Hello aspiring Ethical Hackers. In our previous blog post, you learnt what is Footprinting, why it is important and different types of Footprinting techniques. In this blog post, you will learn about performing Footprinting using Metadata.
What is Metadata?
Metadata is a set of data that provides information about other data. Simply put, it is data about the data. Everyone knows data is very important but metadata is often ignored but equally important. But how is metadata helpful to Ethical Hackers. Before going there, let us see how to extract Metadata.
How to extract Metadata?
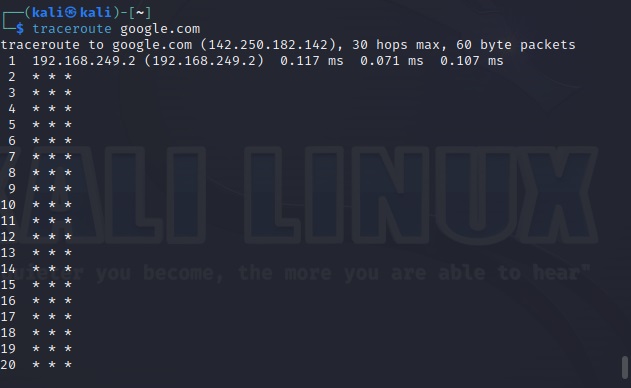
There are various tools and online resources that extract metadata from different files. For this article, let’s use one tool that is inbuilt in Kali Linux, exiftool. Exiftool extracts metadata from a number of file types.
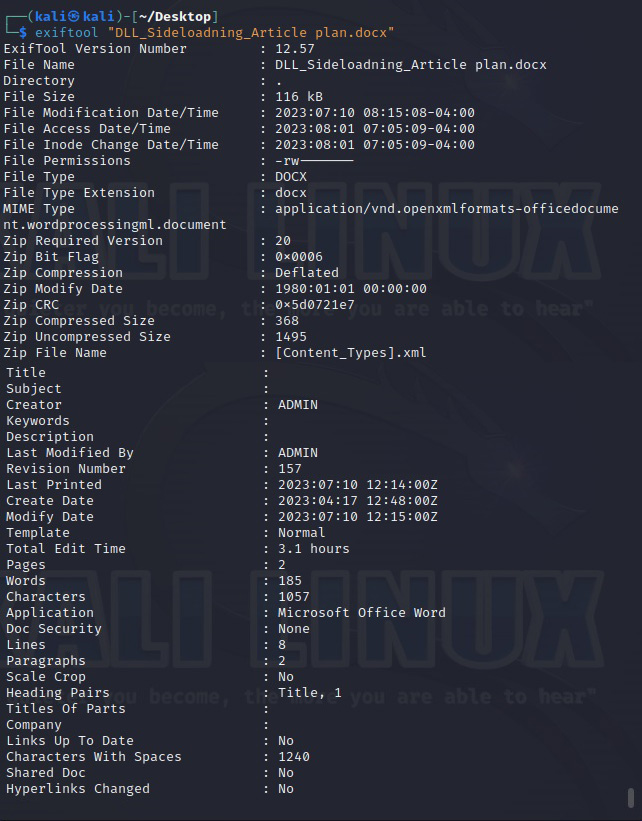
Let’s extract metadata of a docx file.
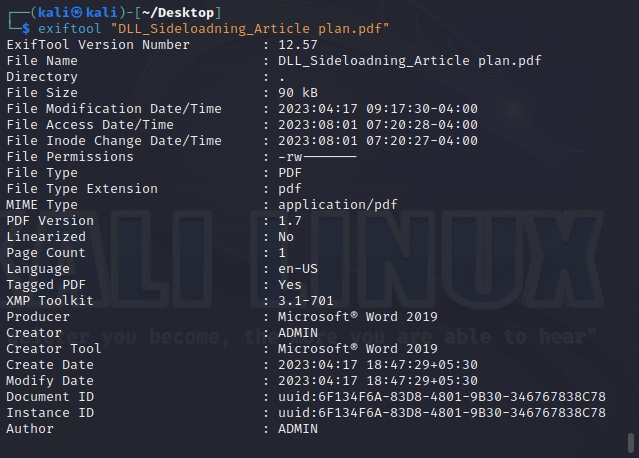
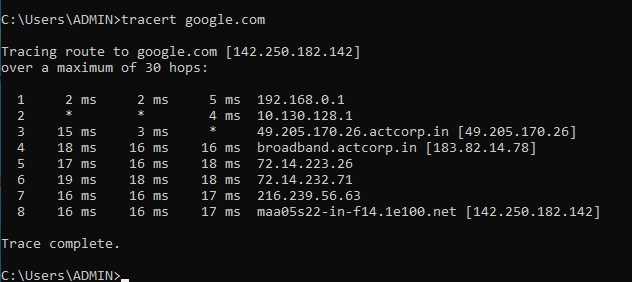
Now, let’s extract it from a PDF file.
