Hello, aspiring Ethical Hackers. In our previous blogpost of Footprinting guide, you learnt about various techniques of Footprinting. In this blogpost, you will learn about DNS Footprinting which is one of the techniques of Footprinting. But first, what is DNS? DNS stands for Domain Name Service. In simple terms, DNS is like translation service between humans & browsers. Why do I say so?
Let me explain you. You open a browser and type a domain name (ex:hackercool.com) to visit a website. Web browsers have no idea about this domain name or for that matter any domain name because web browsers communicate with servers through Internet Protocol addresses. Then how web browsers take you to the website you want. Thanks to DNS (Domain Name Service) translates domain names to IP addresses. Lean more about how DNS works here.
What is DNS Footprinting?
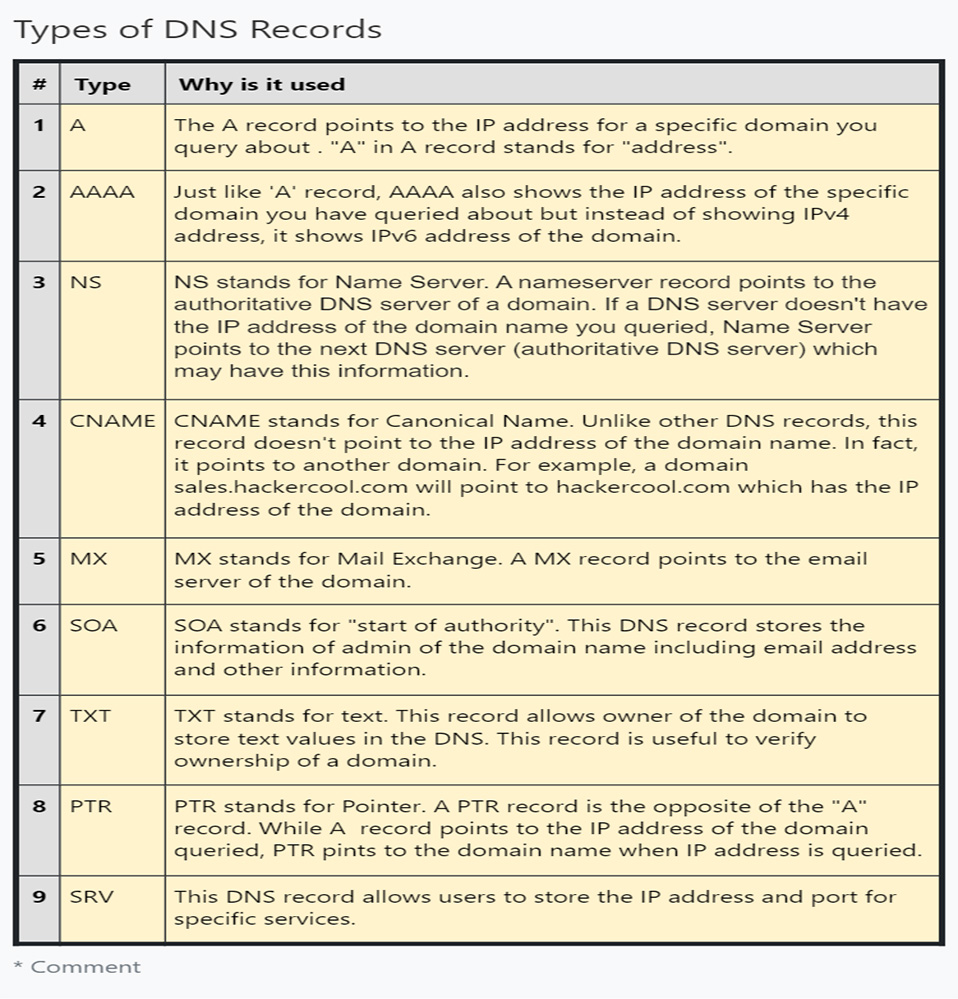
DNS Footprinting is a technique in which attackers gather DNS information about the target system. A DNS server stores information such as DNS domain names, computer names, IP addresses and other network related information. It also has some records that are important. Here are the types of records a DNS server can have.
