Hello, aspiring ethical hackers. In this article, you will learn everything you need to know about Incident Response (IR). Unfortunately, unlike pen testing or ethical hacking, the role of incident response becomes important only after a cyber attack or any other cyber incident has occurred.
What is Incident Response (IR)?
In simple terms, incident response is how you or your organization respond to a cyber attack or a data breach that occurred in your organization. Obviously, any organization will want to respond to any cyber incident in such a way that the impact or damage due to that incident is minimized and contained.
So, IR is a planned and organized response of an organization to a cyber attack or incident.
Why is incident response important?
No matter how much security an organization has, there is no guarantee that a cyber incident may not occur. This cyber attack can damage the organization’s brand reputation, affect customers retention, damage intellectual property etc. A data breach can simply make a business run out of business.
IR aims to reduce this damage as quickly as possible. This requires a definite plan instead of ad hoc responses.
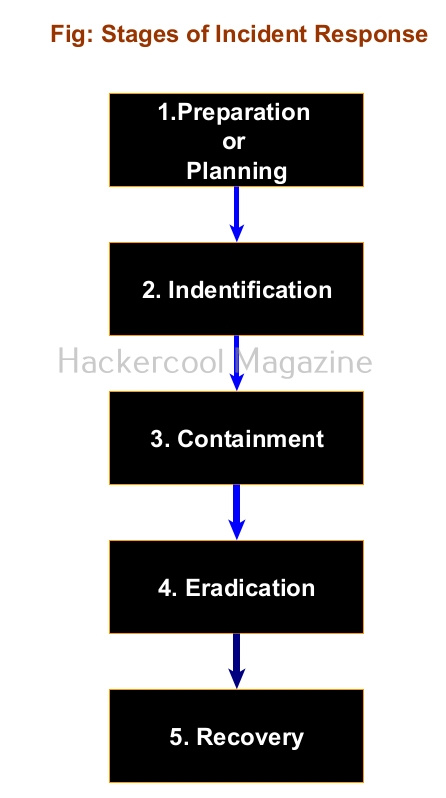
Stages of Incident Response
As I told you, Incident response should follow a planned and organized approach that should make the organization quickly recover from the impact of the cyber attack. Any good Incident response should have 5 steps. They are,
1.Preparation or Planning
Every organization should have a definite Incident response plan that caters to its requirements and depends on resources it wants to protect in its organization. This plan should be in written format. It should also have a dedicated incident response team that is not only aware of the incident response plan but also trained in it. This team should have the necessary tools and documentation ready in the case of a cyber attack.
2.Identification:
The next step is identifying the incident. In this era of false positives and false negatives, the incident response teams should be able to first determine what is a cyber attack to its organization. For example, let’s imagine an organization uses Windows XP machines in its organization. You know Windows XP machines are vulnerable to ms08-067.
Multiple SYN requests to SMB port of Windows XP machines of an organization may raise shackles but it is not yet an incident. But somebody exploiting the vulnerability to gain a shell or creating a new user account on that Windows XP machine can be termed as an incident.
3.Containment:
Once an incident has been identified correctly, the next step should be to limit and prevent further damage. The infected resource should be isolated and steps taken to ensure that customers or employees don’t experience any problems in accessing the resource.
Going with the same example we gave above, the infected Windows XP machine should be isolated so that the infection can be prevented from spreading to other devices on the network. In some cases, the network traffic needs to be rerouted or redirected. Once isolated, the forensics team should be informed so that it can perform digital forensics to further investigate the incident.
4.Eradication:
After the infected system or resource is isolated and the forensics team is done with creating forensic images of the infected system, the next step is the removal and restoration of systems affected by the security incident. For example, this stage involves fixing the ms08-067 vulnerability and removing the malware or payload, backdoors from the infected system. The important role of this stage is to make sure that the system cannot be exploited again.
5. Recovery
This stage involves bringing the infected system back into production environment and to make sure that another incident doesn’t occur. Before the infected system is brought back into production again, they are tested, monitored, validated and cleansed of all malware.
All of the above steps should be written in policy plan and should be documented. That’s all about Incident response. Next, learn how to prevent your organization from being hacked with threat intelligence.
Follow Us