Vulnerawa stands for “Vulnerable Web Application”. This vulnerable web application developed by me is still in its nascent stages. I have started developing “Vulnerawa” to simulate a real website, i.e practice website hacking on this application and you are ready for hacking real websites. It is available for downloadhere, it has only SQL Injection vulnerabilities. (Gohereto see how to setup Vulnerawa). Here’s a picture of Vulnerawa below.
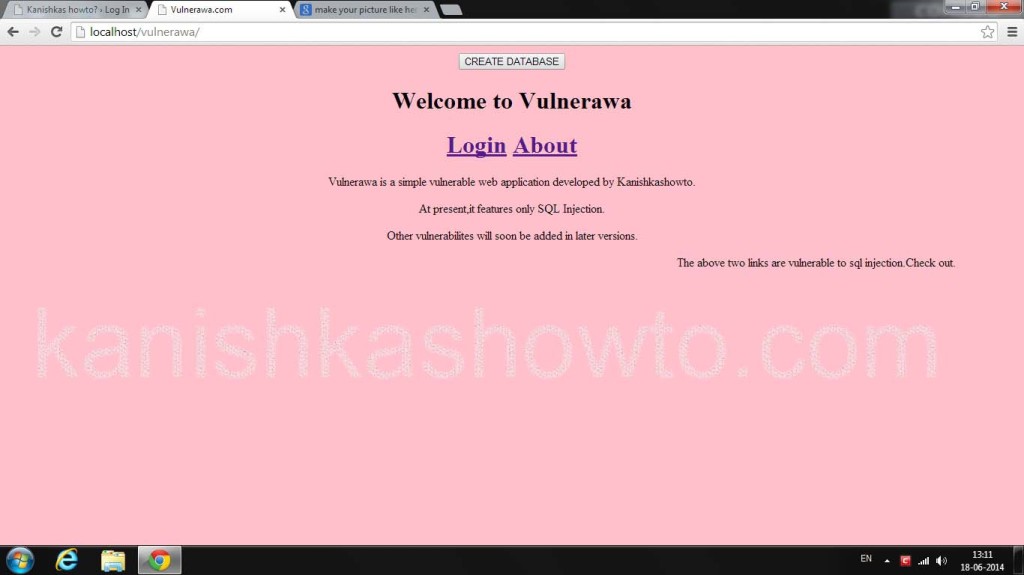
This vulnerable web app has two SQL injection vulnerabilities, url based and Login Bypass. As an example, let’s see login bypass using SQL injection. Click on link “Login”. You will be greeted with a login form. Enter single quote character(‘) as shown below in the picture below and click on “Submit”.
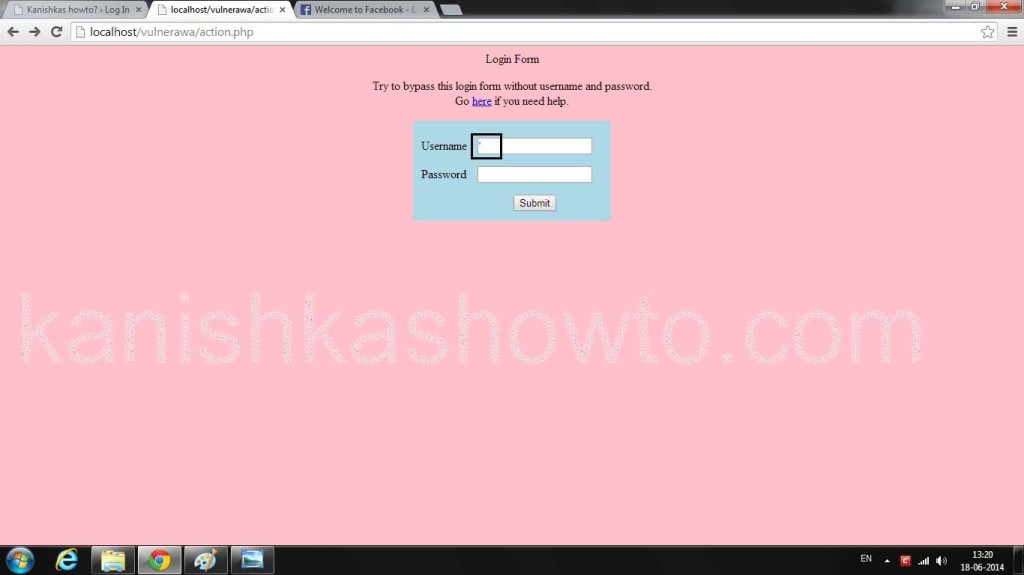
You will get an error as shown below, i.e the web app is vulnerable to SQL injection. This trick also works on real-time websites if they are vulnerable to SQL injection.
