Hello aspiring Computer Forensic Investigators. This article is the second part of performing Digital Forensics with Autopsy. Read the first part here. So let’s continue answering the questions presented by the case.
11. When was the last recorded computer shutdown date/time?
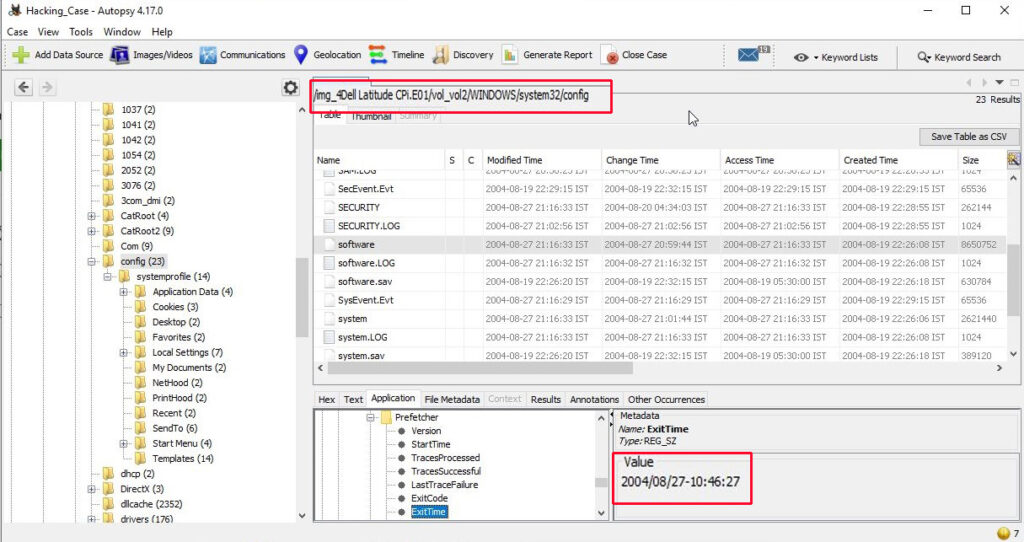
The last recorded shutdown date and time can be found out in the following file in Windows.
“C:\WINDOWS\system32\config\software\Microsoft\WindowNT\CurrentVersion\Prefetcher\ExitTime”
The shutdown date and time is 2004/08/27 10:46:27.
12. List the network cards used by this computer?
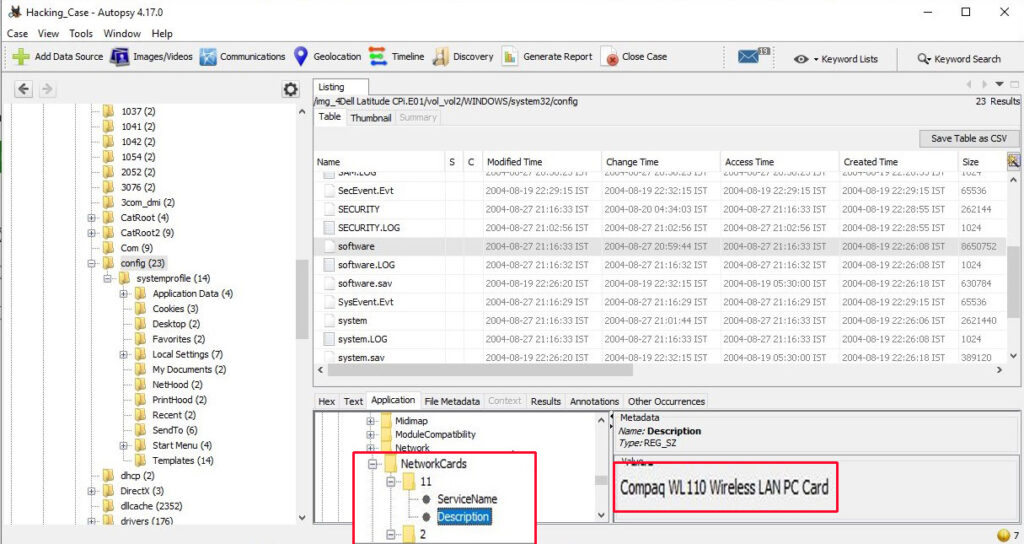
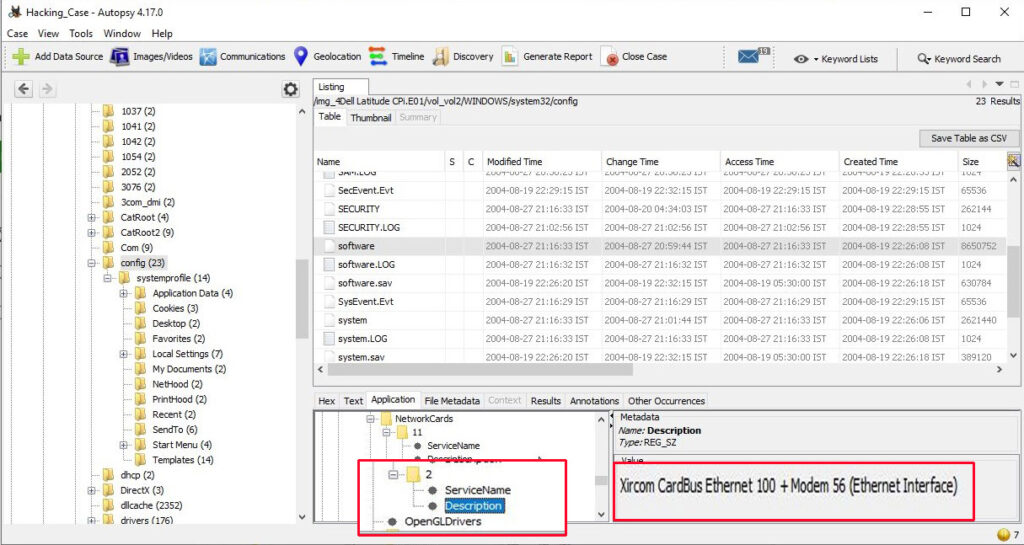
The information about the network cards on this computer can be found in the Windows file “C:\WINDOWS\system32\config\software\Microsoft\WindowNT\CurrentVersion\NetworkCards”
There are two network cards on this system. One is a Compaq WL 110 Wireless LAN PC Card and another is Xircom CardBus Ethernet 100 + Modem 56 (Ethernet Interface).
