Hello, aspiring ethical hackers. This is a complete guide to dnsrecon tool. In our previous blogpost on DNS enumeration, you read what DNS is, what are the various types of DNS records, what is the information about the network can DNS enumeration reveal to a pen tester or a Black Hat Hacker. DNSrecon is one such tool used for enumerating DNS.
DNSrecon is written by Carlos Perez. He wrote it initially in Ruby to learn about that programming language and about DNS way back in 2007. As time passed by, he wanted to learn python and he posted dnsrecon tool to python.
The features of DNSrecon tool are,
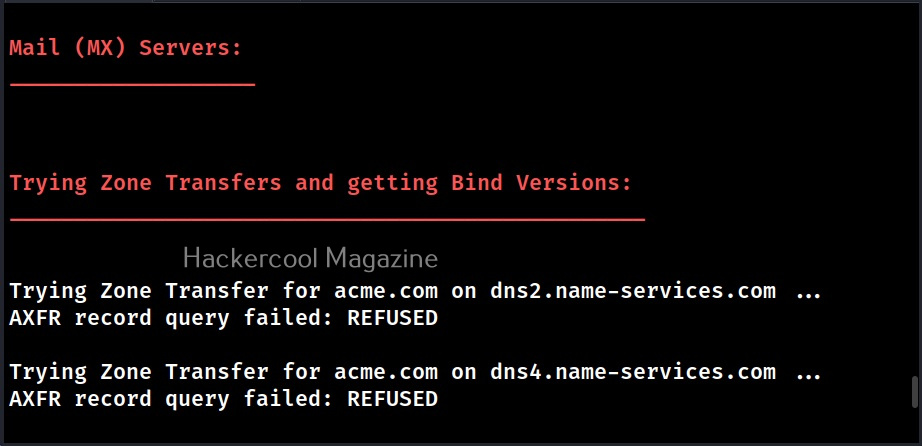
- Checks all NS Records for Zone Transfers.
- Enumerates general DNS Records for a given domain (MX, SOA, NS, A, AAAA, SPF and TXT).
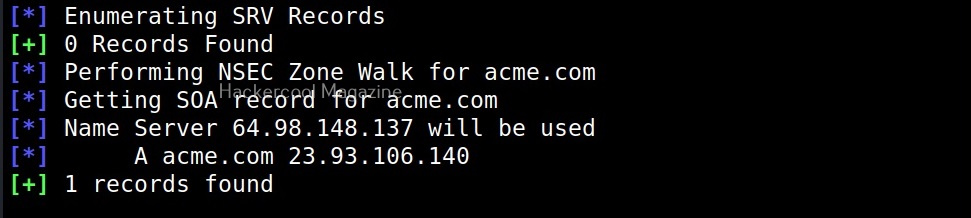
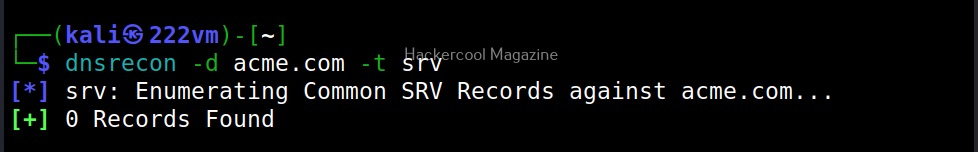
- Performs common SRV Record enumeration.
- Top Level Domain (TLD) expansion.