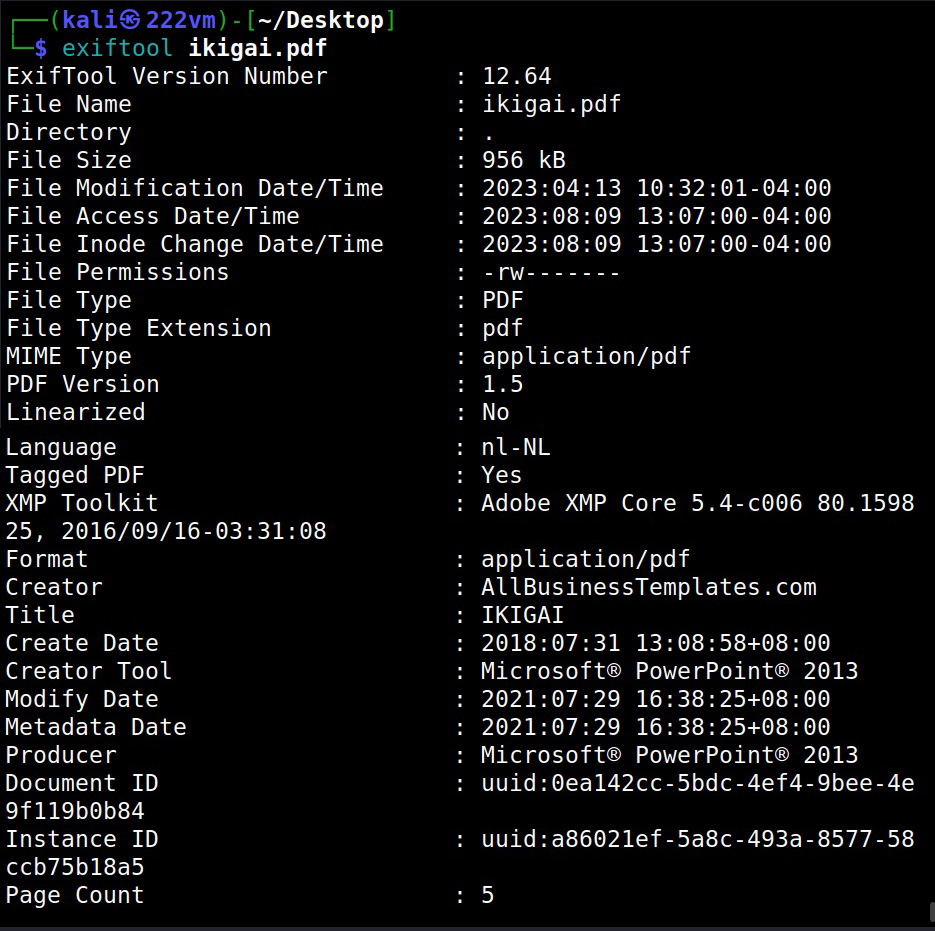
Let’s see another PDF file.