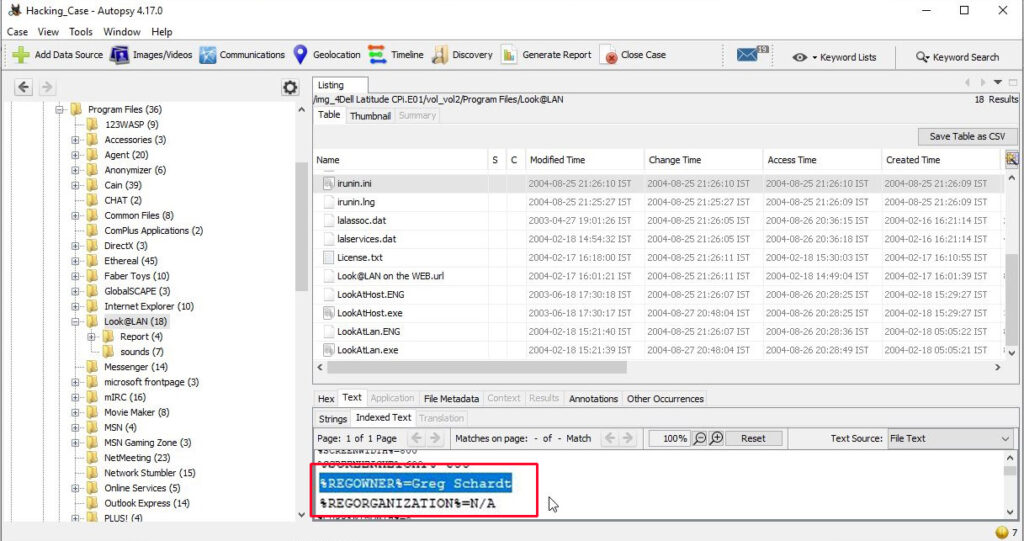
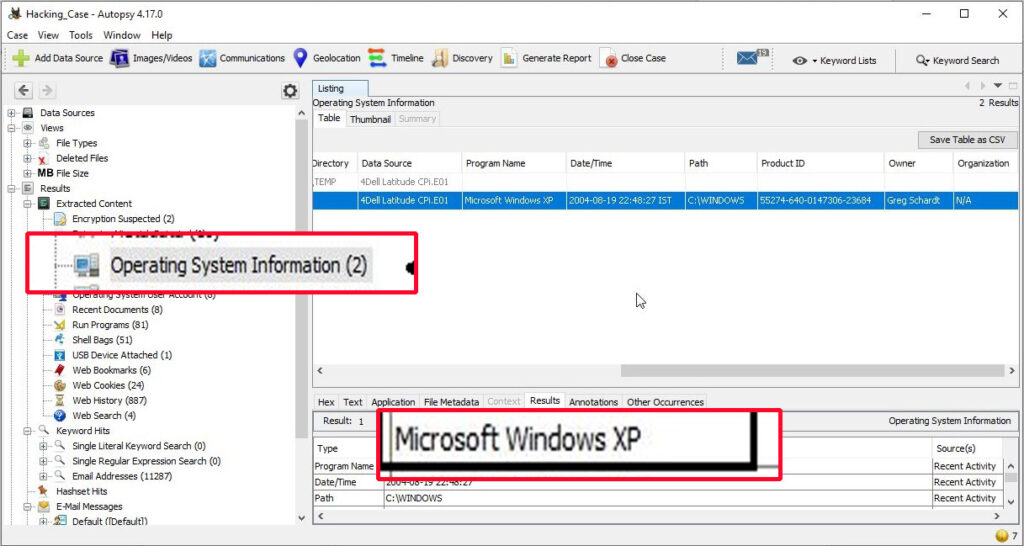
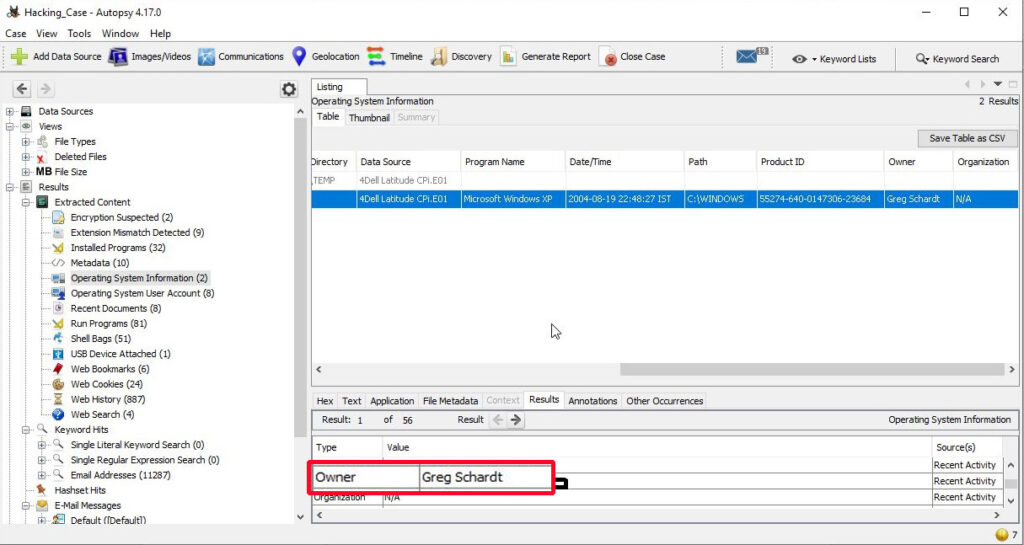
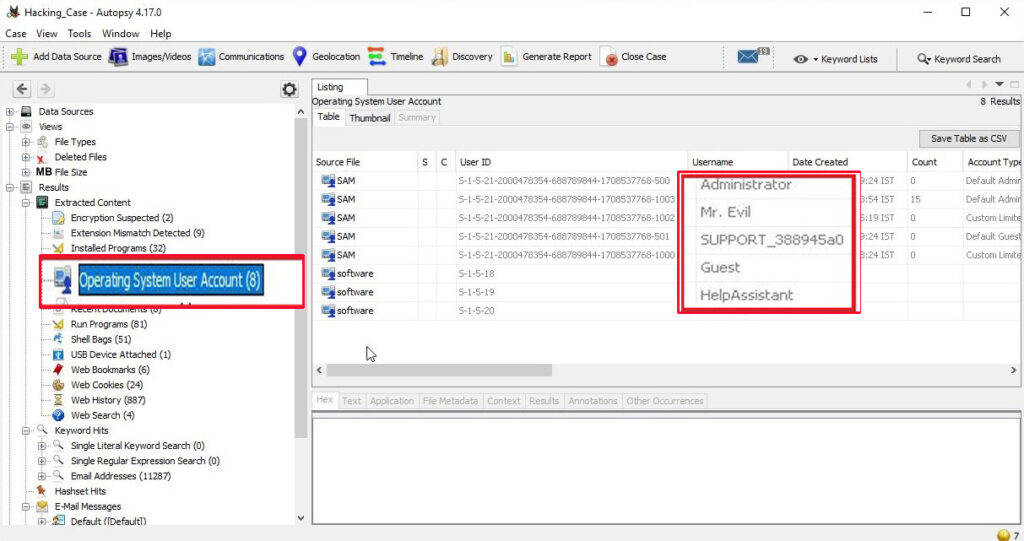
13. A search for the name of “G=r=e=g S=c=h=a=r=d=t” (The equal signs are just to prevent web crawlers from indexing this name; there are no equal signs in the image files) reveals multiple hits. One of these proves that G=r=e=g S=c=h=a=r=d=t is Mr. Evil and is also the administrator of this computer. What file is it? What software program does this file relate to?