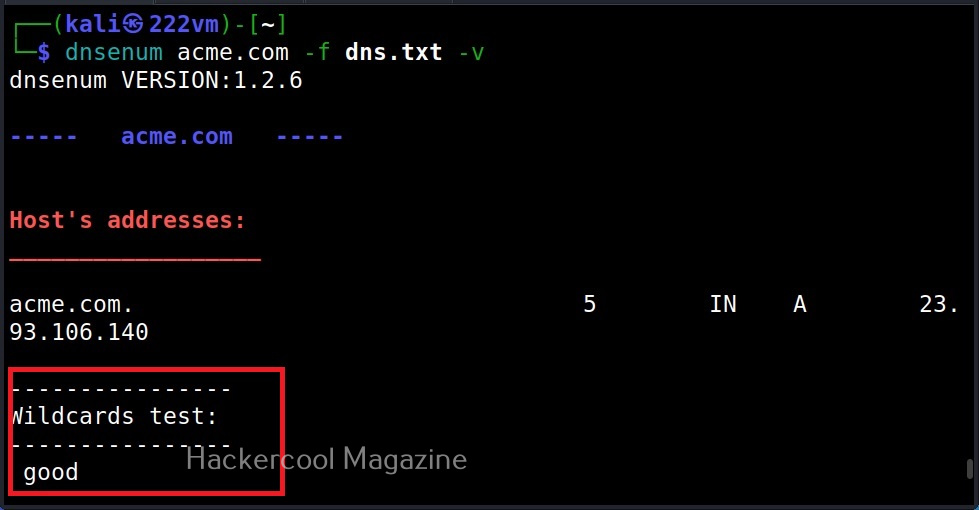
- Checks for Wildcard resolution.
- Brute forces subdomains and host A and AAAA records given in a domain and a wordlist.
- Performs PTR record lookup for a given IP Range or CIDR.
- Checks a DNS server’s cached records for A, AAAA and CNAME.
- Records provided a list of host records in a text file to check.
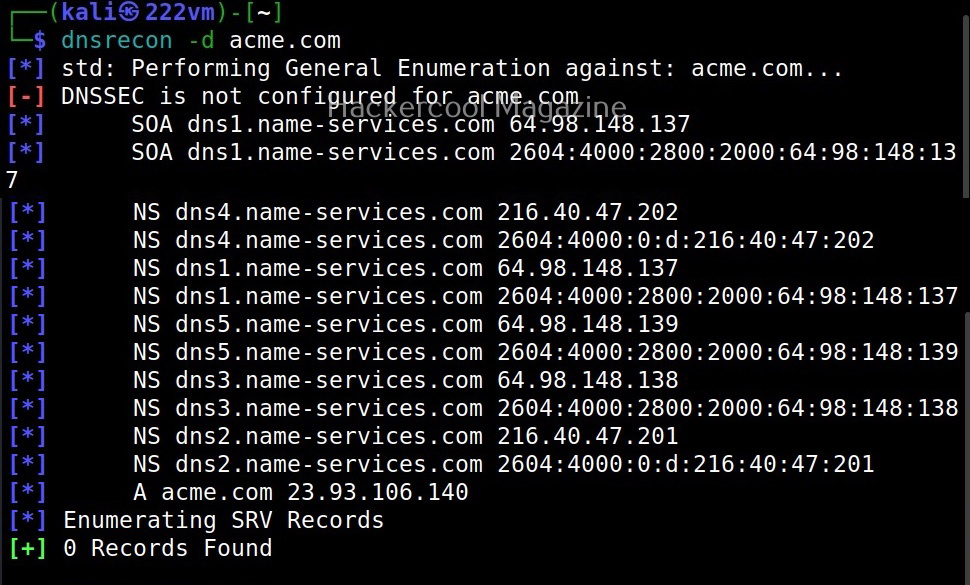
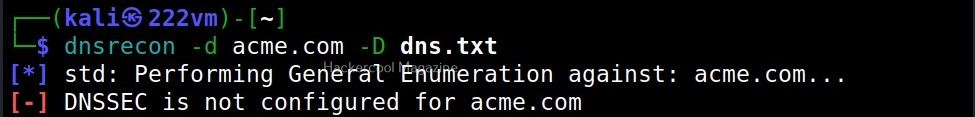
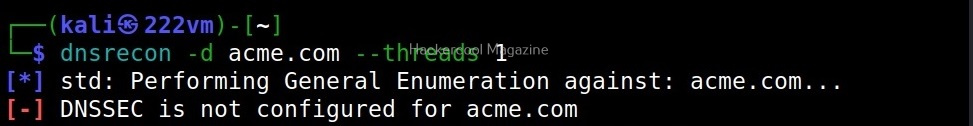
Let’s see how to enumerate DNS with DNSrecon. DNSrecon is installed by default in Kali Linux. To use DNSrecon, all we have to do is use the command below.
