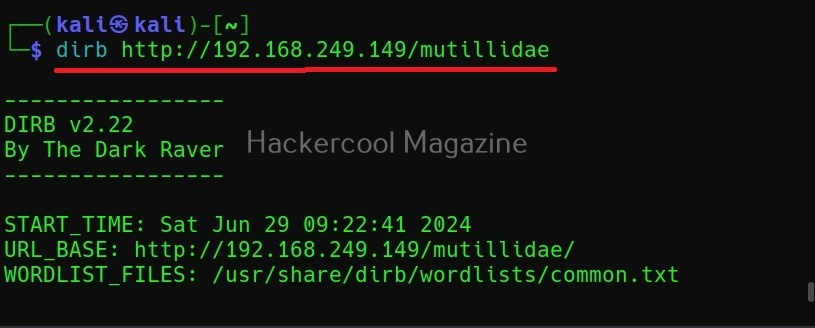
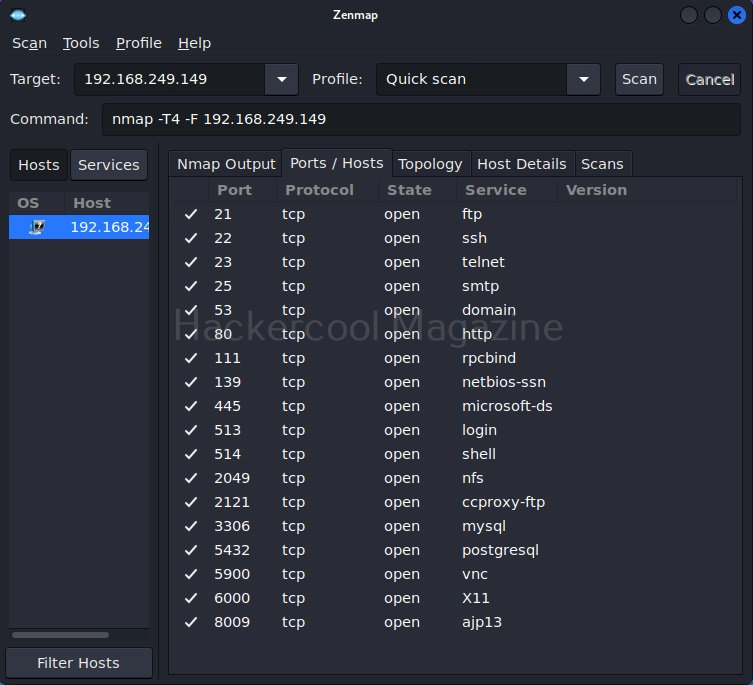
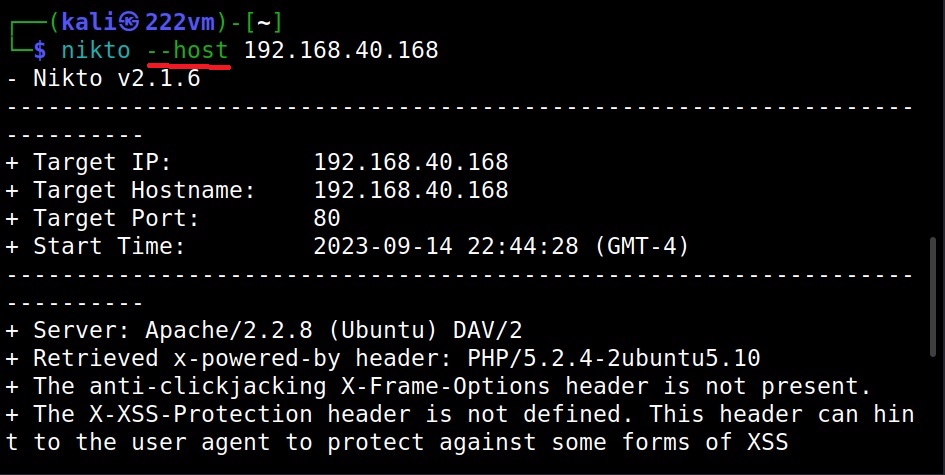
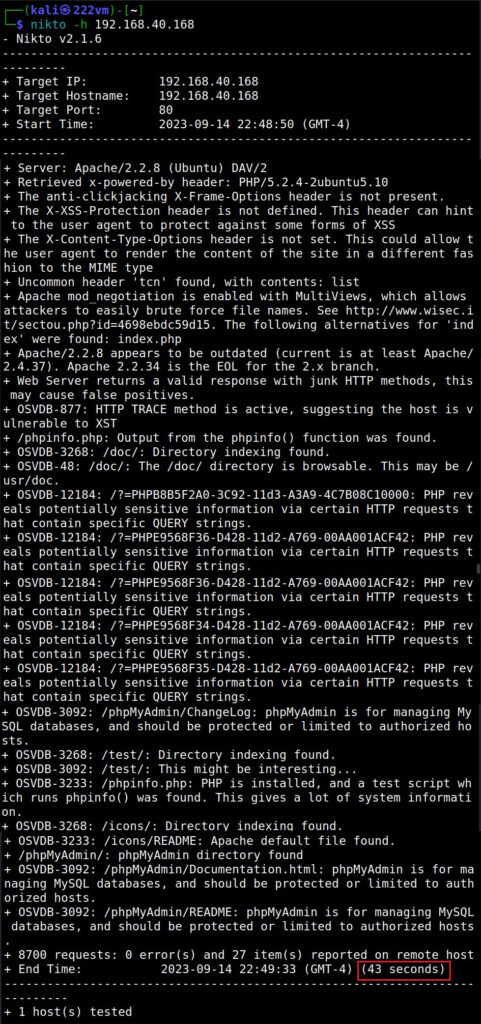
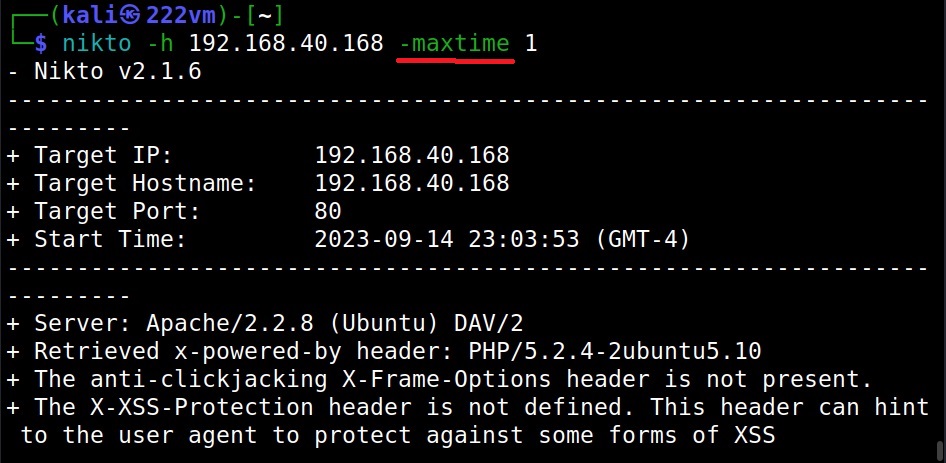
Hello, aspiring ethical hackers. In one of our previous blogposts, you learnt in detail about website footprinting. In this blogpost, you will learn in detail about