The file that reveals all this information is “C:\Program Files\Look@LAN\irunin.ini”
his file belongs to the program Look@LAN.
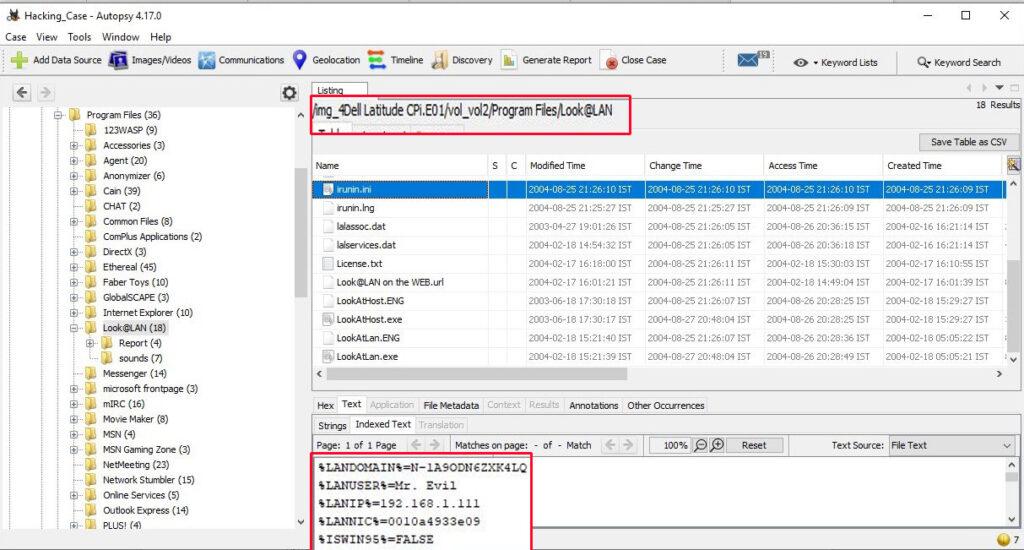
14. This same file reports the IP address and MAC address of the computer. What are they?
The IP address of this machine is 192.168.1.111 and the MAC address is 0010a4933e09. The LAN user is Mr. Evil. This confirms that Mr. Evil and Greg Schardt are one and the same.