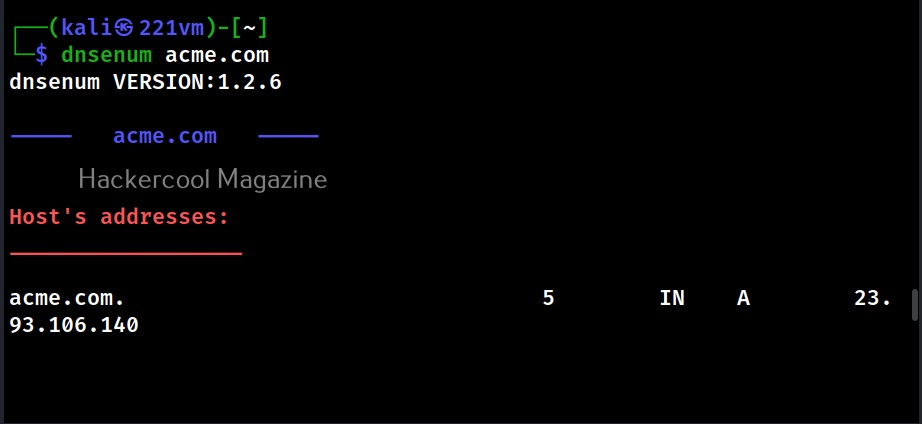
dnsenum -d <domain>
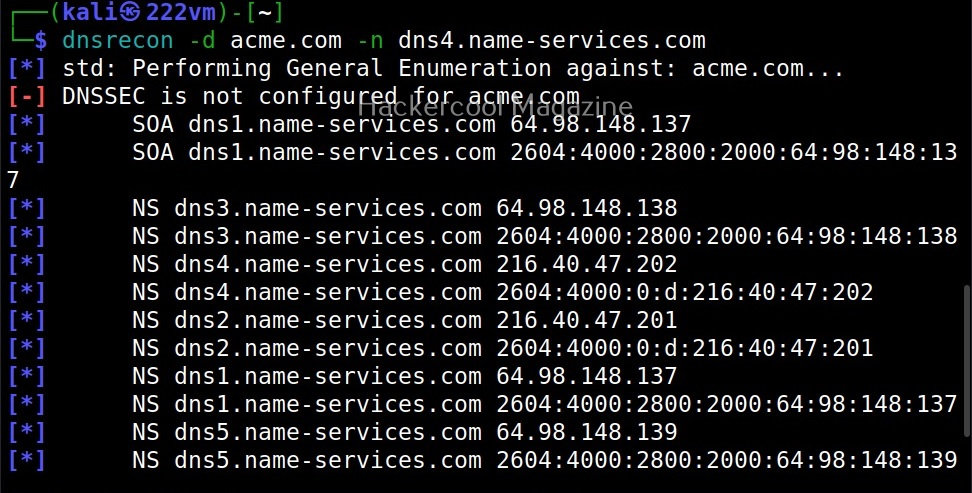
–name_server (-n)
By default, DNSrecon will use SOA of the target server to enumerate DNS. You can use a different server, you can use it using this option.
