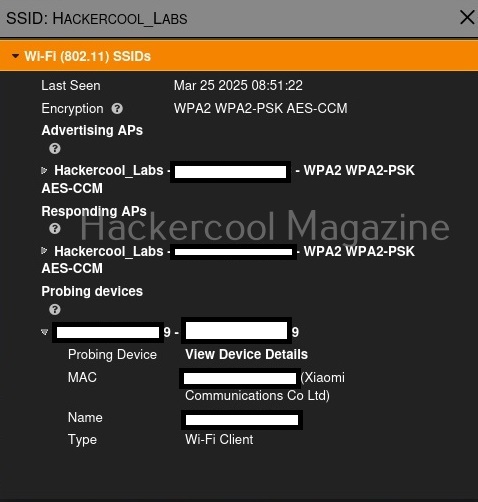
You have learnt in threat intelligence that data & information related to security is collected, processed and analyzed to detect upcoming threats to the organization. This data not only includes external data but also data from the organization’s network itself.
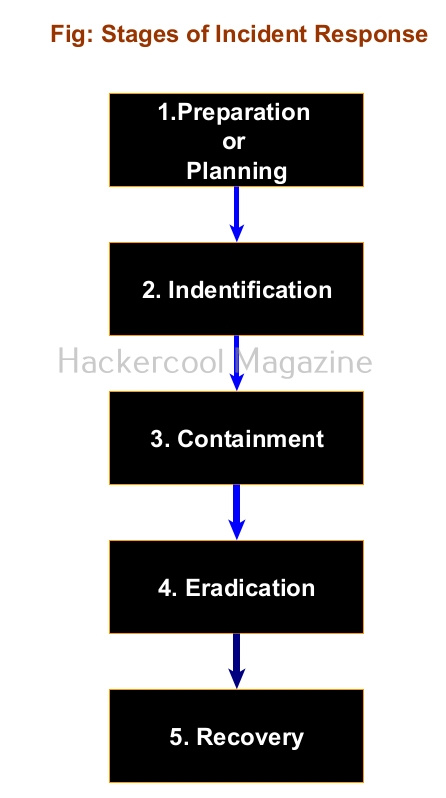
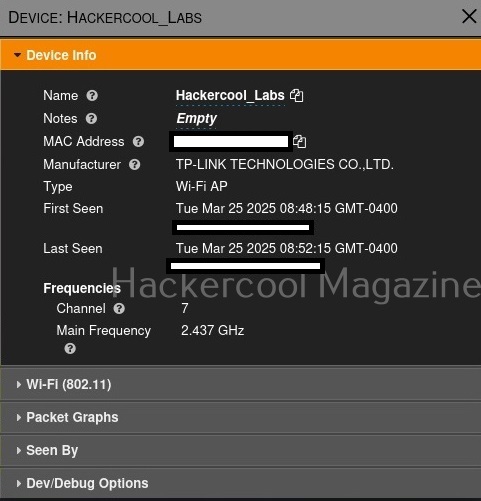
A Security Information & Event Management solution’s role comes here. It collects information, stores, processes, analyzes and upgrades security related data from multiple devices from the organization. This also helps in proper incident response. SIEM can collect, aggregate, analyze data from multiple devices in a network like Firewalls, IDS, IPS, Network gateways, Honeypots, Wireless access points, Endpoint security solutions, Routers, Switches etc. If it finds anything suspicious, it can trigger an alert and even quarantine the resource.
SIEM is a combination of Security Information management (SIM) and Security Event Management (SEM) solutions. It can be considered a successor to log viewers and event management tools.
Importance of SIEM
You have just now learnt that Log analysis tools and Event viewer tools are the predecessors of SIEM solutions. Well, manually viewing and analyzing logs and events can be a process requiring efforts of huge proportions. Just imagine that with multiple devices in a network, instead of a single system. This can directly affect the security of the organization as most of the threats nowadays require immediate response.
Here’s where a SIEM solution proves resourceful. It not only simplifies and automates but also enhances the security of the organization. Some popular SIEM vendors include Splunk, IBM QRadar, LogRhythm, Microsoft Sentinel, Securonix, Exabeam, Sumologic etc.