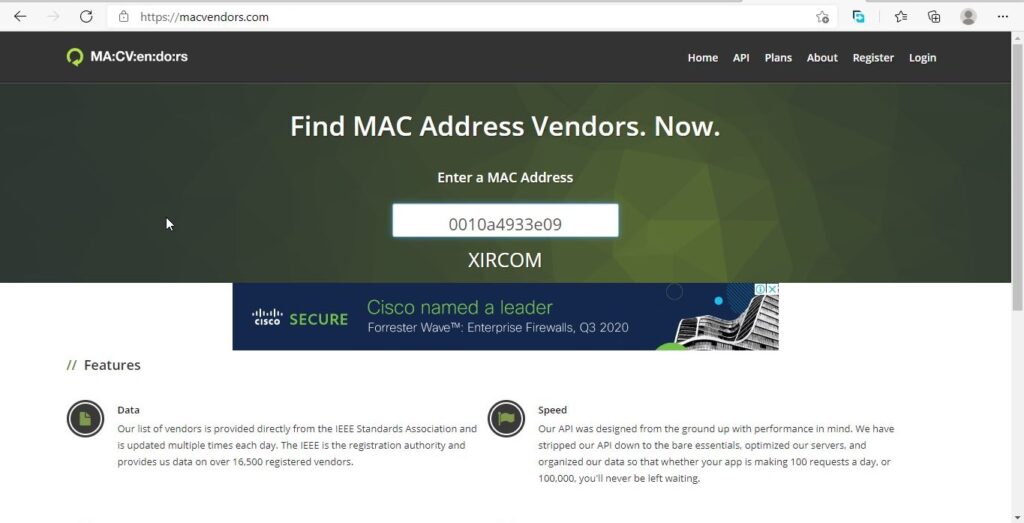
15. An internet search for vendor name/model of NIC cards by MAC address can be used to find out which network interface was used. In the above answer, the first 3 hex characters of the MAC address report the vendor of the card. Which NIC card was used during the installation and set-up for LOOK@LAN?
Media Access Control (MAC) address or the physical address is a 12 digit hexadecimal number hardcoded to the NIC card. The first 3 hexadecimal characters reveal the vendor of the NIC card. There are many websites which offer this service of knowing the vendor of the NIC card. Pasting the MAC address of the computer reveals the vendor.
The Vendor of this NIC card is XIRCOM.
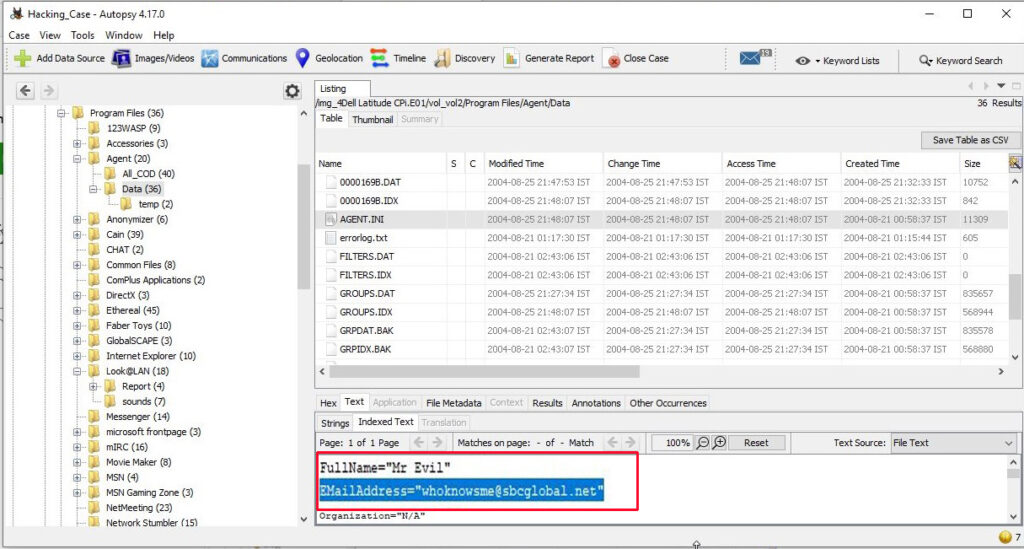
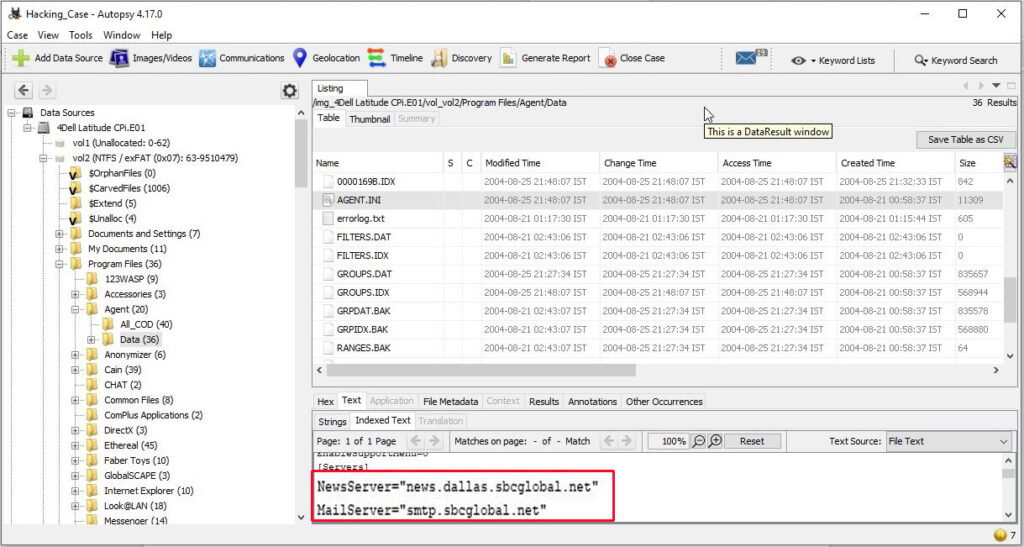
16. What is the SMTP email address for Mr. Evil?
SMTP or Simple Mail Transfer Protocol is a protocol used to send emails. The SMTP email address if present on the system can be found in “C:\Program Files \Agent\Data\AGENT.INI file”.
The SMTP email address is “[email protected]”.