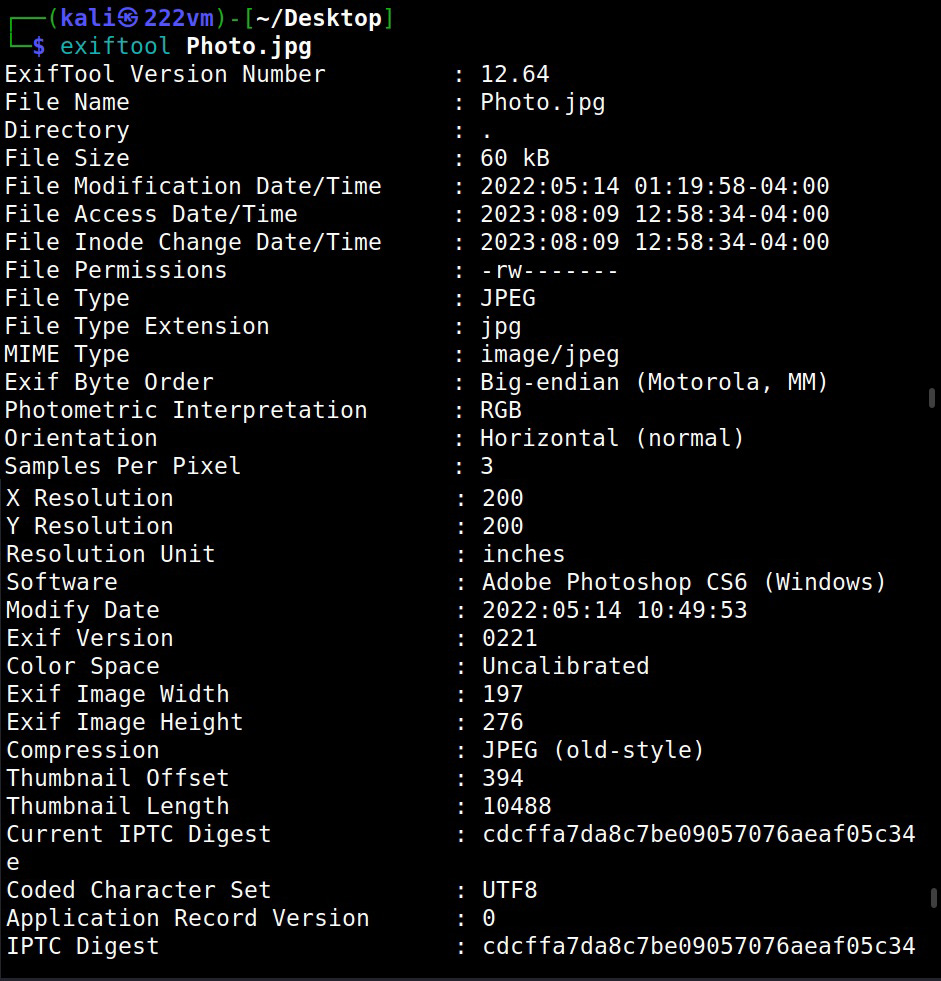
Last and final, let’s use it on an image file.
How is it useful in pen testing?
If you have noticed, we have performed metadata extraction from 3 types of files: Docx, PDF and an Image. That’s because these are the most common types of files that are available online. Any organization uses these types of files on their websites or anywhere else to convey information.
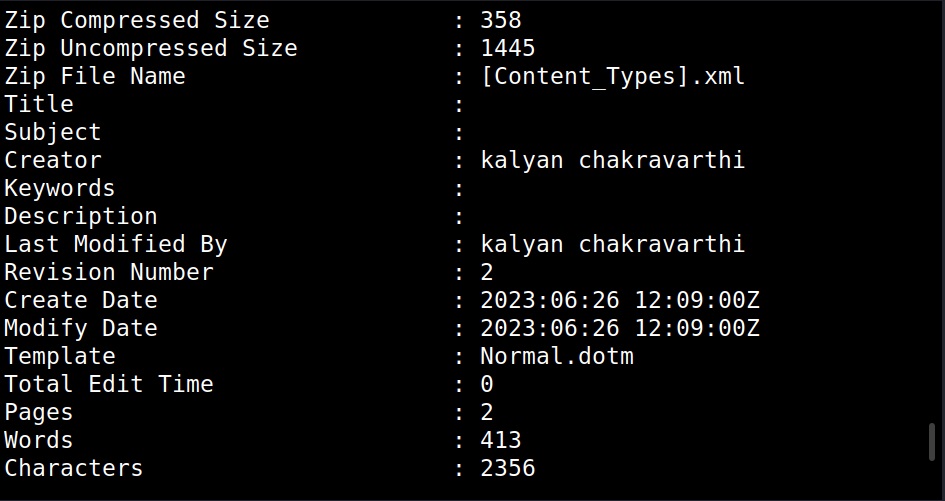
While extracting information of the docx file revealed the names of creators of the file (Admin, Kalyan). This revelation can help in gaining access later (i.e username is admin etc) or to perform a spear phishing attack targeted at the target user. We can also see that the document was created using Microsoft Word software. So, we can target these users with a malicious macro attack.
While observing the information extracted from a PDF file, we can see that this PDF was created using Microsoft Word. In this case, the version of the MS Word software is also very clear (2019) along with the creator’s name.
The second PDF file was created using Microsoft PowerPoint. So, we can figure out that these users need to be targeted with PowerPoint attack.
Images are another most common types of files found on a website or any other company’s property. We can see that the image I downloaded from a website is either edited or created with Photoshop along with its specific version. So, we can search for any vulnerabilities in this particular software or use this software themed lure to target this organization.
That’s how Metadata can help Pen testers in gaining information about the target organization.