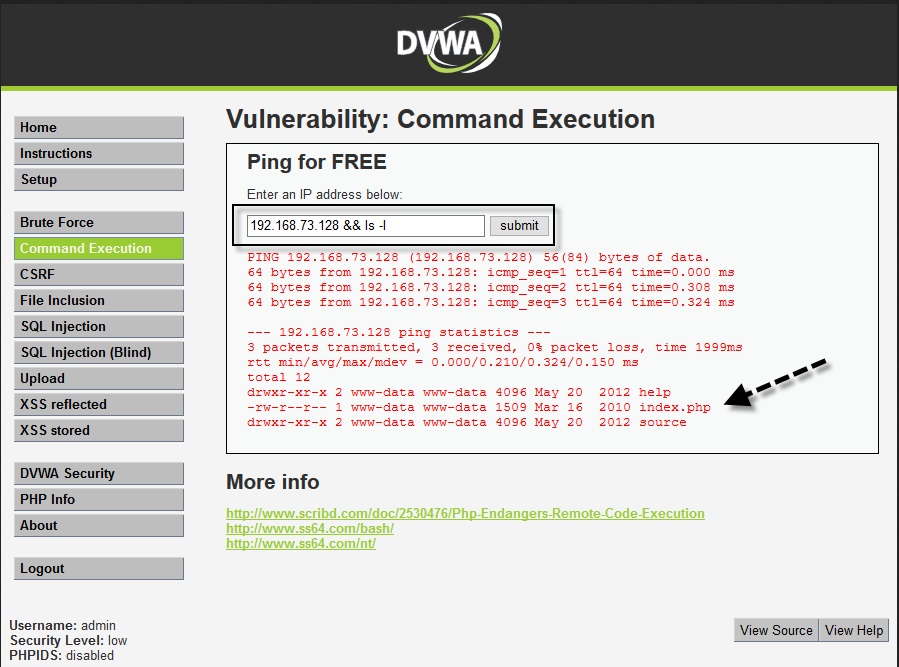
Hello aspiring Ethical hackers. In this blogpost, you will learn about another hacking attack Command Injection. This vulnerability can be found in a wide range of web applications, from small personal websites to large corporate applications.
What is Command Injection?
Command Injection is a security vulnerability that allows an attacker to execute arbitrary commands on a target system. It occurs when an attacker can inject malicious code into a vulnerable application, which the application then executes with the privileges of the application itself.
How Command Injection Attacks Work?
Command Injection attacks work by exploiting vulnerabilities in an application that accepts user input and then passes that input directly to a shell or command interpreter. This allows attackers to inject arbitrary commands into the input that are executed with the same privileges as the application.
Attackers can use various techniques to exploit this vulnerability, such as appending commands to existing commands or using shell metacharacters to execute multiple commands in sequence. The impact of a successful attack can be significant, ranging from unauthorized access to sensitive data to full system compromise.
Command Injection is a serious threat to web applications because it can allow attackers to bypass application-level security measures and gain unauthorized access to sensitive data or systems. Moreover, these attacks can be difficult to detect and can lead to serious consequences, such as data breaches, system compromise, and financial loss.
Common vulnerable points for Command Injection
Common entry points for Injection attacks include web application forms, user input fields, and API endpoints. Any input that is passed to a shell or command interpreter without proper validation and sanitization can be vulnerable to Command Injection attacks.
For example, vulnerabilities can be introduced in code through improper input validation and sanitization, as well as through the use of system commands that are not properly escaped or sanitized. Examples of vulnerable code include:
perl
$command = $_GET[‘command’];
system(‘ls ‘ . $command);
In the above code, an attacker could inject arbitrary commands into the $command variable, which would then be executed by the system function. Examples of command Injection payloads and techniques include using shell metacharacters to execute multiple commands, appending commands to existing commands, and using the $(…) syntax to execute subcommands. An example of payload using shell metacharacters might look like this:
bash
; cat /etc/passwd
This would execute the cat command to display the contents of the /etc/passwd file.
Real World Examples
Command injection attacks are a serious threat to web applications and have been responsible for numerous security breaches in the past. In this section, we will discuss some real-world examples of this attacks.
1. Shellshock Bash vulnerability:
In 2014, a critical vulnerability was discovered in the Bash shell, which is used on many Unix-based systems. The vulnerability allowed an attacker to execute arbitrary commands by exploiting the way that Bash processed environment variables. This vulnerability affected millions of servers and devices worldwide, including many web servers.
2. EquiFax Data Breach:
In 2017, Equifax suffered a massive data breach that exposed the personal information of over 140 million people. The breach was the result of a command injection attack that targeted a vulnerability in the company’s web application framework. The attackers were able to execute arbitrary commands on the server and steal sensitive data.
These are just a few examples of the devastating consequences of command injection attacks. In each case, the attackers were able to gain unauthorized access to sensitive data by exploiting vulnerabilities in web applications.
Detection and Prevention
To identify Command Injection vulnerabilities, developers should thoroughly review their code for any input that is passed to a shell or command interpreter without proper validation and sanitization. There are several strategies that organizations can use to detect command injection vulnerabilities, including:
1. Manual Code Reviews
Developers should review code for any instances where user input is passed to a command shell or operating system.
2. Automated Testing:
Organizations can use tools like Burp Suite, OWASP ZAP, and Nikto to scan for command injection vulnerabilities automatically.
3. Web Application Firewalls:
WAFs can be configured to detect and block command injection attacks before they reach the server.
There are several techniques that can be used to mitigate Command Injection attacks. Some of these techniques are:
- Input Validation: One of the most effective techniques to mitigate Command Injection attacks is to validate all user input. This includes validating the length, format, and type of input. Input validation can be done on the client-side, server-side, or both. It is essential to ensure that the input is sanitized to remove any characters that could be used for injection attacks.
- Restricted Shell Access: To prevent attackers from executing arbitrary commands on the server, it is recommended to restrict shell access. This can be achieved by using a chroot jail, a containerization technology like Docker, or by limiting the commands that can be executed by the user.
- Principle of Least Privilege: The principle of least privilege is a security best practice that recommends limiting the access and permissions of users to only what is required to perform their tasks. This means that the user should not have unnecessary access to the server or application.
- Update and Patch Software: It is essential to keep all software updated and patched to prevent known vulnerabilities that can be exploited by attackers. This includes the operating system, web server, database server, and any other software used in the application.
- Use Security Libraries and Frameworks: Using security libraries and frameworks can help in mitigating Command Injection attacks. These libraries and frameworks are designed to handle input validation, encryption, and other security-related tasks.
- Monitor and Log Activity: Monitoring and logging activity can help in detecting Command Injection attacks. By monitoring the application and server logs, it is possible to identify suspicious activity and take appropriate action.
That’s all about Command Injection. We will be back with a new vulnerability vey soon. Until then, Good Bye.