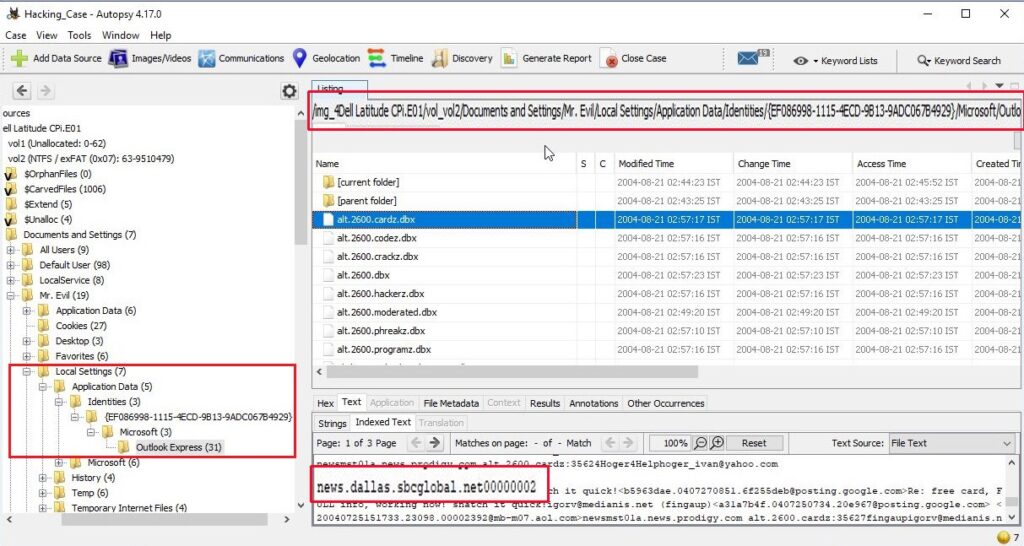
17. What are the NNTP (News Server) settings for Mr. Evil?
This information can be found in the same file as above.
The news server being used is “news.dallas.sbcglobal.net”.
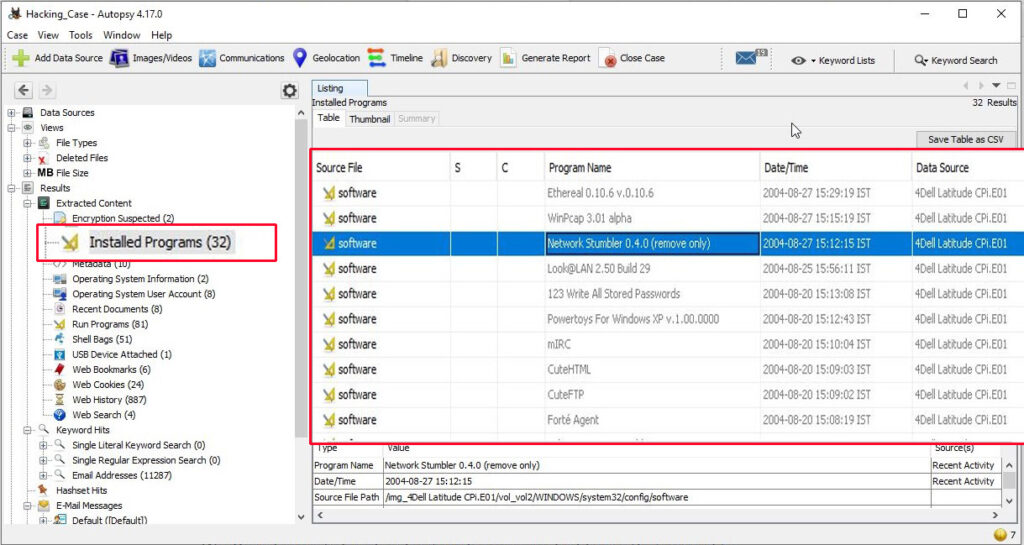
18. What two installed programs show this information?
We searched for local settings of all programs and found the information about this news server in the local settings of Outlook Express.
We found this information in the documents and settings file (and above shown path) of user Mr. Evil.
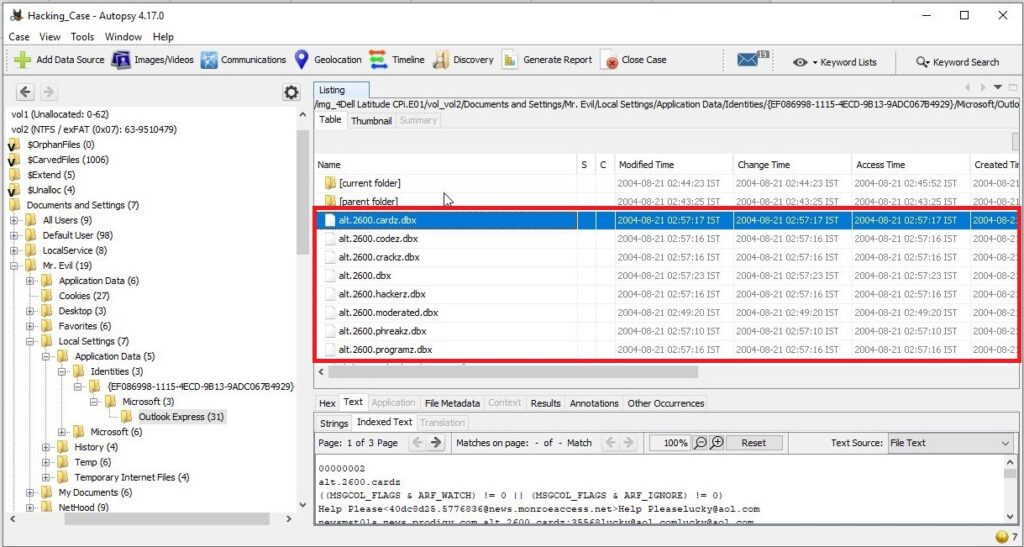
19. List 5 newsgroups that Mr. Evil has subscribed to?
We can find this information in the same file as above.
