Hello, aspiring Ethical Hackers. In this blogpost you will learn about OS Fingerprinting. Before you learn about OS fingerprinting, you should know what exactly is Fingerprinting. Fingerprinting is a form of biometrics that identifies a person with their fingerprint. Why Fingerprint? Because GOD has created humans in such a way that two people (no matter how much population rises) have same fingerprints.
What is OS Fingerprinting?
Just like every human has his own fingerprint, operating systems too have a unique fingerprint. Windows systems have a unique fingerprint whereas Linux systems have their unique fingerprint. The process of determining this fingerprint to determine the operating system of the target is known as Operating System fingerprinting.
What is this required?
If a hacker or pen tester can find out the operating system of the target system, he/she can know which vulnerabilities to exploit or which payloads to design to gain access to the target system (For example, Windows need EXE payloads whereas Linux systems require .sh payloads.
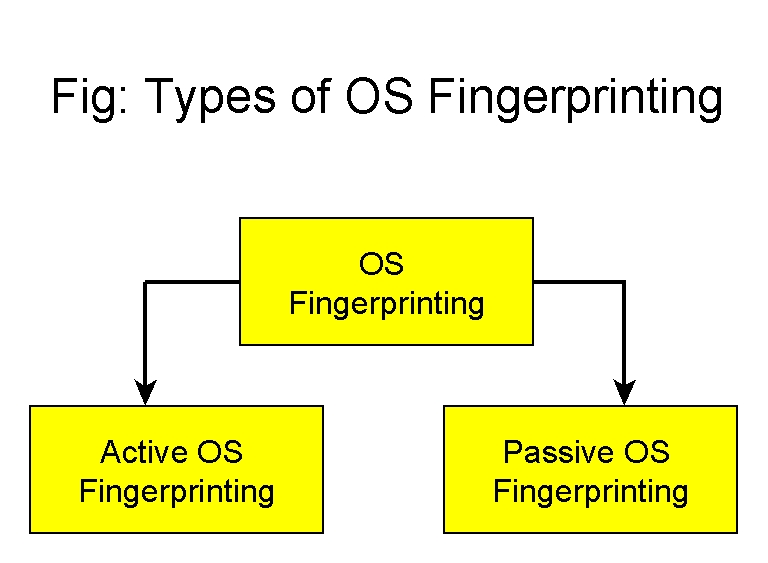
Types of OS Fingerprinting
Active OS Fingerprinting
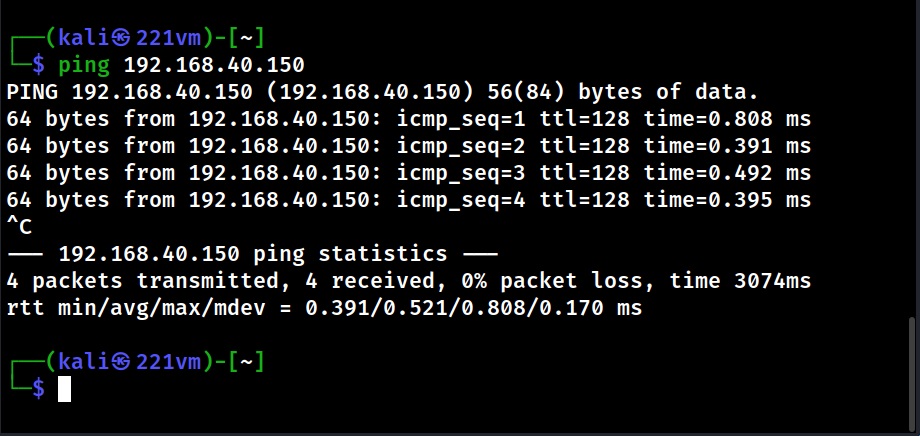
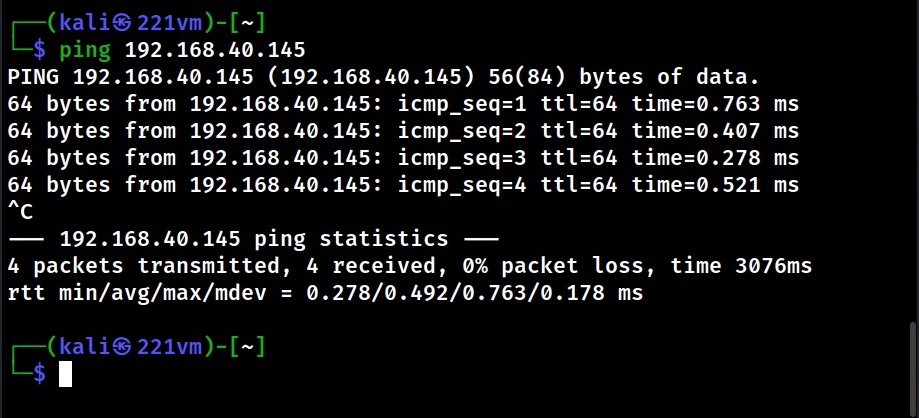
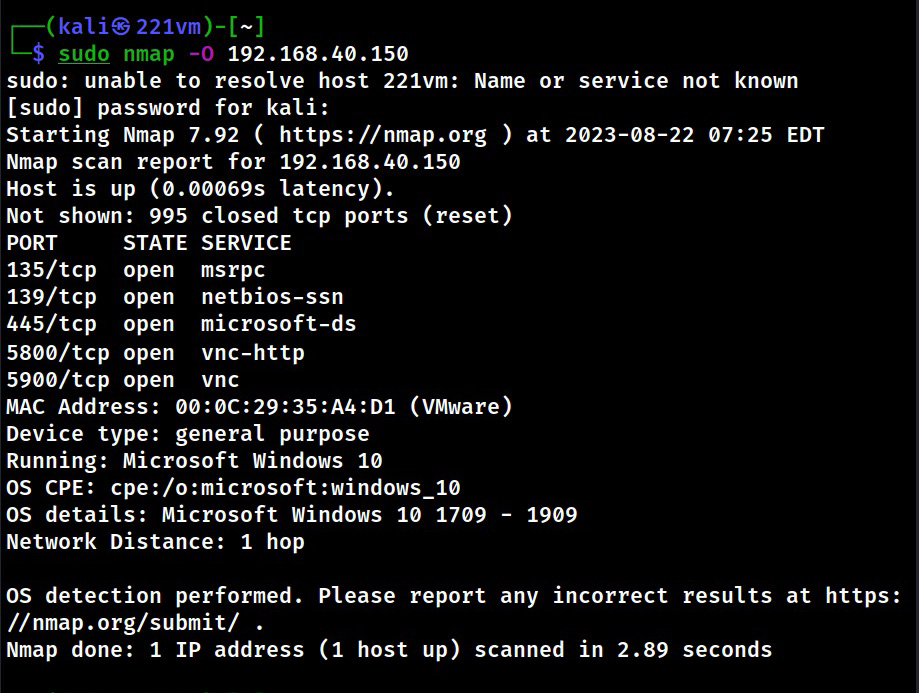
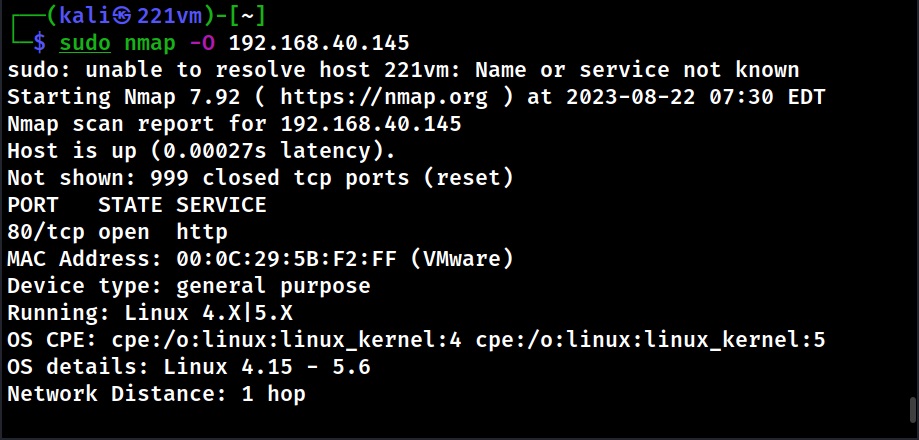
In Active OS Fingerprinting, specially crafted packets are sent to the target system and its responses are analyzed to determine the operating system of target computers. This interaction can be as simple as a ping or a scanner like Nmap. Using ping, we can detect a target operating system by observing the Time To Live (TTL) values as shown below.
