Hello, aspiring ethical hackers. In this blogpost, you will learn about cryptography or in the cybersecurity sense about encryption. The word cryptography came from a Greek word kryptos which means “hidden secret” and it plays a very important role in cybersecurity.
What is cryptography?
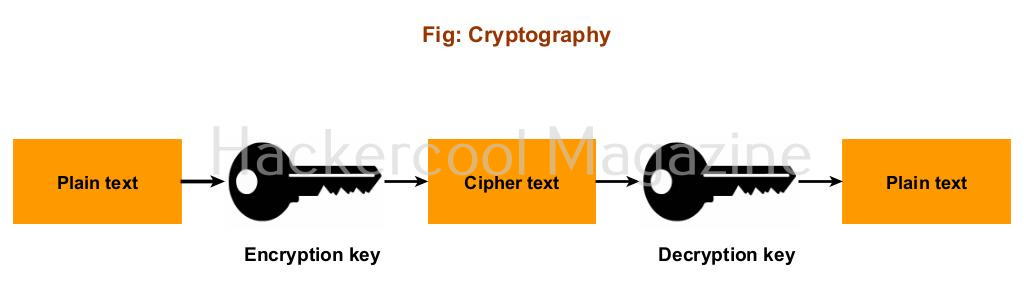
Cryptography is the study of secure communication techniques. It is closely associated with encryption which is an act of taking an ordinary text and scrambling it to transform it in to cipher text. The aim of this encryption is to make sure that the message is only understood by someone which it is intended to.
Types of Cryptographic techniques
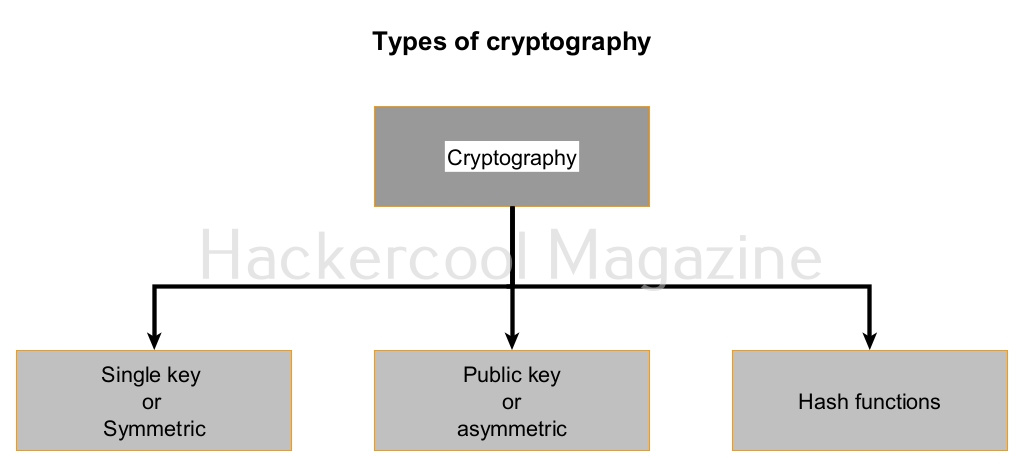
There are three types of cryptographic techniques. They are,
- Single key cryptographic system (Symmetric encryption)
- Public key cryptographic system (Asymmetric encryption)
- Hash Functions.
What is a cryptographic key?
A cryptographic key is a string of characters used with an encryption algorithm to transform data into a scrambled form or cipher text.
What is an encryption algorithm?
An encryption algorithm is the method used to transform plain text to cipher text.