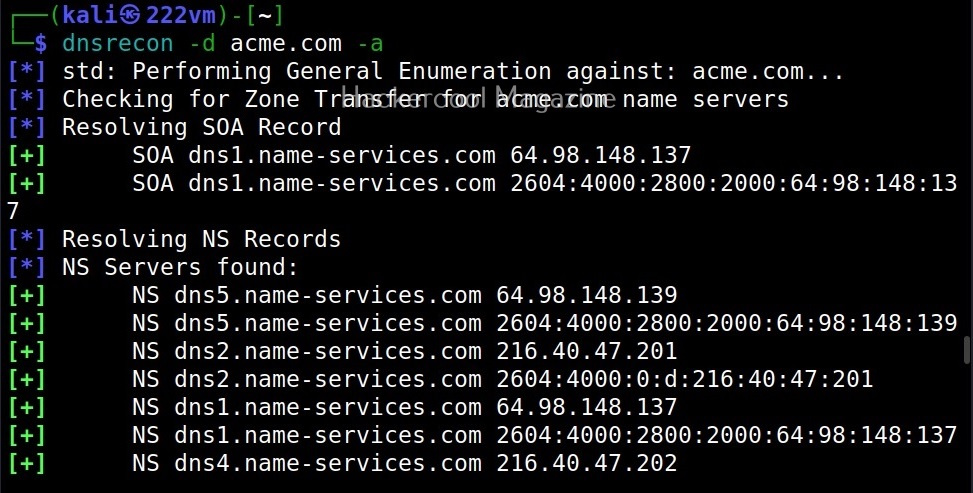
-a
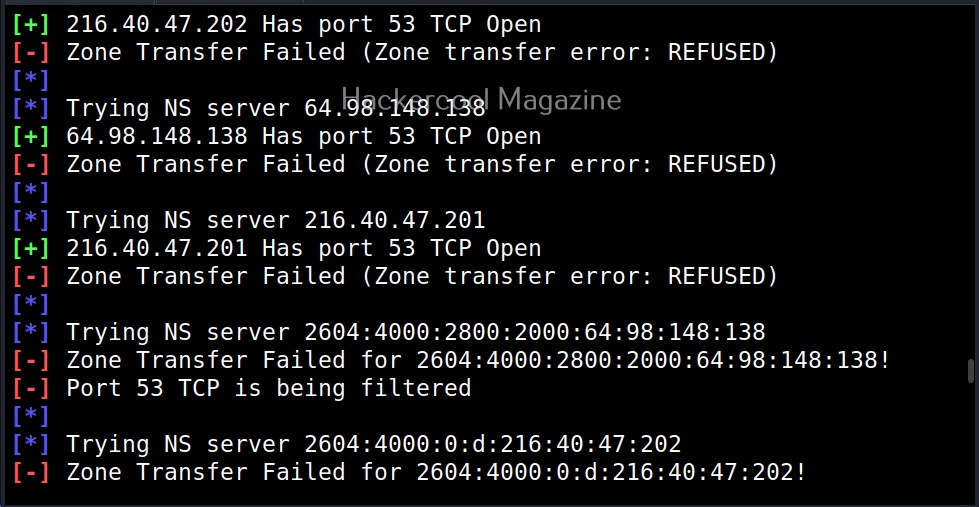
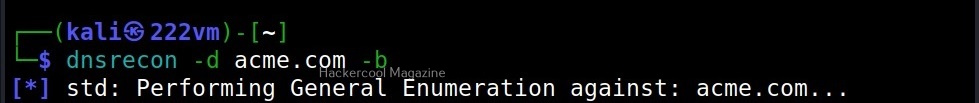
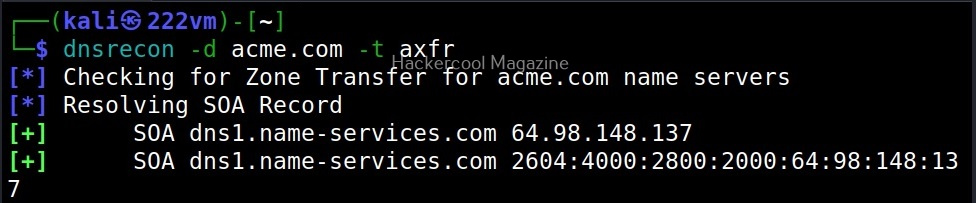
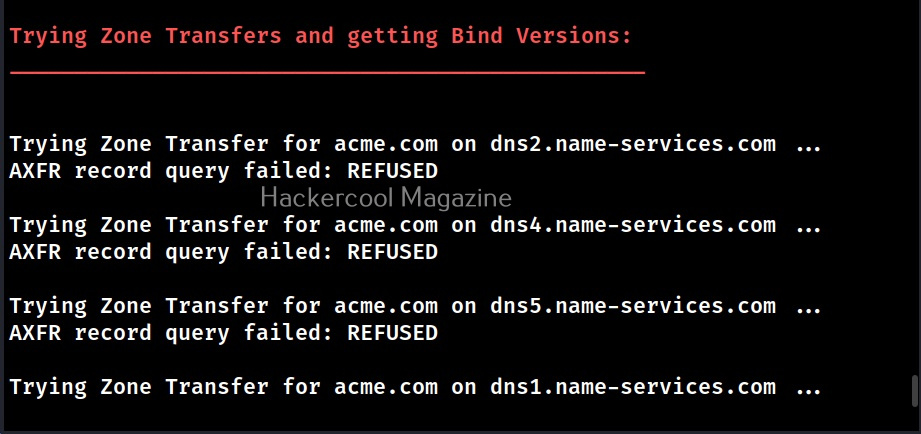
This option is used to do a zone transfer along with standard enumeration performed above.