How does it help in Pentesting?
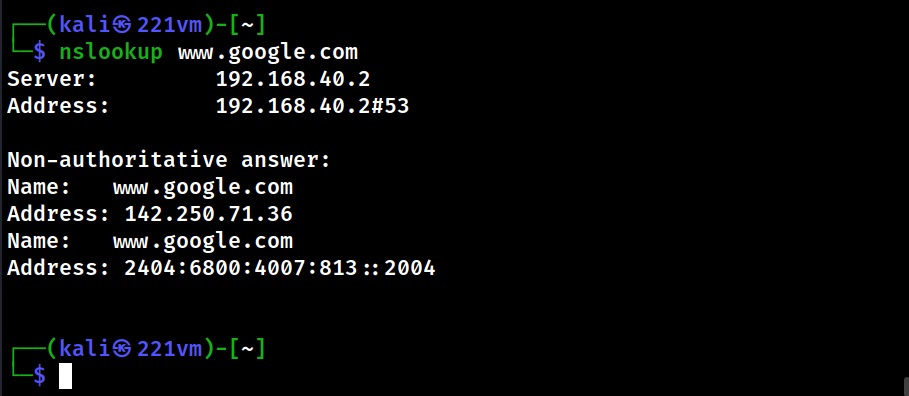
DNS Footprinting can reveal other information about server related to the network and in some cases expose entire Zone data. DNS Footprinting is very simple. Let’s show you two tools popular for DNS footprinting. The