Hello, aspiring Ethical hackers. In this article, you will learn about password sniffing. You should have observed that almost all the websites you have visited recently have a padlock sign and begin with HTTPS now. Google started giving minor ranking boost to websites with HTTPS enabled since year 2014. As you will learn by the end of the blogpost, there is a good security reason behind this.
What is Password sniffing?
Password sniffing or Credential sniffing is sniffing or capturing of credentials (or any other data) while they are in transit from one machine to another machine (usually from client to server). Password sniffing is only possible when plain text protocols are in use. Plain text protocols are those protocols in which confidential information like usernames and passwords are passed to the server in complete plain text and without any encryption.
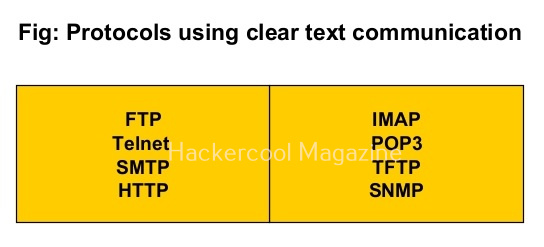
This allows anyone in middle to sniff on these usernames and passwords. Examples of plain text or clear text protocols are FTP, Telnet, SMTP, HTTP, IMAP, POP3, TFTP etc. Let’s see password sniffing practically. In this article, we will demonstrate the basic level of password sniffing on plaintext protocols. For this, we will be using three virtual machines which are on the same network.