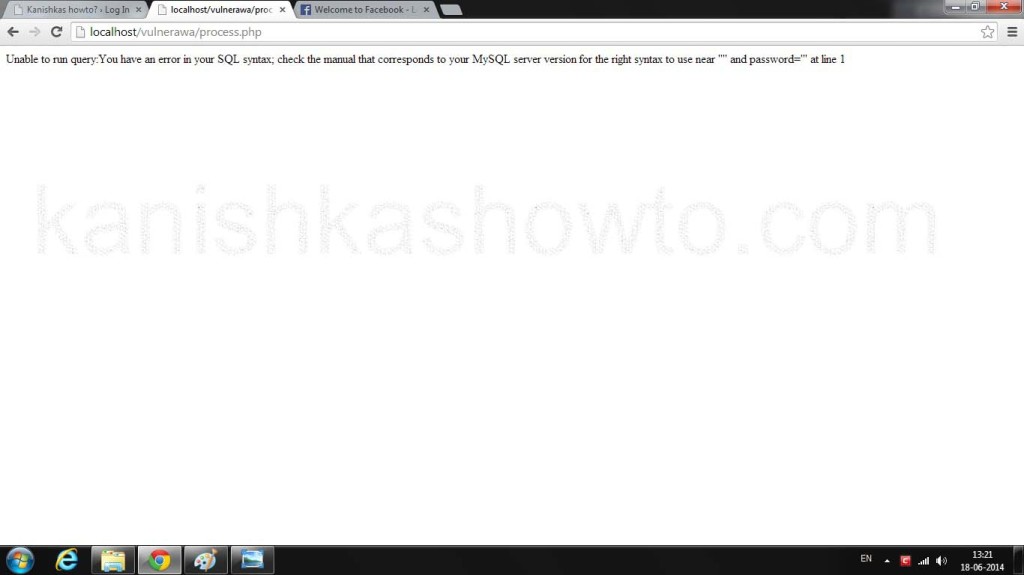
As the webapp is vulnerable to SQL injection, try to bypass the login form as shownhere. If you successfully bypass the login form, you will be taken to page shown below.
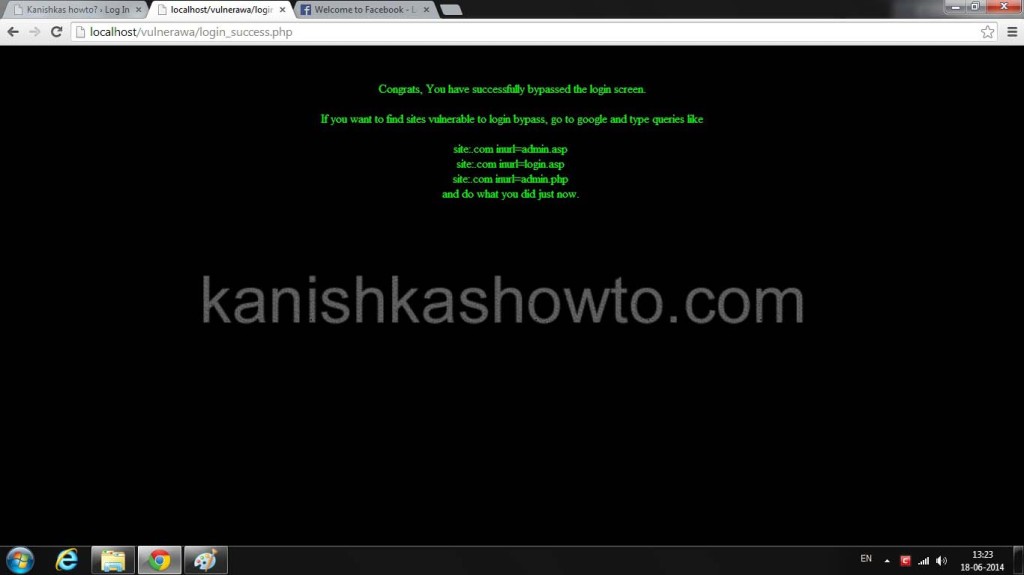
In the above page, apart from congrats message, you can see some google search queries. Copy these queries and enter it in a Google search box. This will give you a list of websites with login forms. You can check if they are vulnerable using the same method(the single quote) as shown above. Let’s say you found one vulnerable website as shown below. Let’s try to bypass it.
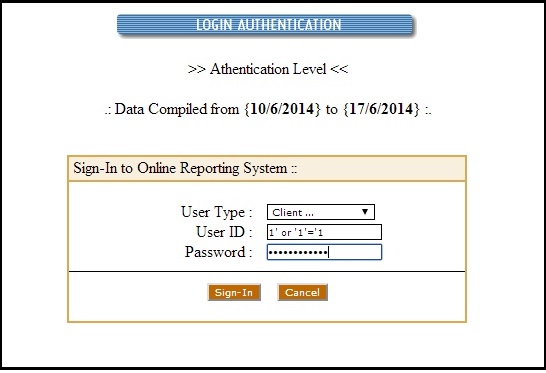
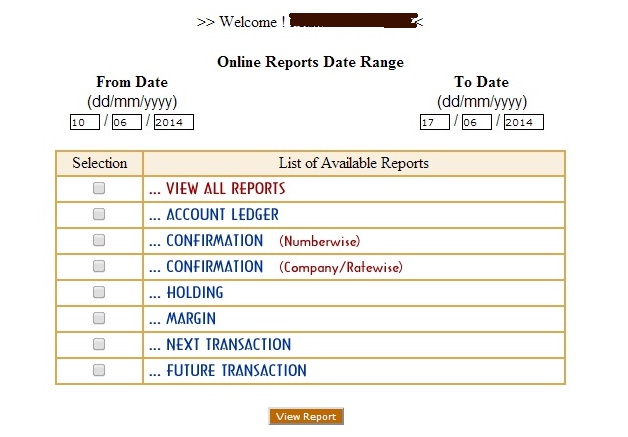
We have successfully bypassed the website as shown below.


[…] this howto, I’m using my own vulnerable webapp “Vulnerawa”. To know more about Vulnerawa go here. Vulnerawa has a file upload vulnerability in its careers […]
[…] it is a vulnerable web app coded by me to simulate a real website for practice. Read more about it here. First, download Wamp Server from here as appropriate to your system requirements. We will […]