Hi Readers today we will see a PEframe Tutorial. These days hackers are using numerous ways to get into our systems. One of them is by sending a malicious portable executable file to us or make us download the malicious executable file and execute it on our system. We have seen one such Real World Hacking Scenario in the issue of Hackercool February 2017. In this scenario we have not only seen how hackers can make malicious executable files but also how they bypass antivirus and convince the innocent users to click on those malicious files. In this howto, we will learn how to perform analysis of portable executable files.
Analysis helps us to determine what the file was intended to do once clicked. There are two types of analysis: static analysis and dynamic analysis. In static analysis the sample is analyzed without executing it whereas in dynamic analysis the sample is executed in a controlled environment. Static analysis is performed on the source code of the sample portable executable. There are various tools which help us in static analysis of portable executables. One such tool is PEframe. PEframe reveals information about suspicious files like packers, xor, digital signature, mutex, anti debug, anti virtual machine, suspicious sections and functions and much more. PEframe is open source and can be installed in Kali Linux as shown below.
Open a terminal and type the command as shown below to clone PEFrame from Github.
After PEFrame is cloned successfully, a new directory is formed with name peframe. You are automatically taken into this directory. This tool requires simplejson (a subset of JavaScript). So install it using pip command. Next, we need to run the setup.py file from the directory. Since it is a python file, we need to run the command “python setup.py” install to install PEframe.
Once the installation is finished, type command “peframe -h” to see its simple usage
Before we analyze the portable executables, let us analyze some files we created for tutorials of our magazine. The first one is msf.pdf we created using Metasploit.
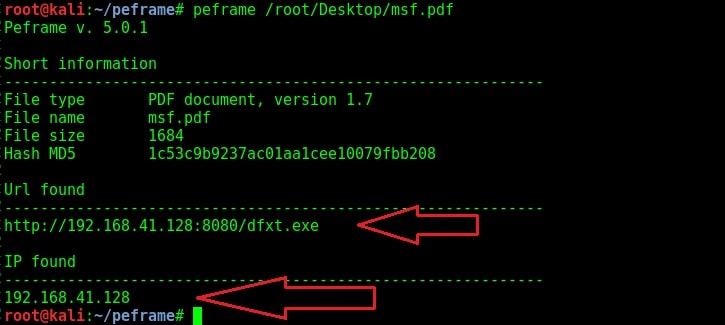
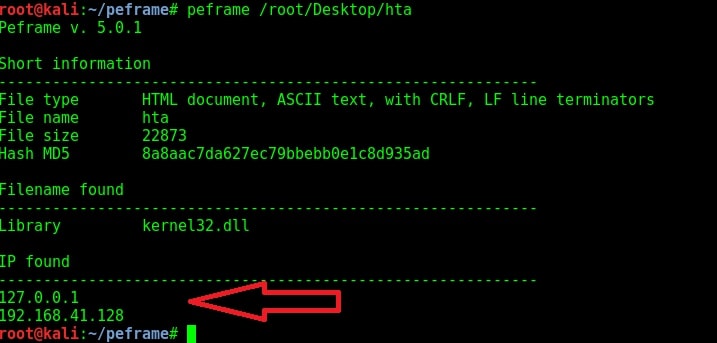
As you can see in the above image, we found not only an IP address but also an url hosting some executable file. It can be assumed that as we open this pdf file, another executable will be downloaded from the IP address and executed in our system. Let us now analyze a hta file created with Metasploit next. This file is analyzed as a HTML document with IP address and it has a library called kernel32.dll. This file probably opens a payload when clicked upon. Given below is another similar file in visual basic format.
