Good Evening friends. Today we will see how to setup Vulnerawa in Wamp Server. For those newbies who don’t know what is Vulnerawa, it is a vulnerable web app coded by me to simulate a real website for practice. Read more about it here. First, download Wamp Server from here as appropriate to your system requirements. We will use “WAMPSERVER (64 BITS & PHP 5.3.10) 2.2d″ for this howto. Install the Wamp Server. Open browser and type “localhost” in the URL bar to see if Wamp server is working as shown below.
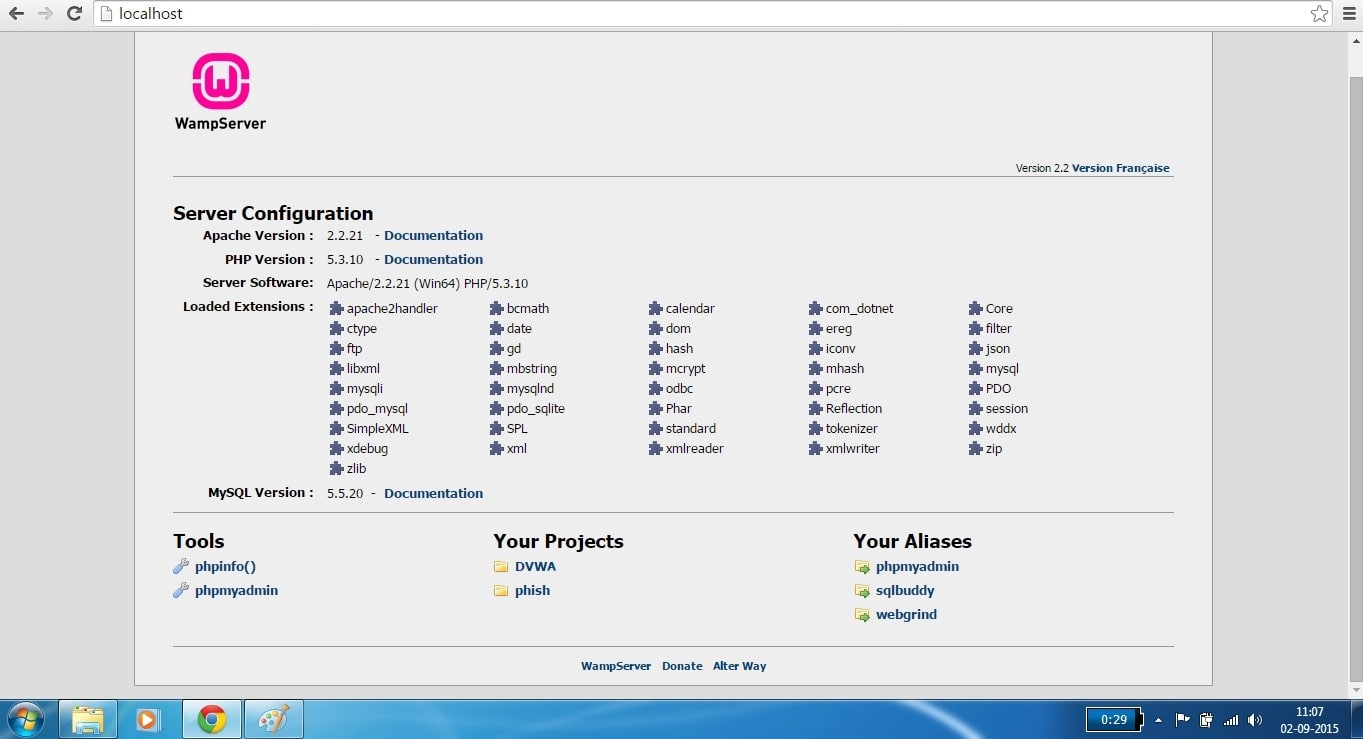
We can see that there are no projects available. Now download Vulnerawa from here. You will find a zip file as shown below. Now we will extract the contents of this file into the root folder of Wamp server. Right click on the zip file, go to 7-zip as shown below ( or any other unzipping software ) and select “Extract files”option. Extract the files to the folder “C:\\wamp\www” which is the root folder for Wamp server.