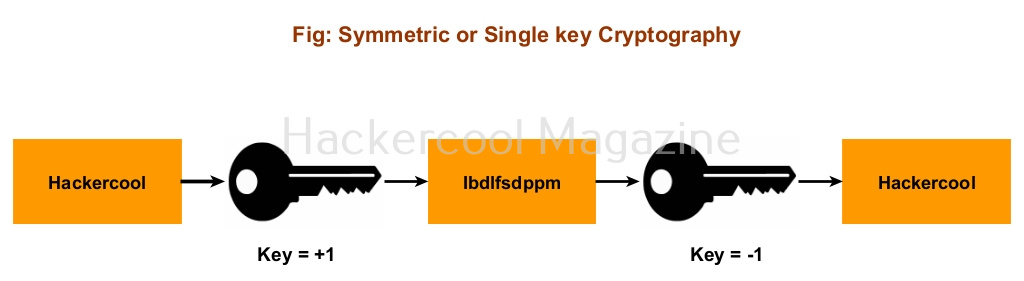
1. Symmetric encryption (Single key cryptographic system)
In symmetric encryption, a single key is used to both encrypt and decrypt data.
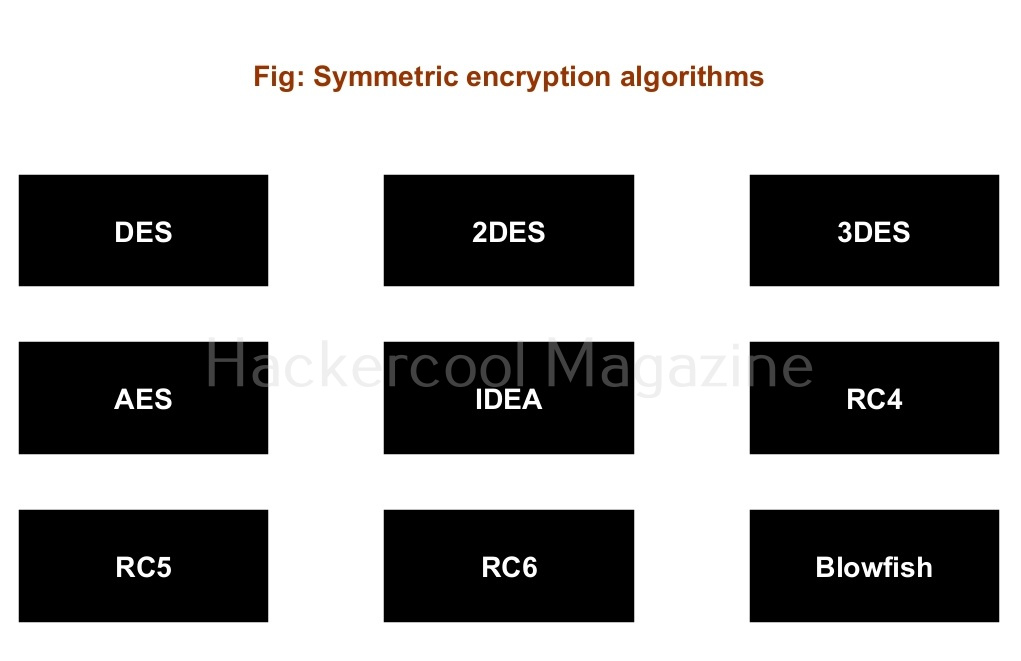
Hence it is known as single key cryptographic system. Symmetric encryption is very fast and hence used wherever speed is required for encryption. For example, it is used for encrypting credit card information and other confidential information, making malware and virus Fully Undetectable (FUD) etc. There are various encryption algorithms. The most popular encryption algorithms are DES, 2DES, 3DES, AES, IDEA, RC4, RC5, RC6, Blowfish etc.