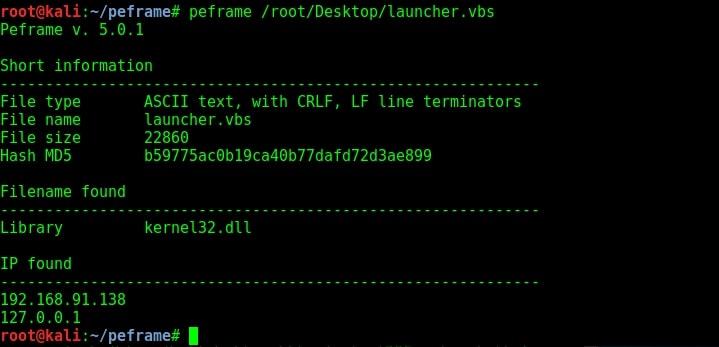
Given below is a macro file. You can see all these files have an IP address where probably a listener is running.
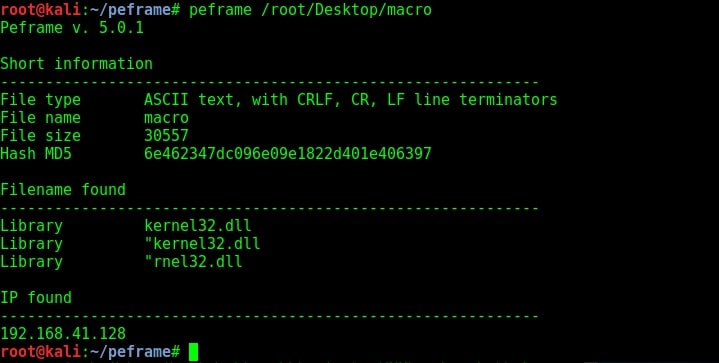
Now let us analyze a portable executable file. Kali Linux has some exe files already stored in its windows-binaries folder. We will analyze the plink.exe file.
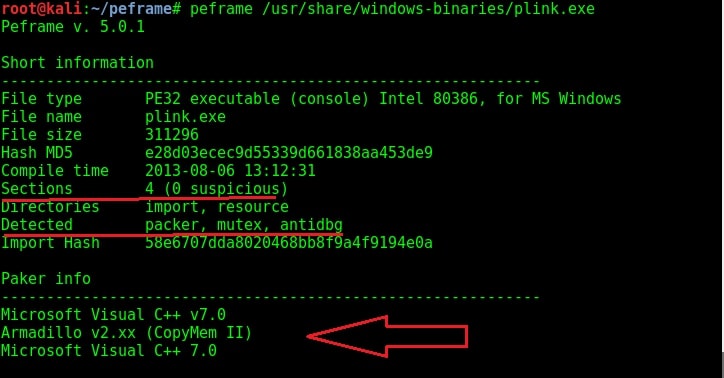
Plink.exe is a command line utility file similar to UNIX ssh. It is mostly used for automated operations. As you can see in the image given above, the program is giving more detailed information to us than the other files. The plink.exe has four sections and none of them appears to be suspicious. But the file has a packer, mutex and antidbg. The packer it used is Microsoft Visual C++ which is normally used for genuine programs.
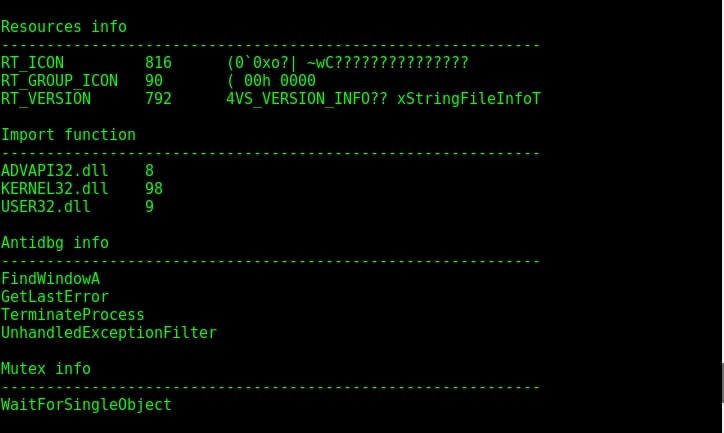
Given above is its Antidbg and Mutex information. The dynamic link libraries it imports is also given. Given below are the apis (application programming interfaces) used by the file.