As expected it failed.
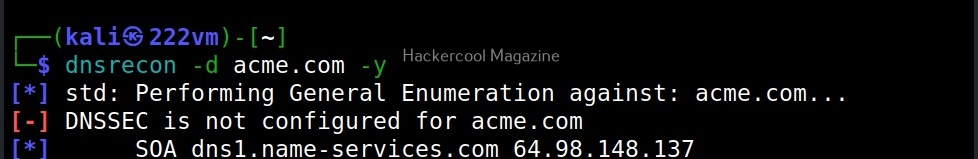
-y, -b, -k
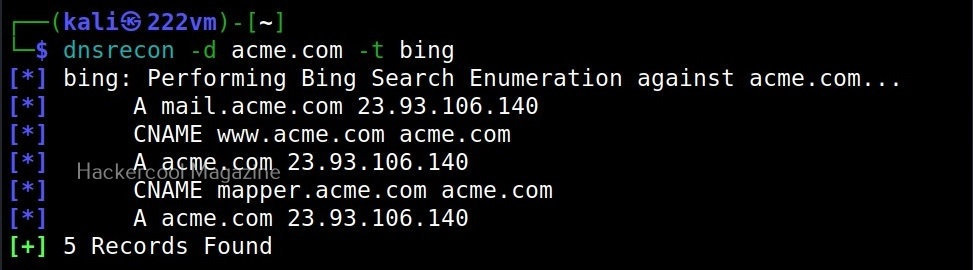
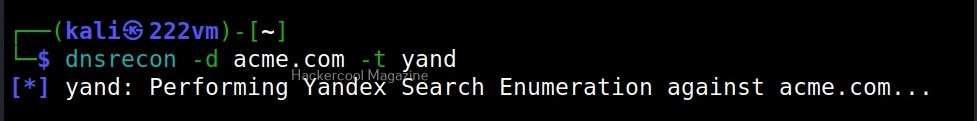
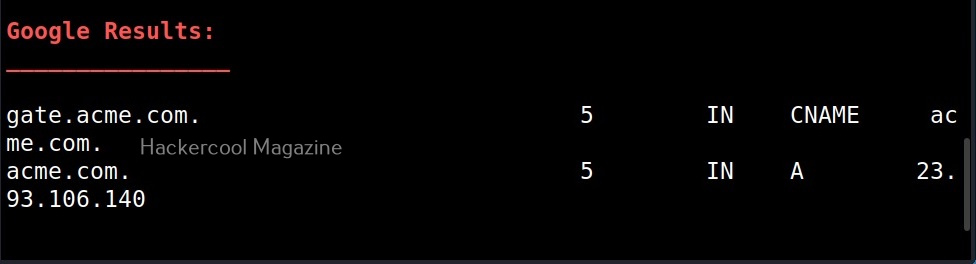
Similarly, you can perform yandex (-y), bing(-b), crt.sh (-k) enumeration along with standard enumeration.