dirb tool, a tool often used in website footprinting. DIRB is an open-source web content or directory scanner. It is used to scan for web objects.
DIRB achieves this by using a pre-configured wordlist to perform a dictionary attack on the web server specified as target. The default usage of DIRB is given below.
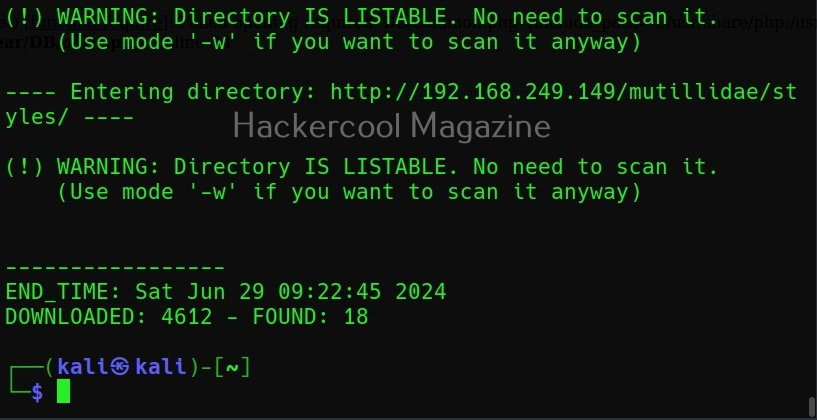
Here is its output.