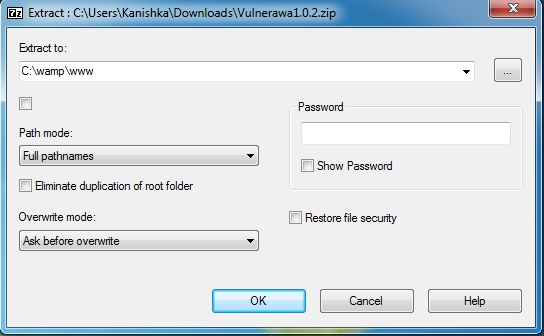
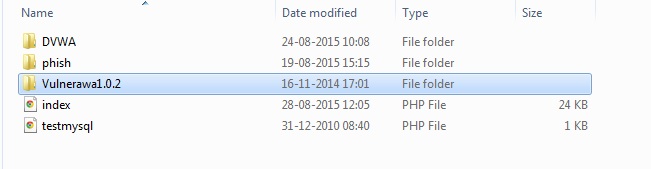
Now lets check the root folder to see if the files are extracted. Go to wamp server’s root directory and you should see the folder named “vulnerawa1.0.2” as shown below.
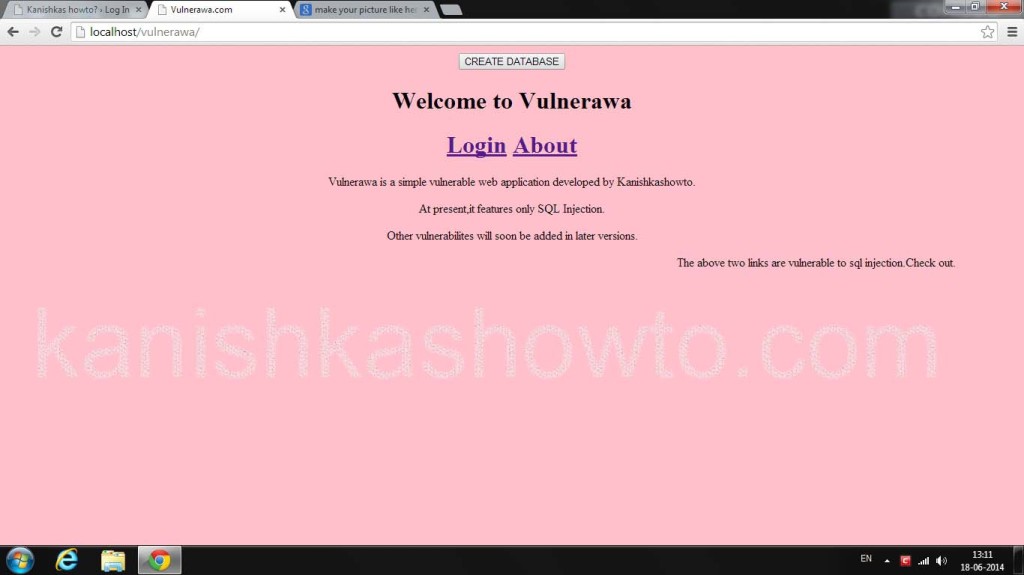