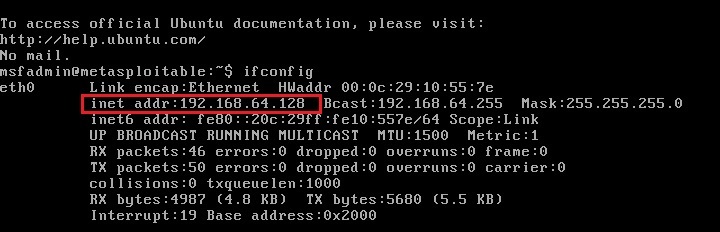
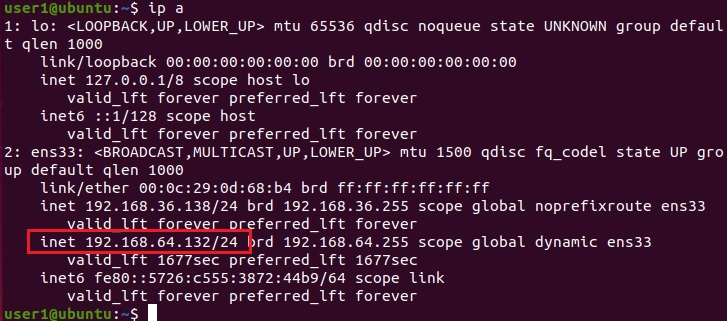
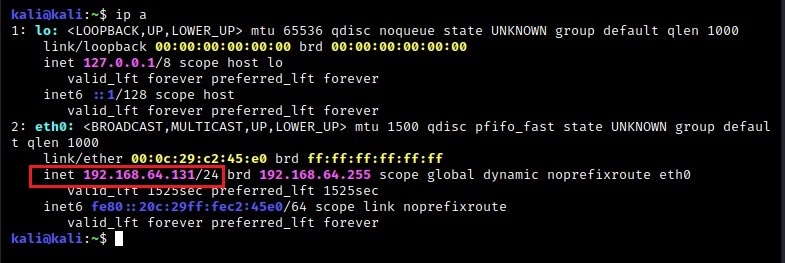
They are Metasploitable 2 which acts as server, Ubuntu which acts as client and of course Kali as our Attacker system. As you can see, the IP addresses of the three machines are
Metasploitable2 – 192.168.64.128 (Server)
Ubuntu – 192.168.64.132 (Client)
Kali – 192.168.64.132 (Attacker system)
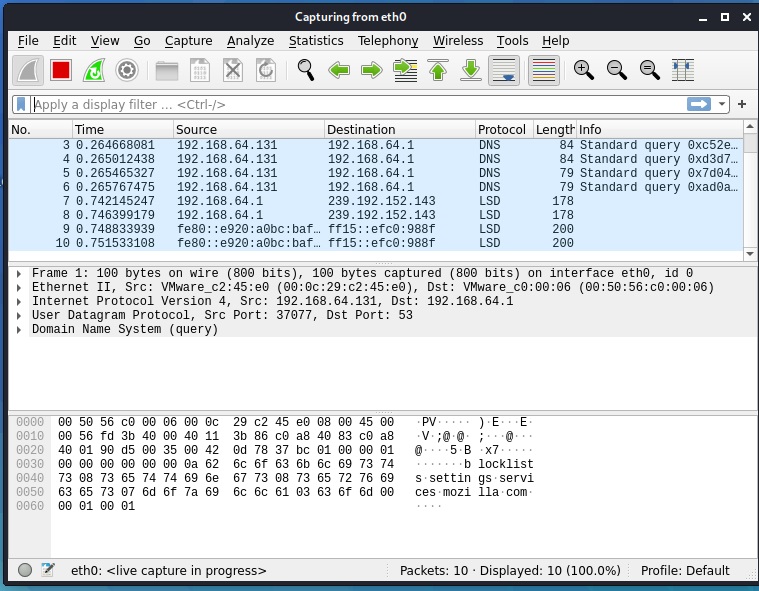
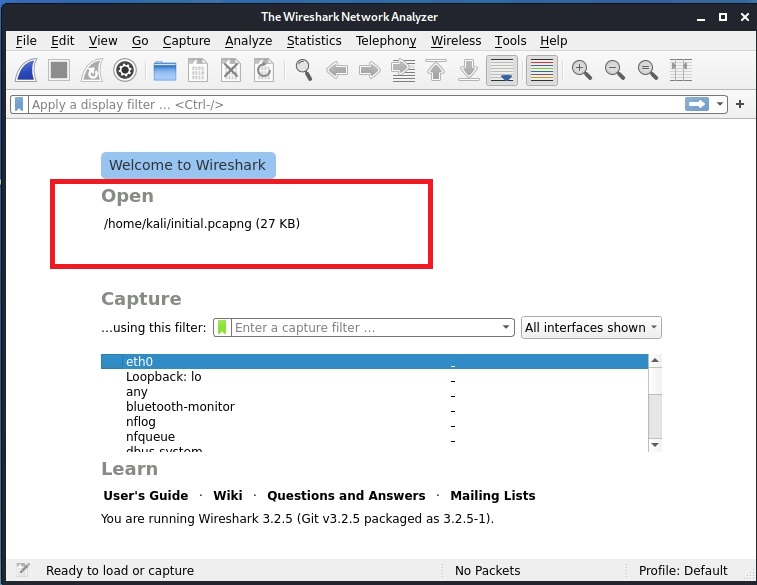
Let’s start Wireshark on the attacker machine (on interface eth0). It starts capturing packets on the network.
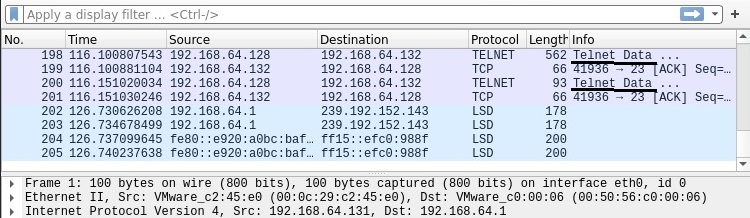
The reason why we are using Metasploitable 2 as our target is that it already has many services that we need for this tutorial preinstalled. The first service we will be using is Telnet. It is a protocol that is used for remote access on another system. On most Linux systems, Telnet clients are installed by default.
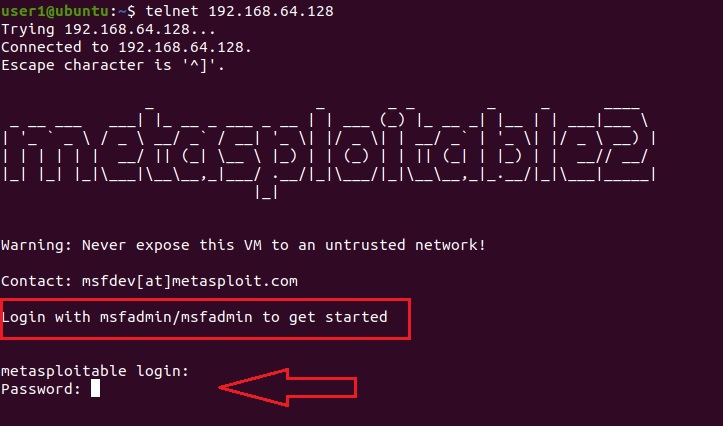
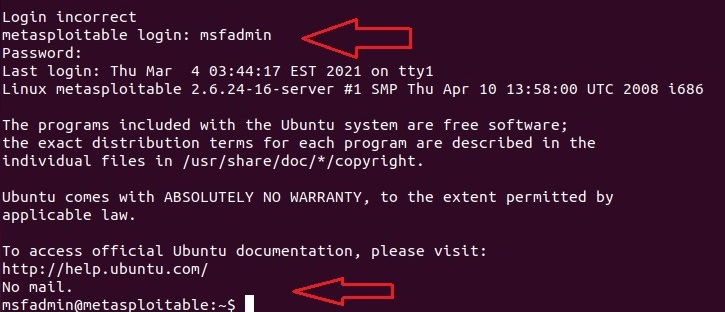
So we open a terminal and log into the Metasploitable 2 Telnet server with the credentials shown below.
The login is successful. Now on the Attacker system, we can observe the traffic being captured by the Wireshark sniffer. You can see data related to Telnet being transferred.