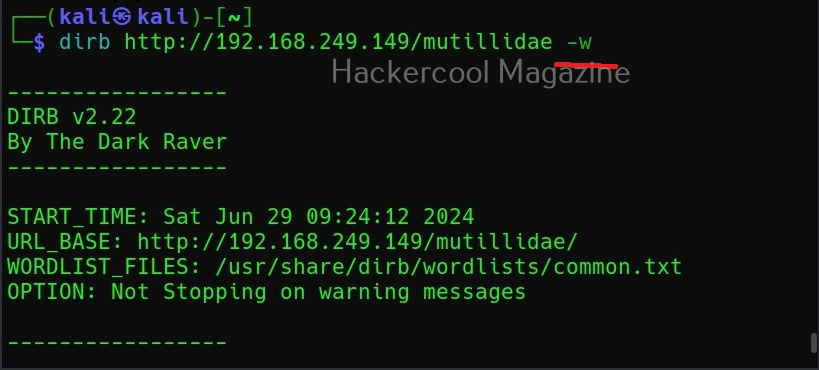
Ignore the warnings (-w)
By default, while scanning, it avoids going into any directories that are listable. This makes common sense too. It displays the message saying “directories are testable”. If you want it to scan inside such directories, you can use this option (-w).
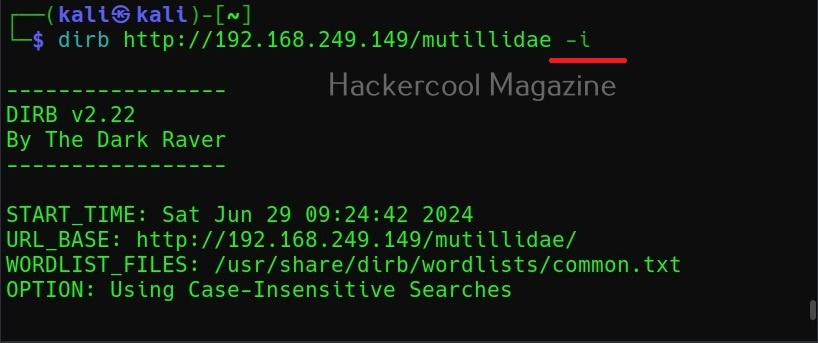
Use case-insensitive search (-i)