User Mr. Evil subscribed to over 23 news groups. The news groups subscribed by the user Mr. Evil are,
- Alt.2600.phreakz 2. Alt.2600 3. Alt.2600.cardz 4. Alt.2600codez 5. Alt.2600.crackz 6. Alt.2600.moderated 7. Alt.binaries.hacking.utilities 8. Alt.stupidity.hackers.malicious 9. Free.binaries.hackers.malicious 10. alt.nl.binaries.hack 11. Free.binaries.hacking.talentless.troll_haven 12. alt.hacking 13. free.binaries.hacking.beginner 14. alt.2600.programz 15. Free.binaries.hacking.talentless.troll-haven 16. alt.dss.hack 17. free.binaries.hacking.computers 18. free.binaries.hacking.utilities 19. alt.binaries.hacking.websites 20. alt.binaries.hacking.computers 21. alt.binaries.hacking.websites 22. alt.binaries.hacking.beginner 23. alt.2600.hackerz
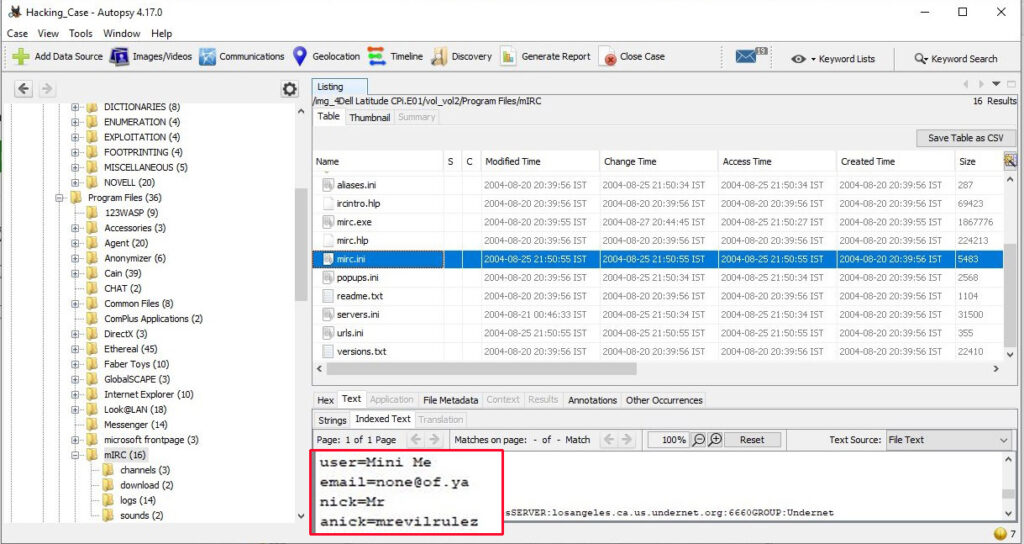
20. A popular IRC (Internet Relay Chat) program called MIRC was installed. What are the user settings that were shown when the user was online in a chat channel?
We can find this information in the .ini file of the installed program MIRC. The path to this program is in “C:\Program Files\mIRC\mirc.ini”
The user settings that were shown when the user was online and in a chat channel are
user = Mini Me
email = [email protected]
nick = Mr
anick = mrevilrulez
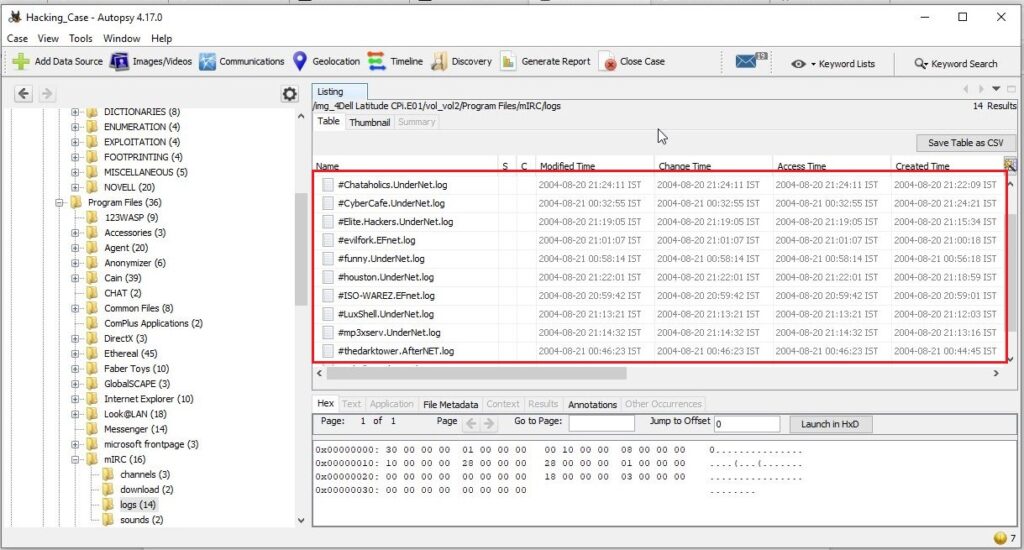
21. This IRC program has the capability to log chat sessions. List 3 IRC channels that the user of this computer accessed?
This information can be accessed from C:\Program Files\mIRC\logs file.