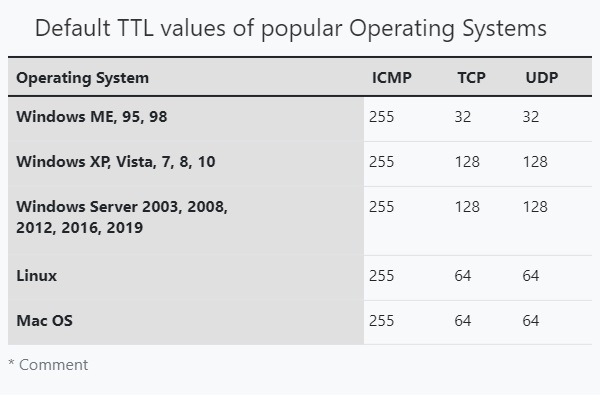
Time To Live (TTL) is the amount of time or “hops” that a packet is set to exist inside a network before discarded by a router. In simple words, it is the period of time that a packet or data should exist on a network before being discarded. This value differs from operating system to operating system. Here are the default TTL values of some operating systems. You can know about the default TTL values of more operating systems here.
Another way to perform Active Foot printing is by sending specially crafted packets to the target system. Among all Ethical Hackers use Nmap for OS fingerprinting.
Passive OS Fingerprinting
Although Active Fingerprinting is very effective and accurate at determining the target’s operating system, it is very noisy and can be easily spotted by Cyber security teams. Passive fingerprinting is a more effective way of detecting target system’s OS. Moreover, there is no chance of Firewalls blocking this type of fingerprinting. How is it possible?
In passive OS fingerprinting, a sample of packets coming from the target we are interested in are analyzed. For this purpose, we use a Packet Capture API. It relies on guessing the target OS by observing their TCP/IP implementation. Apart from TTL, this type of fingerprinting will observe window size, Don’t Fragment (DF) bit and Type Of Service (TOS).
Follow Us