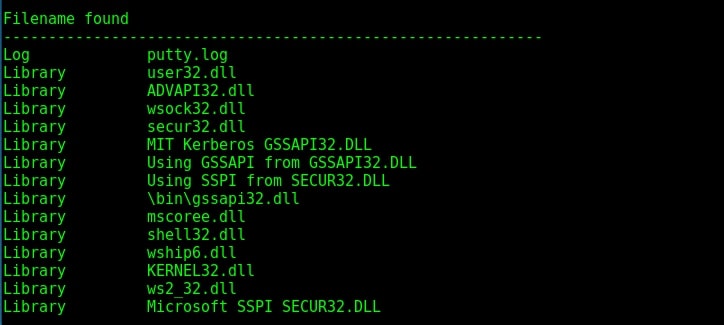
The filenames found in the portable executable are given in the image below. As you can see it has a big list of filenames.
Metadata is data about the data. Metadata reveals a lot of information about a file. Given below is the metadata of our portable executable. We can see that it is a part of Putty Suite.
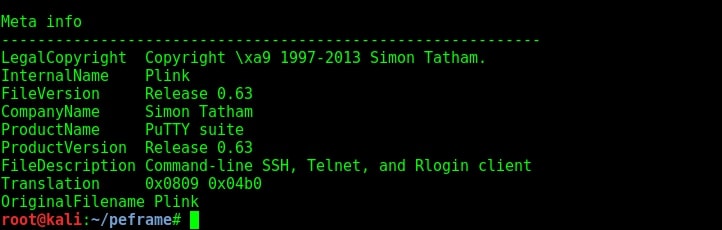
Even the description of the file is given. Normally malware does not contain so much information about itself like this Plink file. Only genuine files contain so much information because they have no use to hide themselves. Now let us analyze another file. This file is also present in Kali Linux and it is a keylogger. It is klogger.exe present in the same windows-binaries folder.
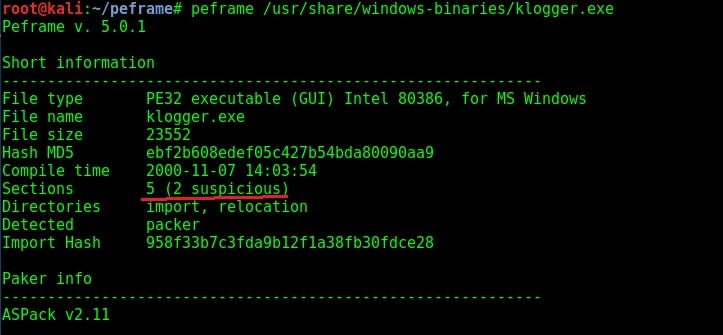
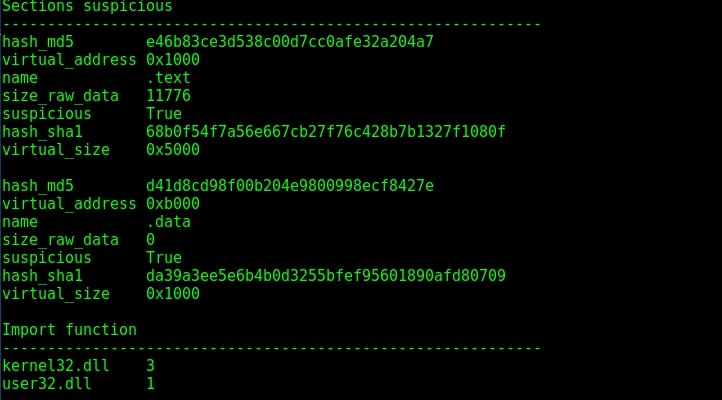
As you can see in the above image, the file which has five sections has two suspicious sections and the packer it uses is ASPack v2.11. Let us have a look at its suspicious sections once.
Given below in the image are its api alerts and filenames. As you have observed, this file reveals very less information than the previous analyzed file. This in itself does not mean that the file is malicious but it gives a general idea about it. That’s all about Forensics using static analyzer PEFrame. We will be back with a new tool in our next howto.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.
Follow Us