Usually, DIRB scans uses case-sensitive searches. Setting this option allows to perform case-insensitive searches.
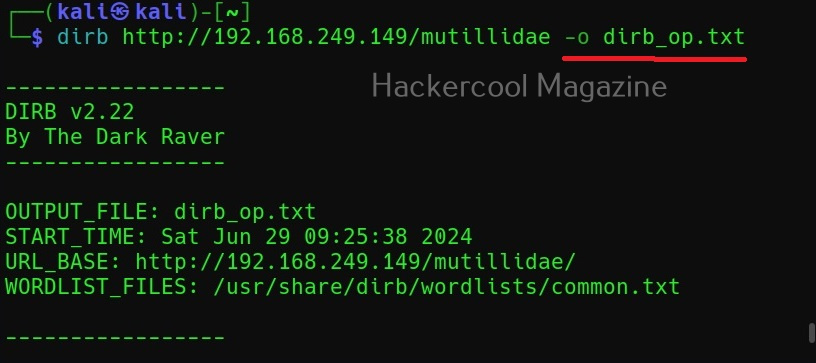
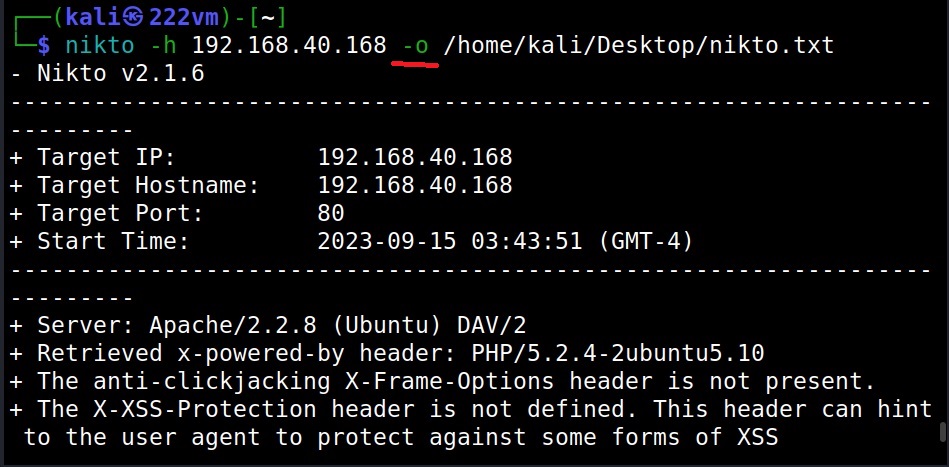
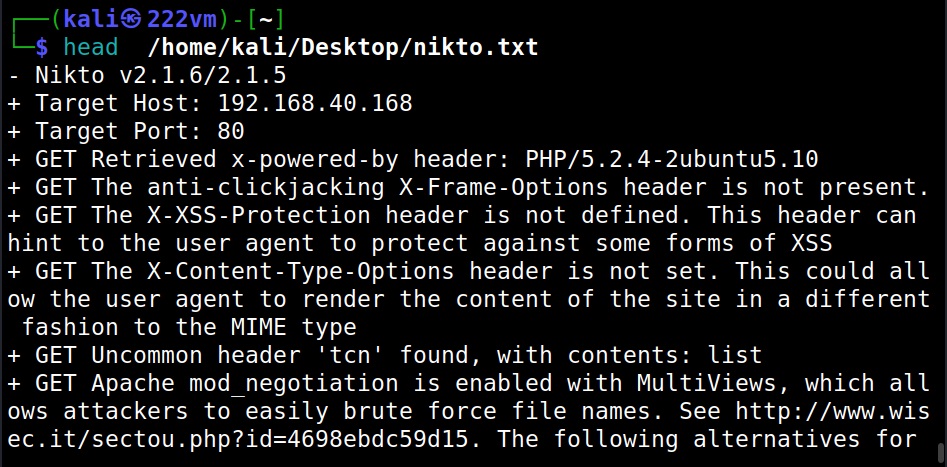
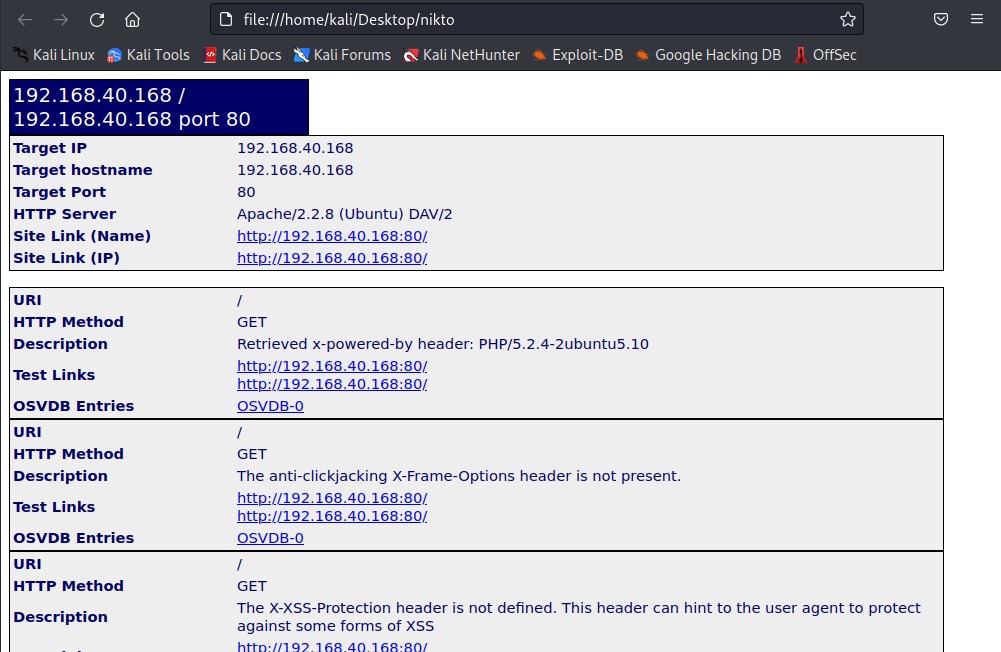
Saving the output (-o)
You can save the output of this tool to a file using the “-o” option.