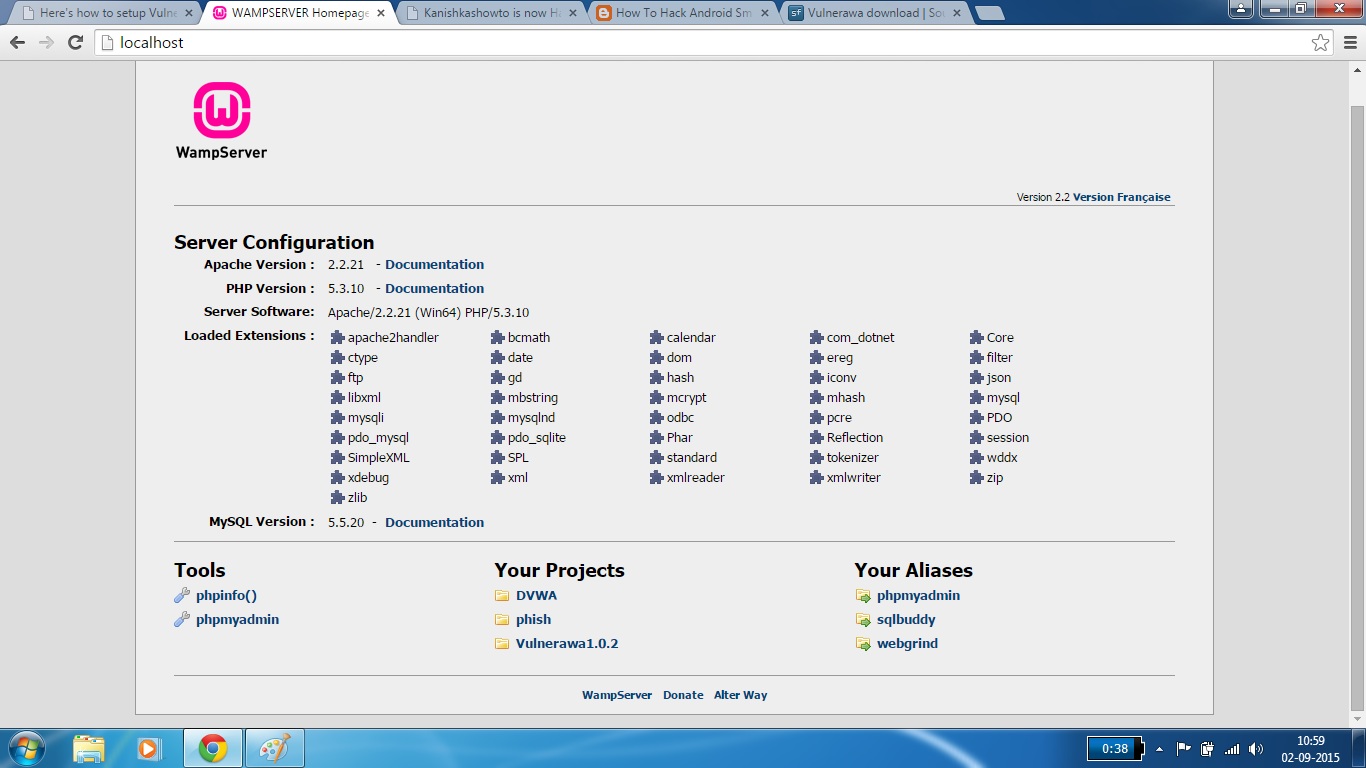
Now open your browser and type “localhost” once again. Now we can see our projectVulnerawa1.0.2 listed in the Projects section as shown below.
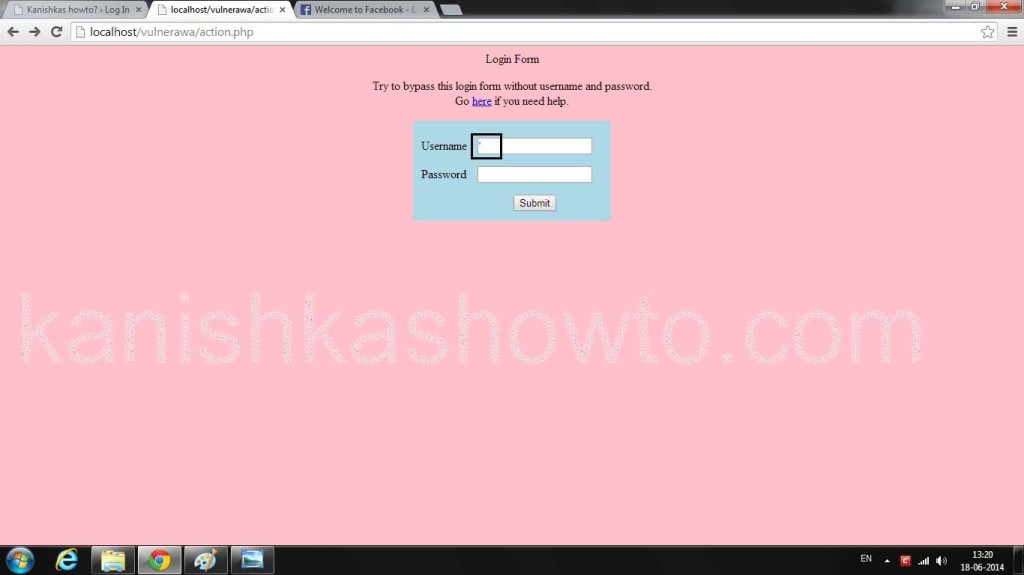
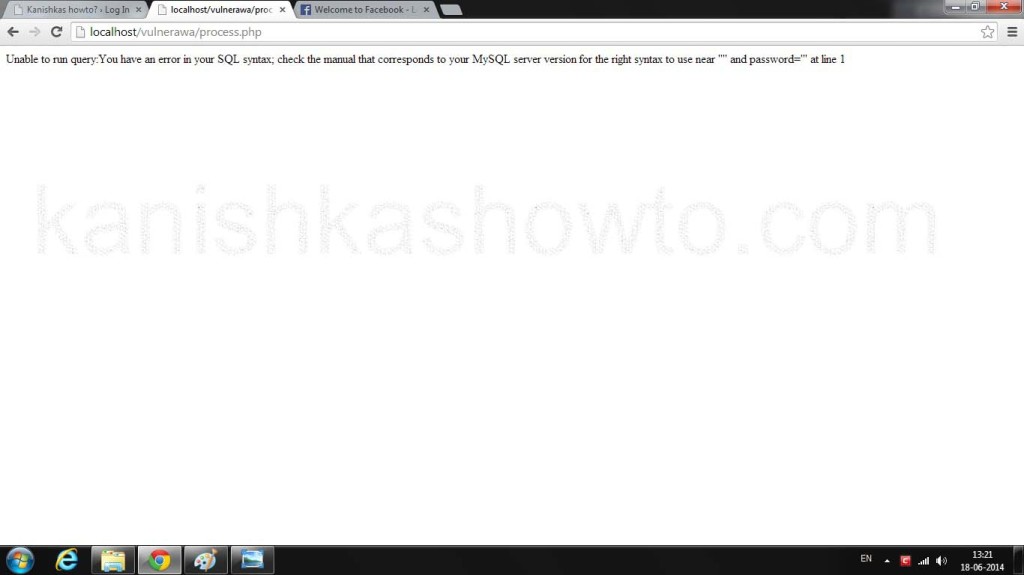