first tool is nslookup. Here’s how to use nslookup to query about a domain.
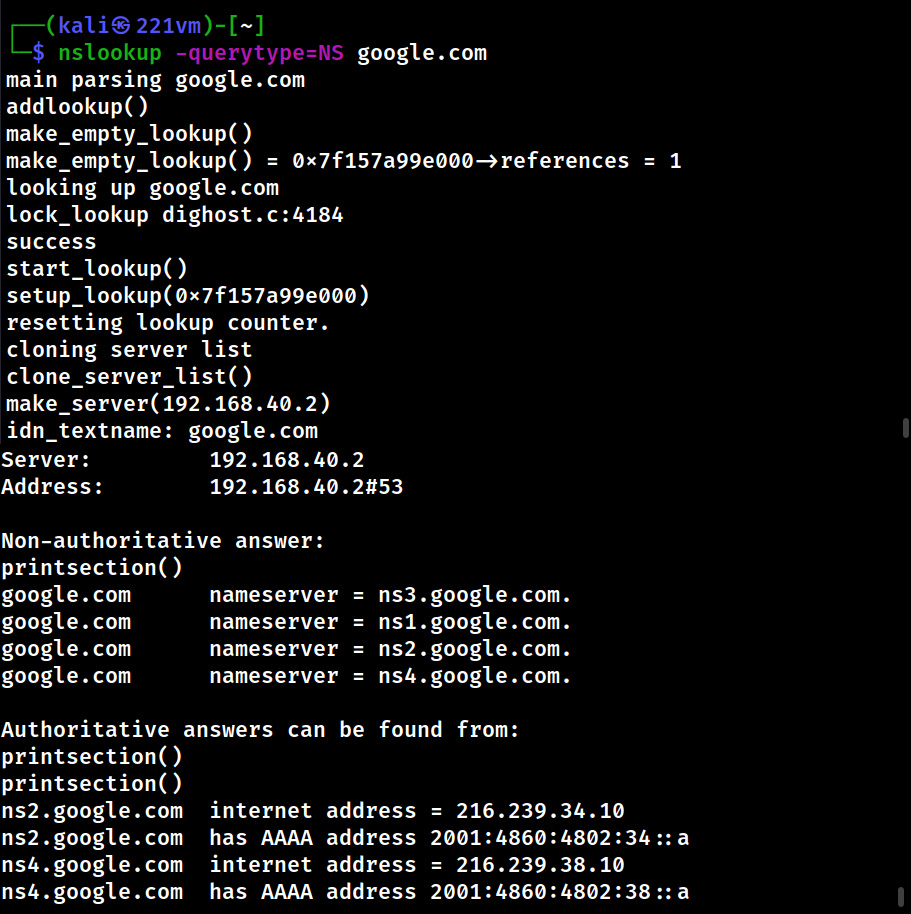
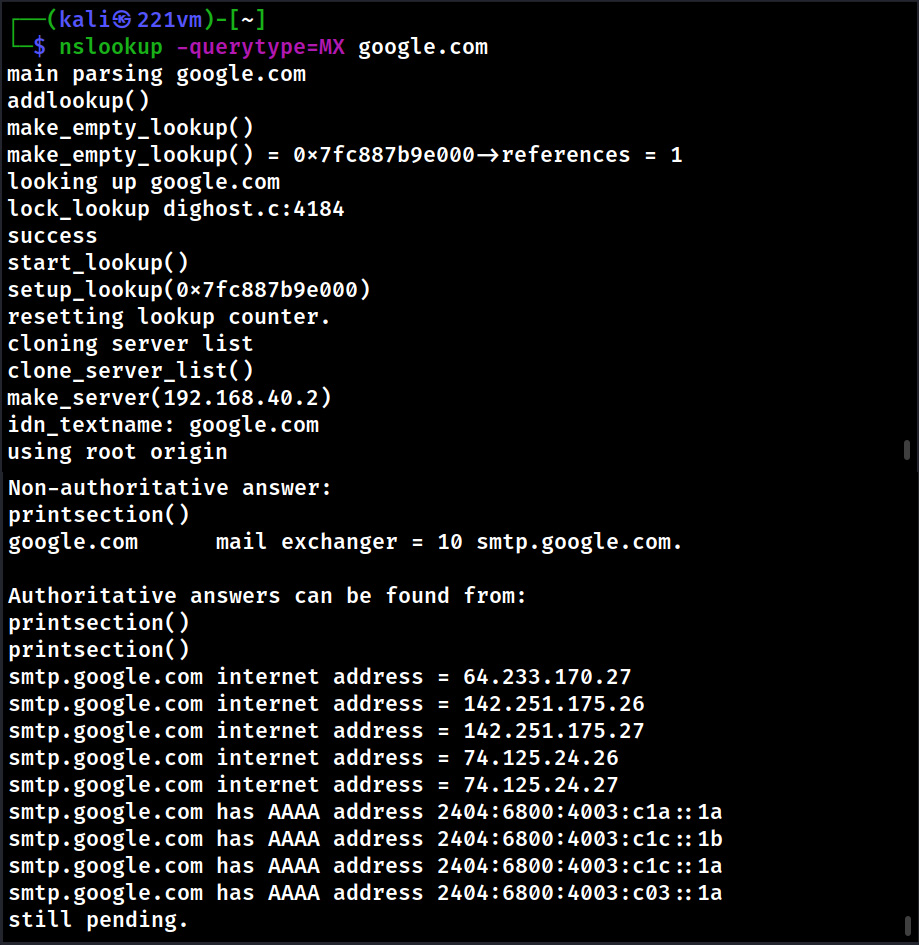
We can even query for a specific type of record using nslookup. Let’s query specifically for “NS” and “MX” records.