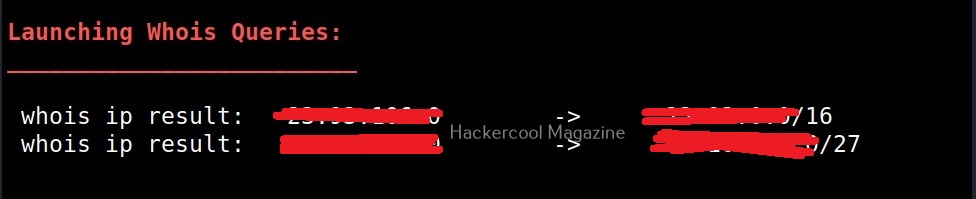
-w
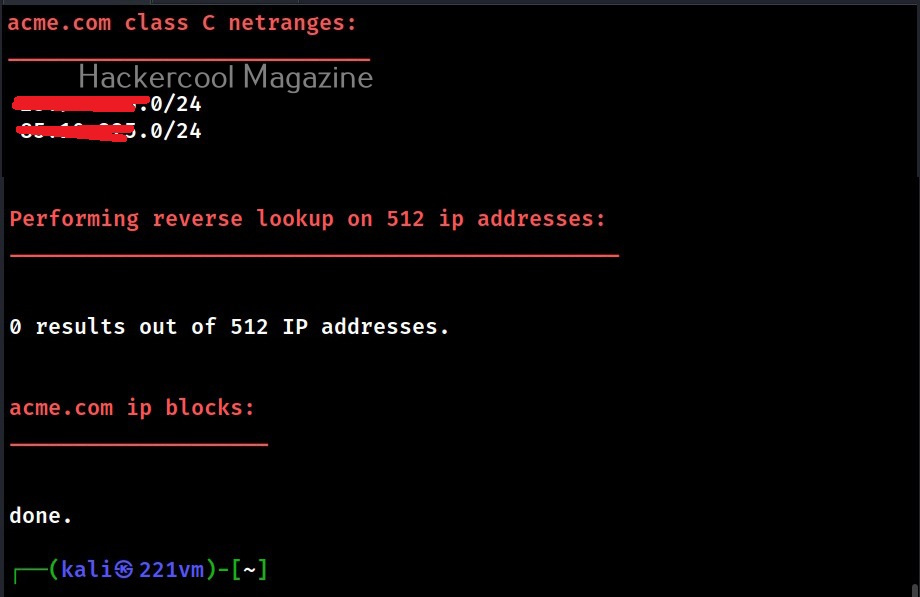
This option is used to perform deep whois record analysis and reverse lookup of IP ranges found when doing standard enumeration.
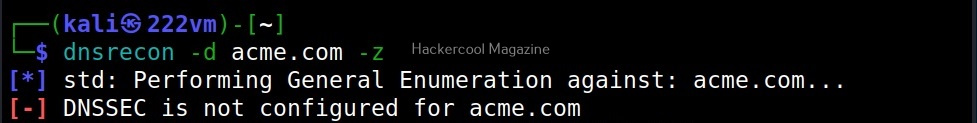
-z
This option is used to perform a DNSSEC zone walk along with standard enumeration.