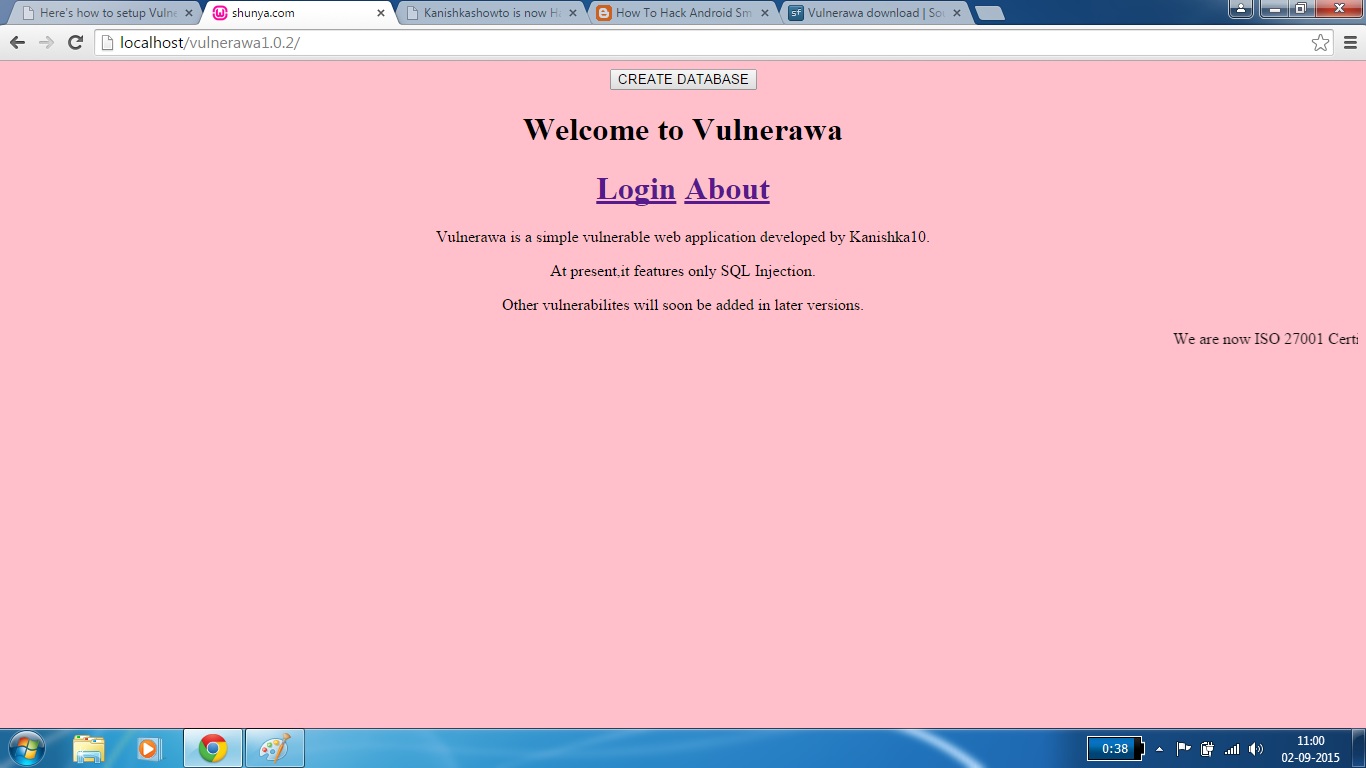
Click on the project. If you see the below webpage, then you have successfully setup Vulnerawa. If it gives you some error go to the url and type “http://localhost/vulnerawa1.0.2” directly. Happy hacking practice.
Here’s a video version of this howto.