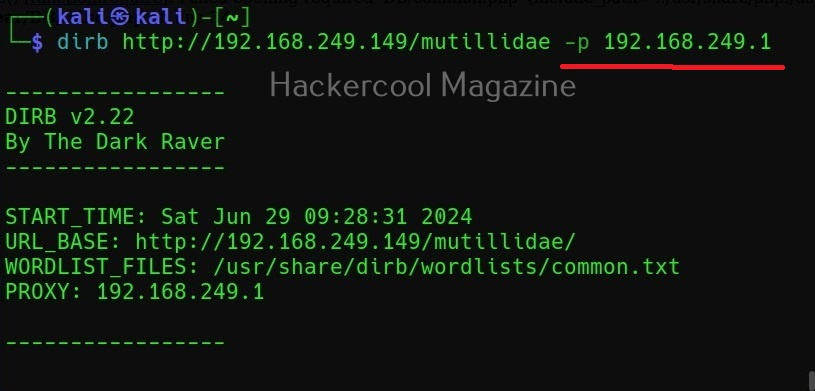
Scan using a proxy (-p)
For all its awesome features, it produces a lot of noise which can raise suspicions on the target side. To beat this a bit, DIRB provides a option to use a proxy to perform directory busting.
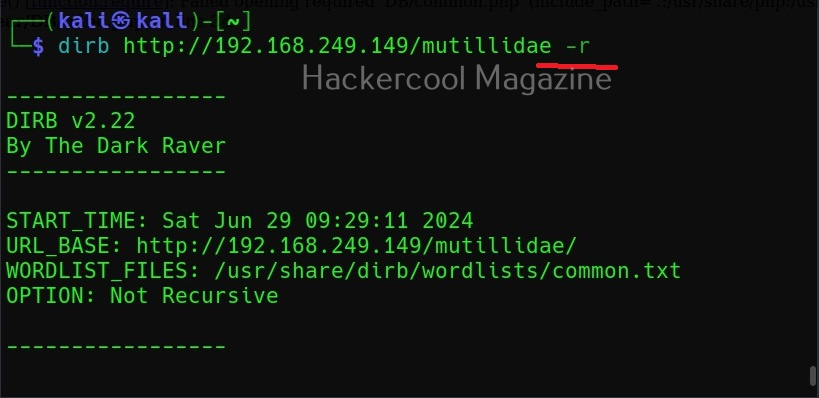
Don’t perform recursive searches (-r)
Setting this option will stop dirb from performing recursive scan of the directories.
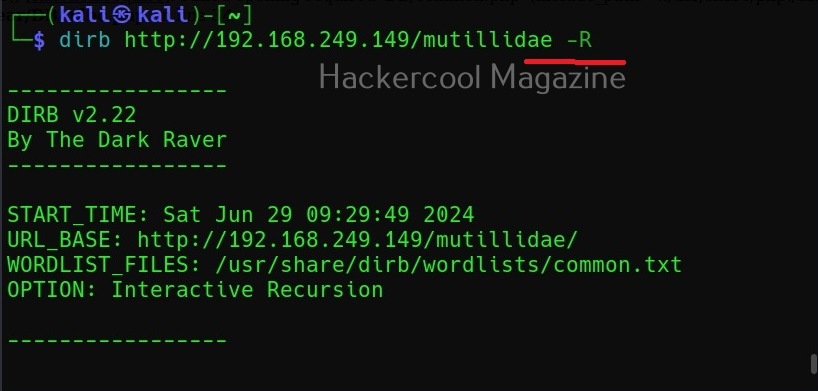
Interactive recursion (-R)
Similarly, this option is used to set Interactive Recursion while scanning.