The IRC channels that this user accessed are
Ushells.undernet.log
Elite.hackers.undernet.log
Mp3xserv.undernet.log
Chataholics.undernet.log
Cybercafé.undernet.log
M5tar.undernet.log
Thedarktower.afternet.log
Funny.undernet.log
Luxshell.undernet.log
Evilfork.efnet.log
Iso-warez.efnet.log
Houston.undernet.log
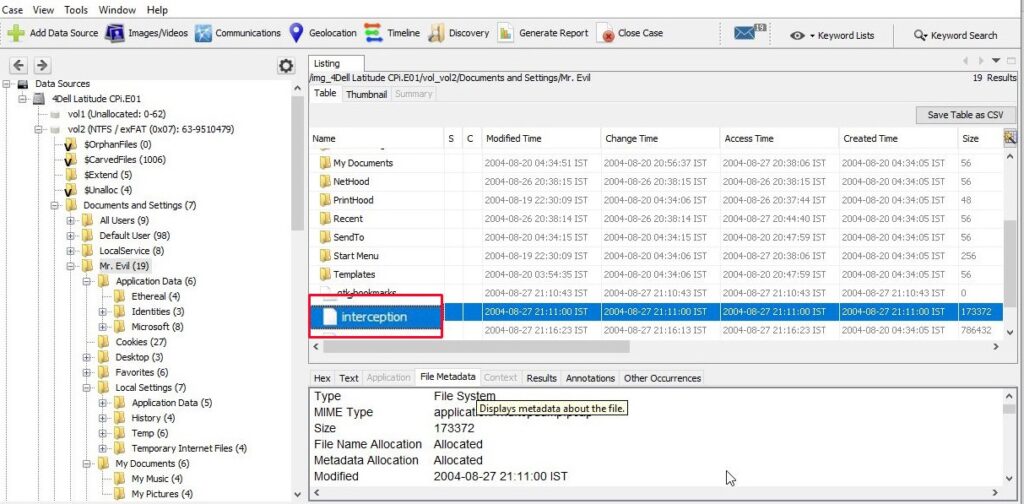
22. Ethereal, a popular “sniffing” program that can be used to intercept wired and wireless internet packets was also found to be installed. When TCP packets are collected and re-assembled, the default save directory is that users\My Documents directory. What is the name of the file that contains the intercepted data?
After going through the Documents folder, we found the file that contains the intercepted data. It’s name is “interception”.
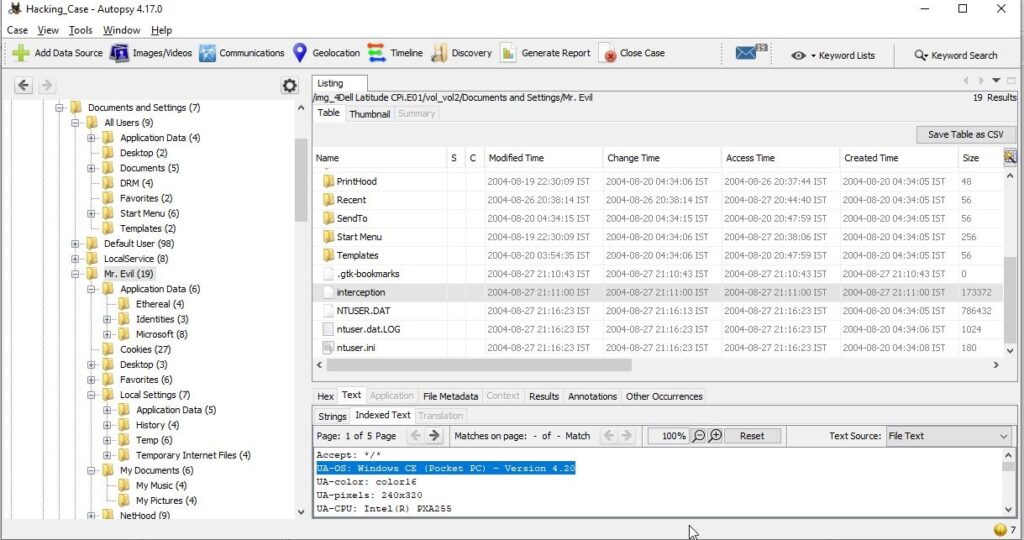
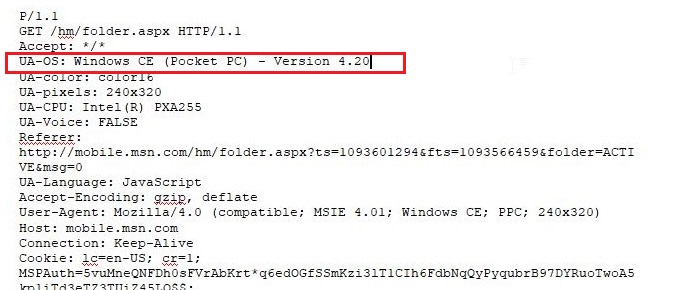
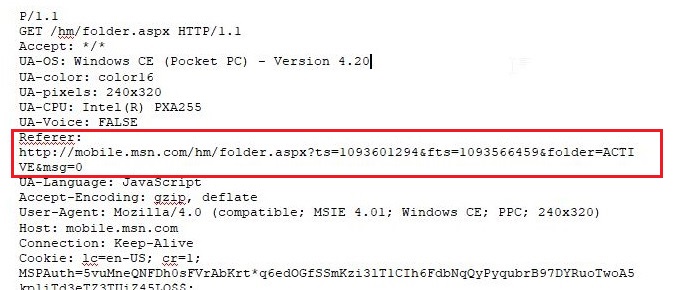
23. Viewing the file in a text format reveals much information about who and what was intercepted. What type of wireless computer was the victim (person who had his internet surfing recorded) using?
Viewing the file “interception” in text format revealed that the victim was using Windows CE Pocket PC wireless computer.