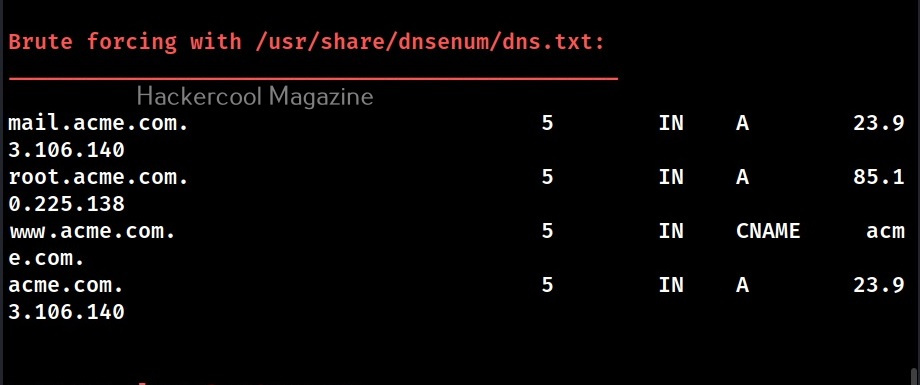
–dictionary (-d)
This option is used to use a dictionary file containing subdomains and hostnames to use for brute force.
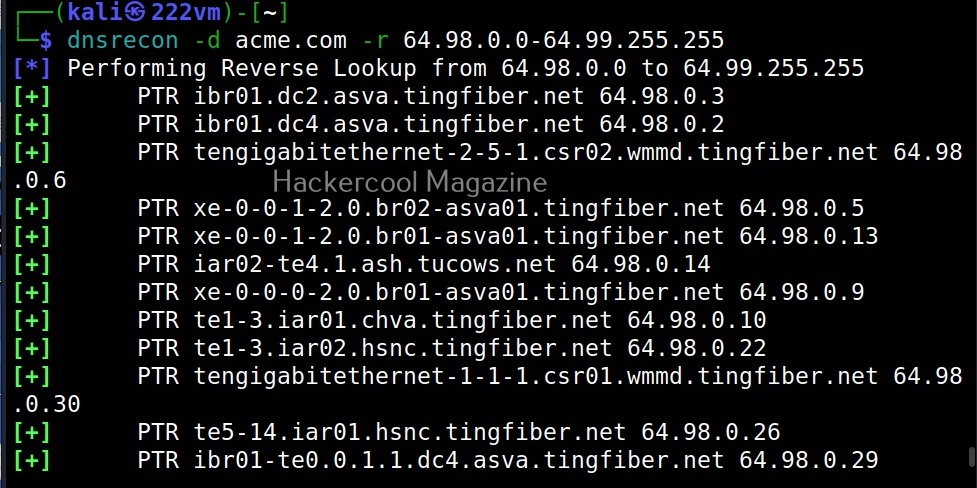
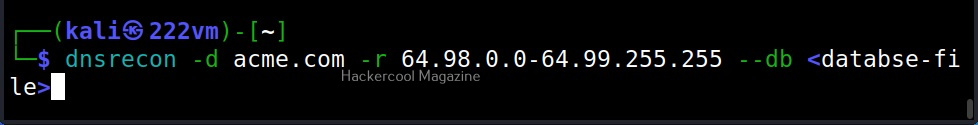
–range (-r)
Specify a IP range to perform reverse lookup.
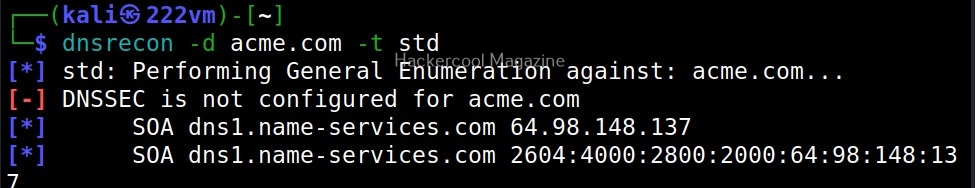
–type (-t)
This option is used to perform a specific type of enumeration only. The various possible types of enumeration that can be performed using dnsrecon are,
- Std: all SOA, NS, A, AAAA, MX and SRV.
- rvl: reverse lookup
- brt: brute force using a given dictionary
- srv: SRV records.
- axfr: zone transfer from NS server.
- bing: Bing search for hosts and subdomains.