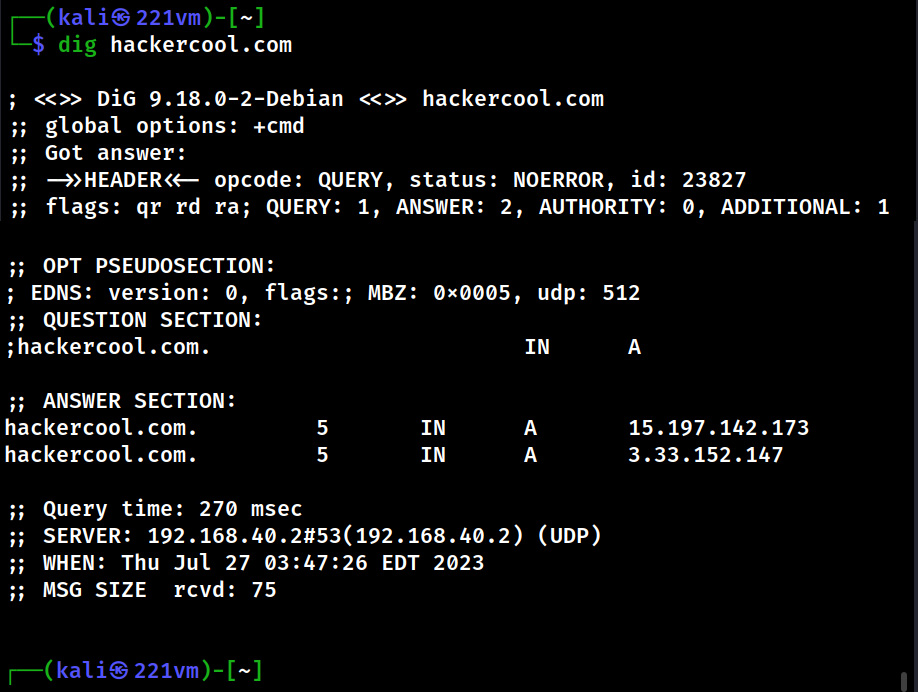
There is another tool named DIG that can be used for DNS lookup.
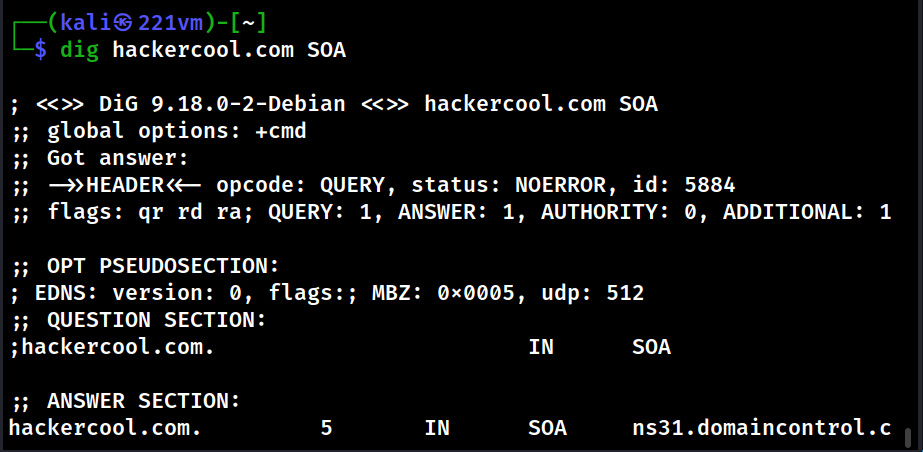