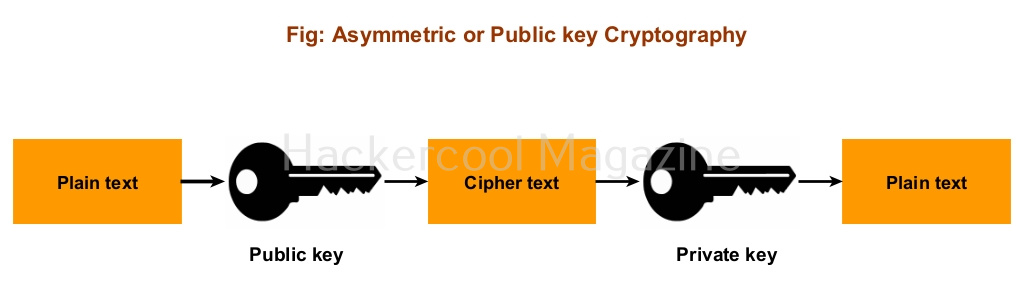
2. Public key cryptographic system or asymmetric encryption (PKCS):
Also known as asymmetric encryption, Public key cryptographic system (PKCS) uses two keys: Public key and Private key. The data is encrypted with the Public key and can only be decrypted with private key or vice versa.
Since two different keys are used for encryption and decryption, even if any attacker knows about the key used for encryption there is no threat to any data. It is more secure than the single key cryptographic system but a bit slow. This is used in online communications like HTTPS, digital signatures etc. Example of Public key cryptography system algorithms are RSA, Diffie-Hellman etc.
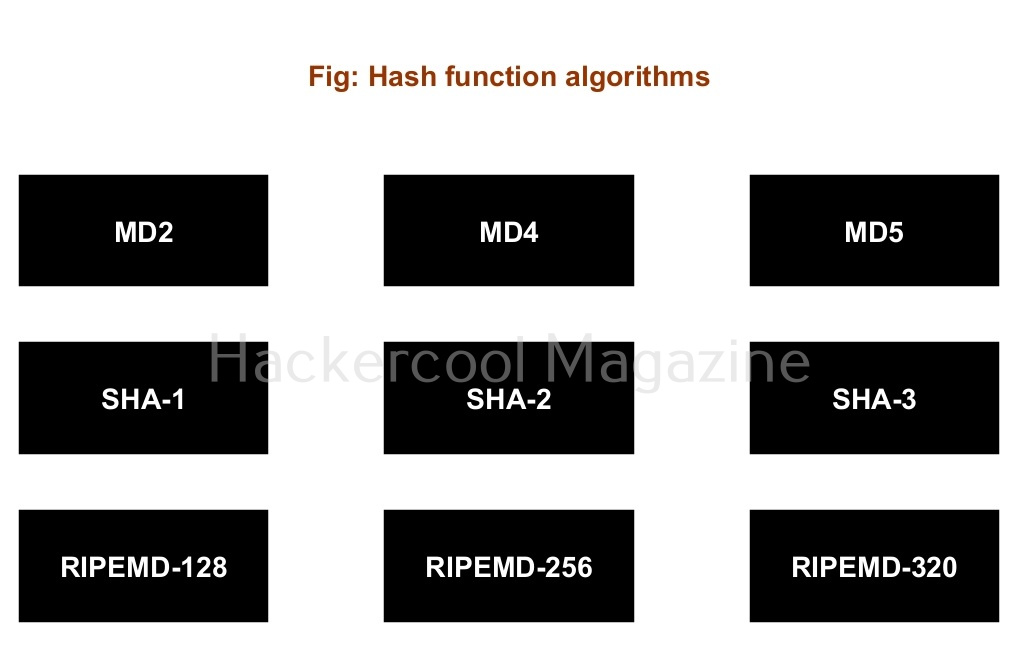
3. Hash Functions or Message Digests:
A hash function is a versatile one-way cryptographic algorithm that converts plain text to a fixed length of encrypted text which is known as a message digest or simply a hash. A hash is known as a one-way function since once it encrypted it cannot be decrypted but (or decrypting it is very complex and difficult). Hash functions and message digests are used whenever the decrypting is not needed like hashing the passwords etc. Example of hash functions are MD5, SHA-1, SHA-512, RIPEMD etc.
Follow Us