24. What websites was the victim accessing?
Even this information can be obtained from the same file “interception” which is a packet capture file. We found two websites the victim was accessing, Mobile.msn.com and MSN Hotmail Email.
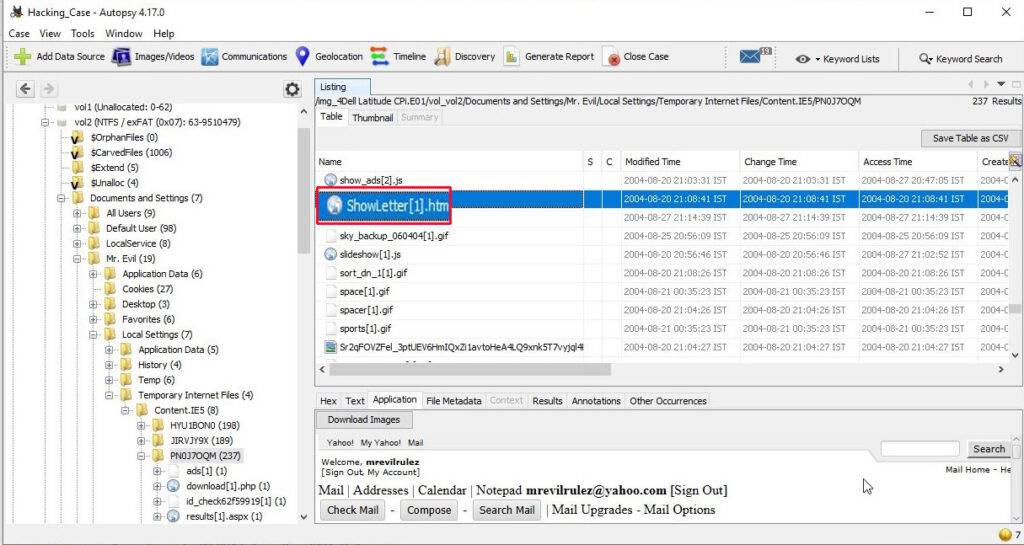
25. Yahoo mail, a popular web based email service, saves copies of the email under what file name?
Yahoo mail saves copies of email under the file name “ShowLetter[1].htm” which is in the temporary internet files folder of the user’s Documents and Settings.
26. Search for the main user’s web based email address. What is it?
This information can be found out in the same file. The main user’s web based email address is [email protected].
27. How many executable files are in the recycle bin?
The contents in the Recycle bin can be found in the RECYCLER folder.
There are in total four executable files in the Recycle bin.
28. Are these files really deleted?
As most of our readers already know, the files that go to the Recycle Bin are not permanently deleted. They are only deleted temporarily and can be restored easily to their actual location in Windows.
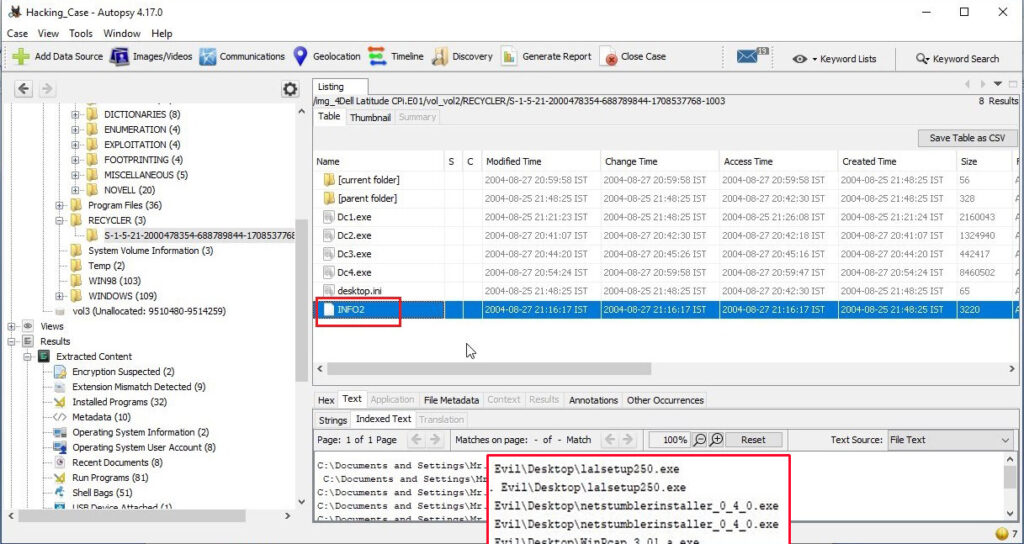
29. How many files are actually reported to be deleted by the file system?
This information can be found out from the INFO2 file.
The actual files deleted are three.
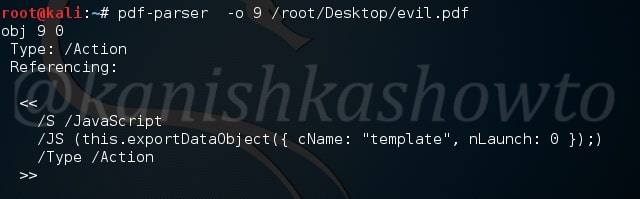
On being asked to find out any evidence that this laptop was used for hacking, we found in our forensic investigation that this laptop belonged to Greg Schardt who also has a online persona “Mr. Evil”. We found his operating system as Windows XP and he was running Ethereal, a packet interception program to capture network traffic. Apart from Ethereal, his system had six other programs which were used for hacking. He was active among many hacking related IRC channels and new groups. Corroborating this evidence with what his associates said about him, we can come to a conclusion that this laptop belonged to Greg Schardt and he was involved in hacking activities. This case can be closed now. Read how to perform forensics on a PDF File.