Hello, aspiring ethical hackers. In this blogpost, you will learn about covering tracks which is the last of the 5 phases of ethical hacking.
What is Covering tracks?
Covering tracks or clearing tracks is the phase of ethical hacking in which a hacker tries to erase all the evidence on the target system that can lead back to the hacker. For covering tracks, hackers perform various actions. They are,
1. Uninstalling executables and scripts:
Hackers install many scripts and executables on the target system as part of their hacking attack. These scripts may help hackers cracking passwords, privilege escalation, maintaining access etc. Detection of these scripts and executables on the target system can lead the investigators to the hacker. So, hackers uninstall or delete any scripts or executables they have used in carrying the hacking attack.
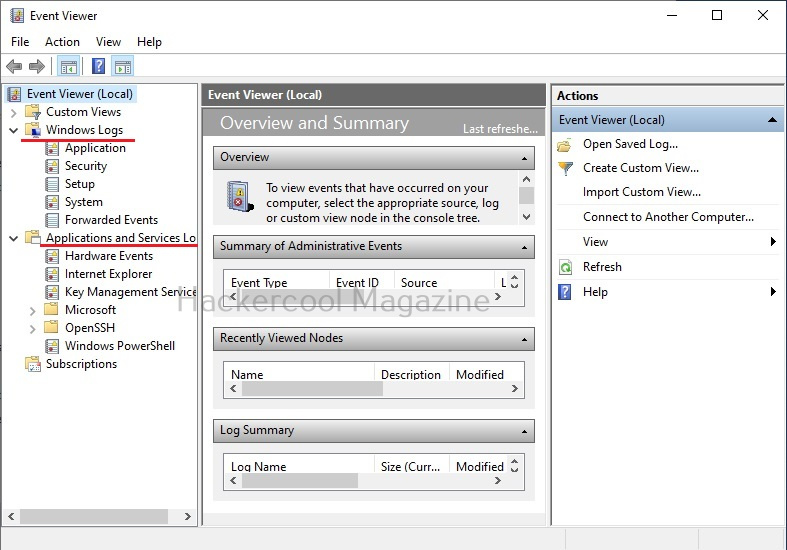
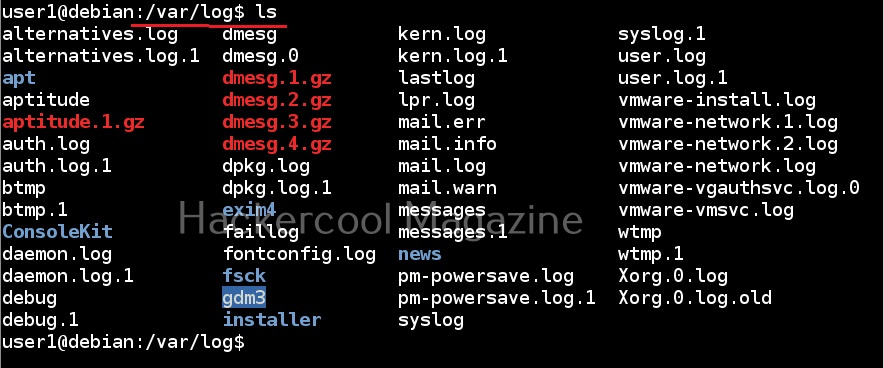
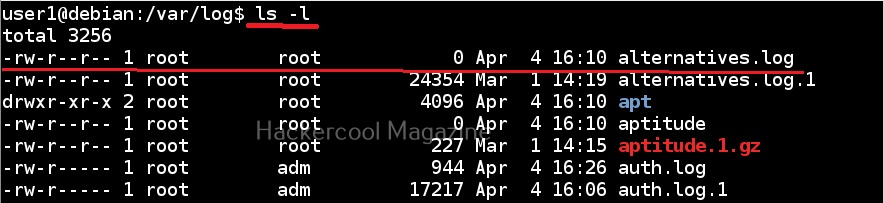
2. Clearing logs:
Every operating system has its own logs that record different operational activities being performed on the operating system. They also record any actions performed by hackers. When an incident investigator observes these logs, he can easily deduce what the hacker did on the target system. To prevent this, hackers clear these logs to hide whatever they did on the target system.
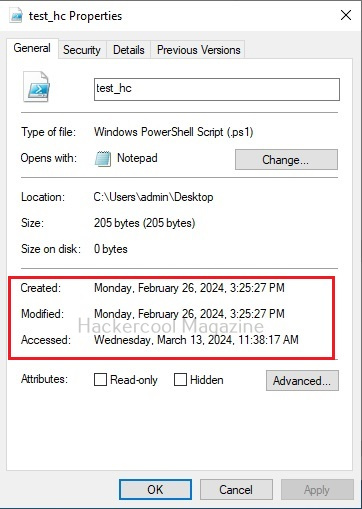
3. Timestamping files:
Every file on the operating system has a time stamp which reveals information about the file like the date of its creation, last modified time etc. Hackers change this timestamp of the files appropriately to prevent detection of the modifications they made to files inadvertently while hacking.
4. Modifying registry values:
The Windows Registry in the Windows operating system is a hierarchical database that contains information, settings, options, and other values for programs and hardware installed on the Windows operating system. Changes made to some program can also be detected by viewing this registry. So, hackers also modify these registry values to hide their malicious activity.
Follow Us