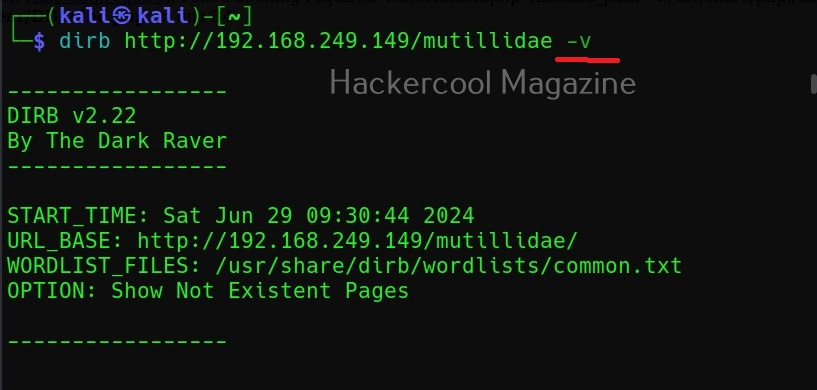
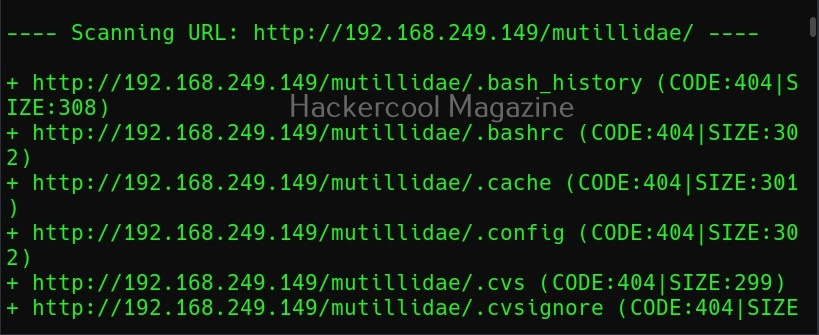
Show pages that don’t exist (-v)
By default, DIRB scans the web server and shows only pages or directories that are found on it. Setting this option will make it show non-existent objects also.
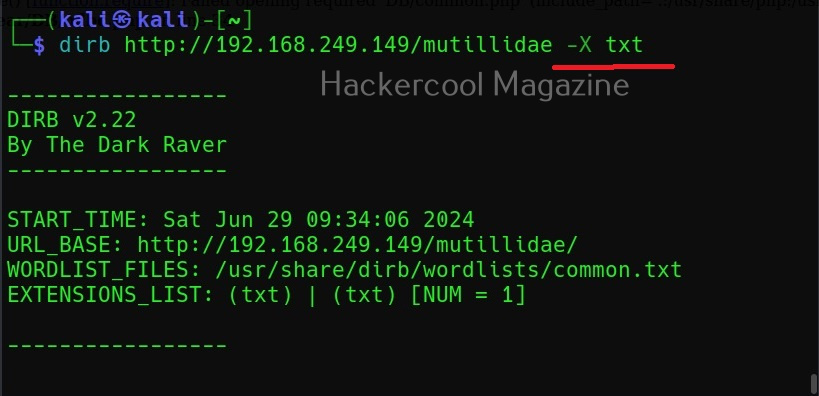
Search for files with a specific extension (-X)
You can use this option if you want to search for files with a particular extension. For example, to search for text files (.txt) extension, we can use dirb as shown below.
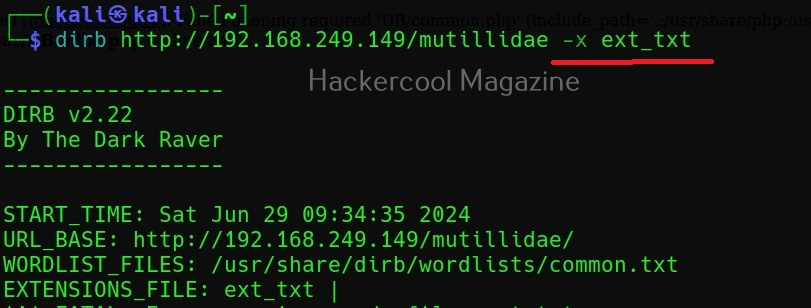
You can also search for multiple file extensions using dirb. Just add all the file extensions you want to search for in a text file and use the (-x) option as shown below. For example, to search for all file extensions specified in a file named “ext_text”.