- Yand: Yandex search for hosts and subdomains.
- Crt: crt.sh enumeration for subdomains and hosts.
- Snoop: cache snooping argument at NS server.
- tld: test against all TLD’s registered with IANA.
- Zonewalk: perform DNS sec Zone using NSEC records.
Saving results
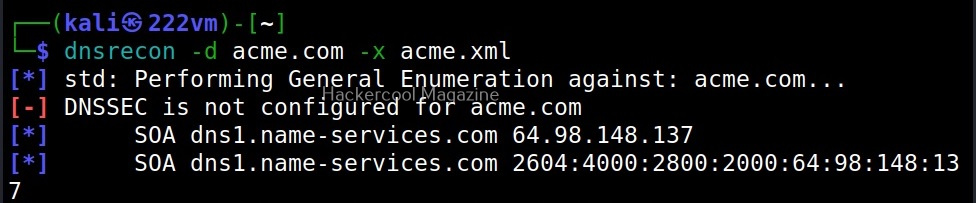
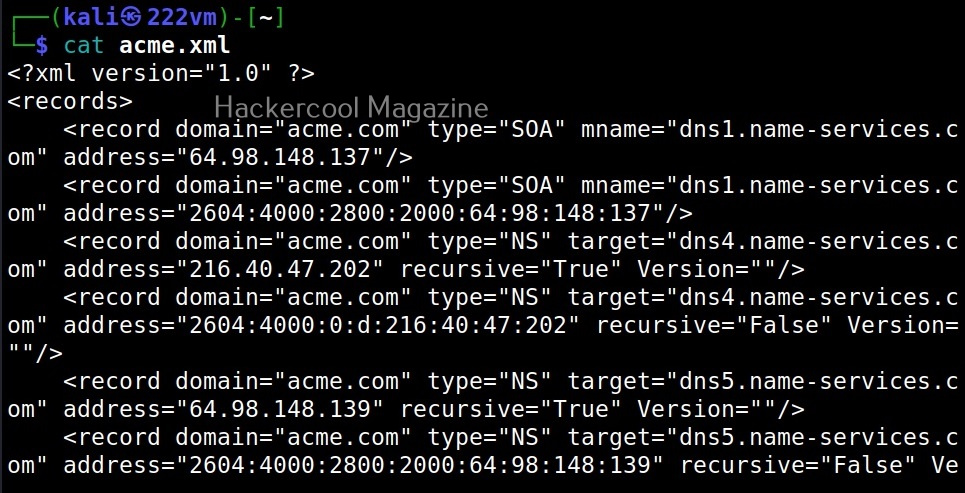
You can save the results of the found records to a database (-db), XML (-X), CSV (-c) and Json(-j) files.
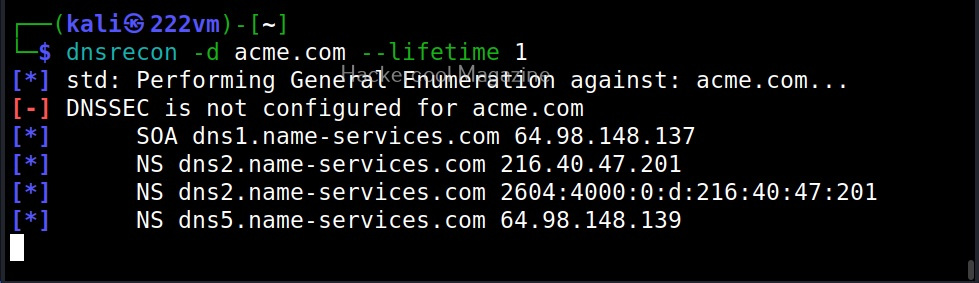
–lifetime
This option is used to set the time the tool has to wait until the target server responds. The default time is 3 seconds.
–threads
This option is useful to specify the number of threads to be used while performing reverse lookup, forward lookup, brute force and SRV record enumeration.
That’s all about DNSrecon.