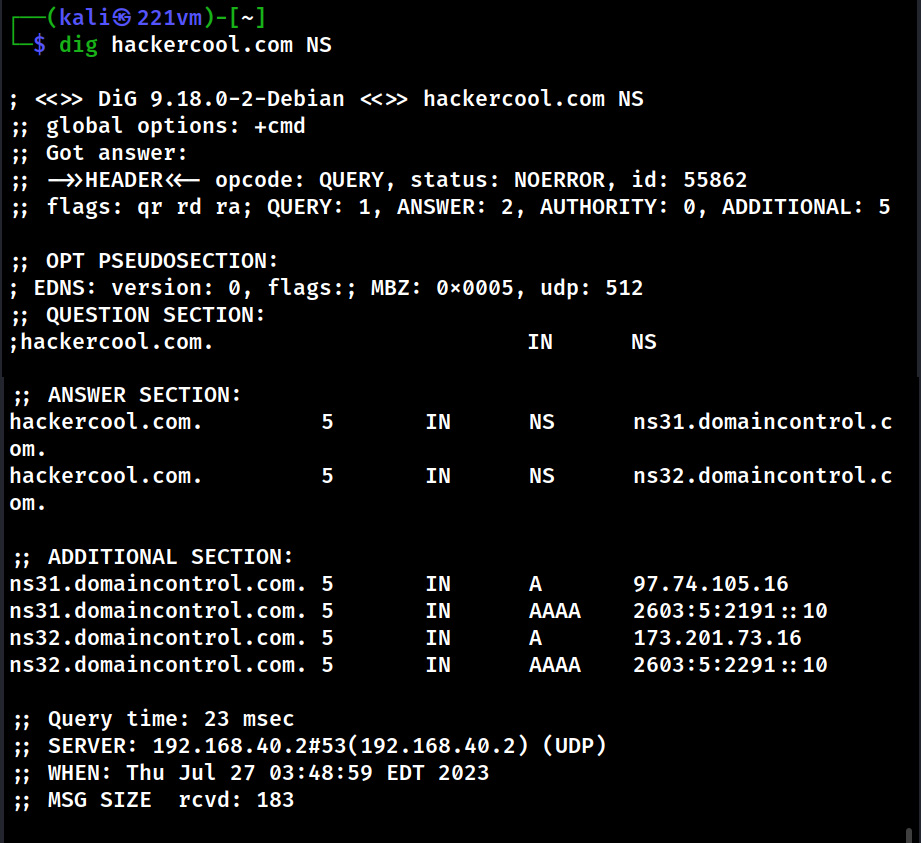
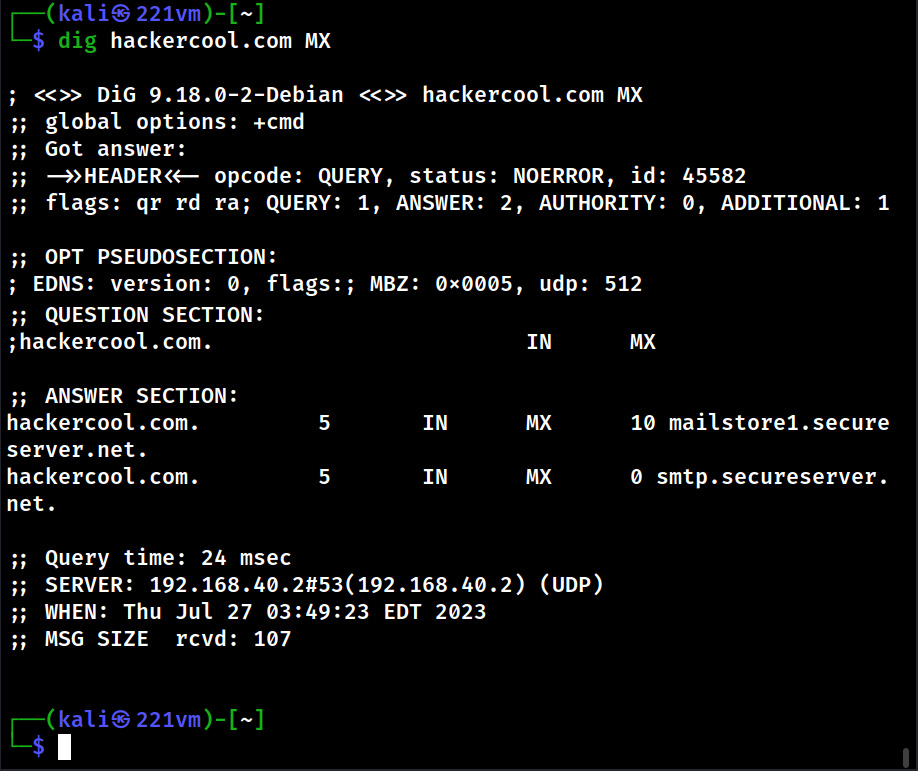
This tool can also be used to query for a specific type of records as shown below.
Follow Us