Kali Linux is the most advanced penetration testing distribution with a number of tools. While using these tools a measure of anonymity is required. Today we are going to see how to spoof your IP address in Kali Linux. First, check your IP address by visiting any website which shows your IP address (http://www.whatismyip.com). Then go to the site www.vpnbook.com.
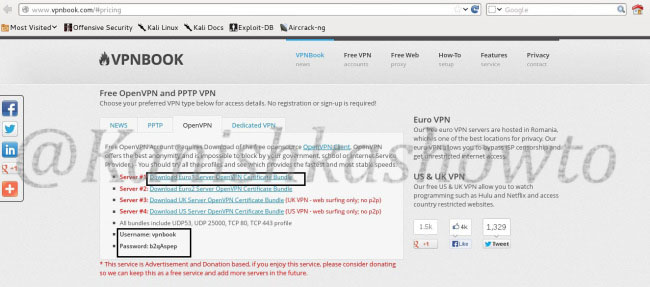
Download the Euro1 Server OpenVPN certificate bundle as shown below. Note down the username and password given. We will need it in later steps.
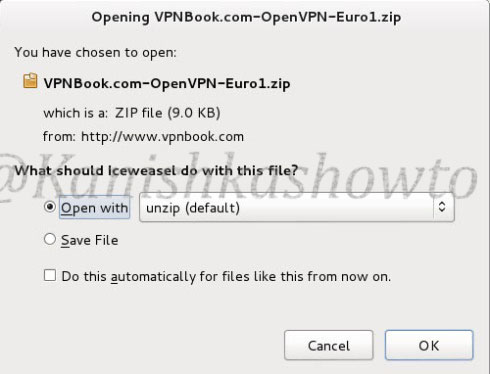
When you click on the download link, the following window opens. Since it is a zip package, system will prompt whether to open it with unzip ( the default option ). Click on “OK”.
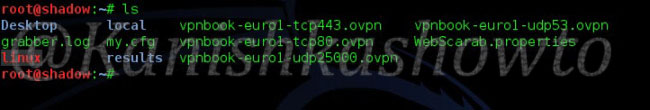
Open the terminal and navigate to the directory where the contents of the zip archive have been unzipped. Type the command “ls” to see the unzipped files. We are going to use the vpnbook-euro1-udp53.ovpn package.
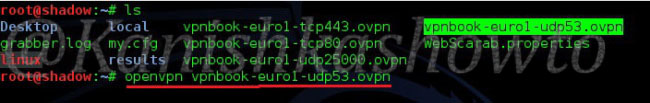
OpenVPN has been installed by default in the Kali Linux distribution. Type the command “openvpn vpnbook-euro1-udp53.ovpn” to start the process.
The installation starts. Enter the username and password we noted above when prompted.
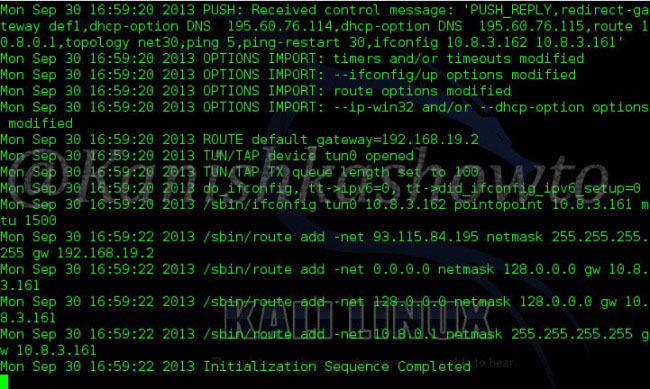
After a short time, the process is completed. Check your IP address again. If everything goes well, your IP address will be changed.
Follow Us

I Don’t think you can run it in a VM, I Know if you have kali installed as your prim sys then any VM will use then vpn automatically, If you don’t won’t to install kali on your hard drive I would try installing vpnbook on your prim system like windows and your VM should use the vpn by default, it’s that the vpn has to be ran on the machine that connects to the internet….
You made some good points there. I looked on the net to find
out more about the issue and found most individuals will go
along with your views on this site.
Thanks you i’m french !
root@probook:~/Downloads/VPNBook.com-OpenVPN-Euro1# openvpn vpnbook-euro1-udp53.ovpn
Wed Feb 10 16:21:38 2016 OpenVPN 2.3.10 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH] [IPv6] built on Jan 21 2016
Wed Feb 10 16:21:38 2016 library versions: OpenSSL 1.0.2f 28 Jan 2016, LZO 2.08
Enter Auth Username: ****
Enter Auth Password: ****************
Wed Feb 10 16:21:44 2016 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Wed Feb 10 16:21:44 2016 Socket Buffers: R=[212992->212992] S=[212992->212992]
Wed Feb 10 16:21:44 2016 UDPv4 link local: [undef]
Wed Feb 10 16:21:44 2016 UDPv4 link remote: [AF_INET]176.126.237.217:53
Wed Feb 10 16:21:45 2016 TLS: Initial packet from [AF_INET]176.126.237.217:53, sid=c4c4a34a 0cc8deb5
Wed Feb 10 16:21:45 2016 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Wed Feb 10 16:21:45 2016 VERIFY OK: depth=1, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, [email protected]
Wed Feb 10 16:21:45 2016 VERIFY OK: depth=0, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, [email protected]
Wed Feb 10 16:21:45 2016 Data Channel Encrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Wed Feb 10 16:21:45 2016 Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Wed Feb 10 16:21:45 2016 Data Channel Decrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Wed Feb 10 16:21:45 2016 Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Wed Feb 10 16:21:45 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Wed Feb 10 16:21:45 2016 [vpnbook.com] Peer Connection Initiated with [AF_INET]176.126.237.217:53
Wed Feb 10 16:21:48 2016 SENT CONTROL [vpnbook.com]: ‘PUSH_REQUEST’ (status=1)
Wed Feb 10 16:21:48 2016 AUTH: Received control message: AUTH_FAILED
Wed Feb 10 16:21:48 2016 SIGTERM[soft,auth-failure] received, process exiting
I HAVE THIS PROBLEM ANYONE FOR HELP ?!