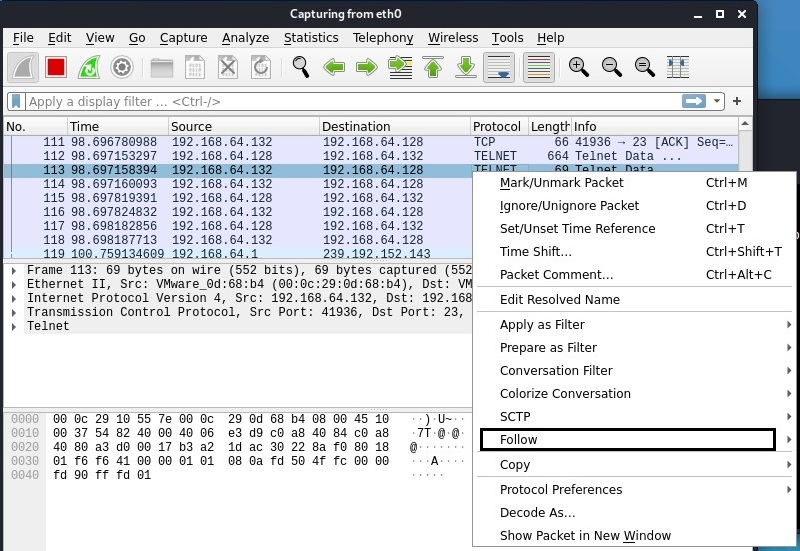
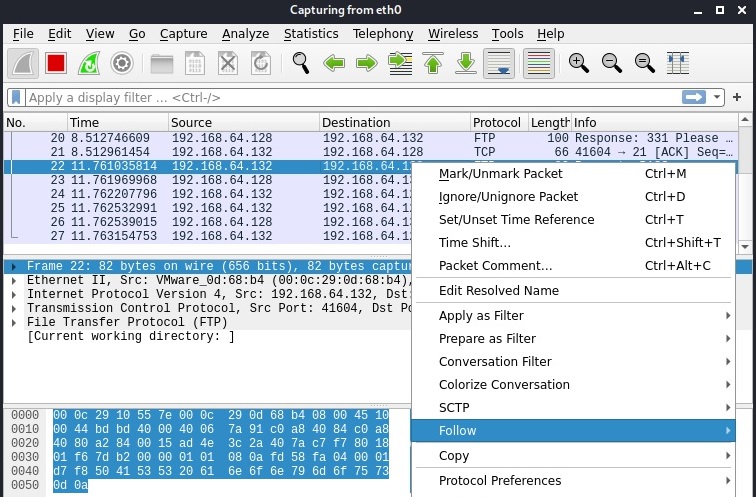
We can Right Click on that Telnet data stream and click on “Follow” as shown below.
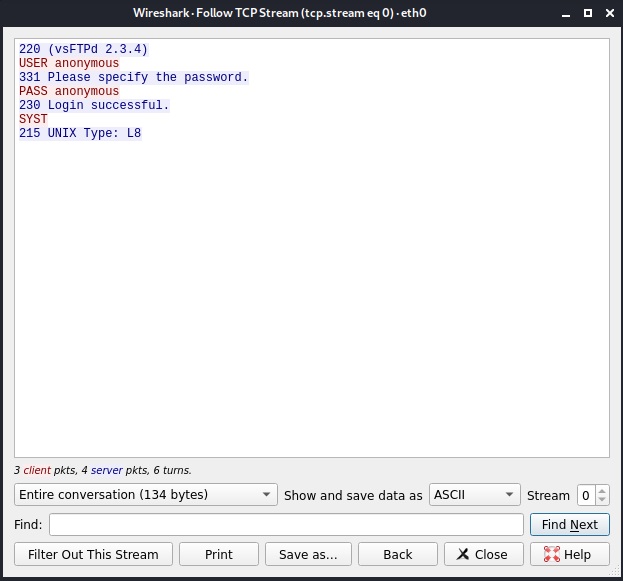
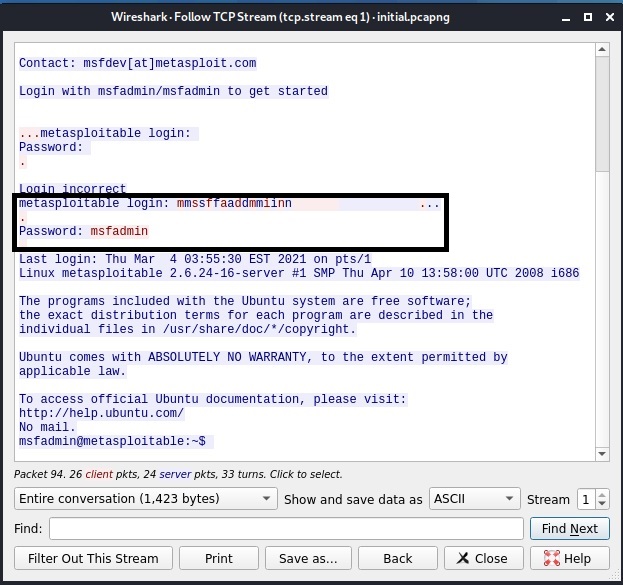
In the sub menu that opens when we click on the only option “TCP stream” a new window opens that will show only the TCP stream.
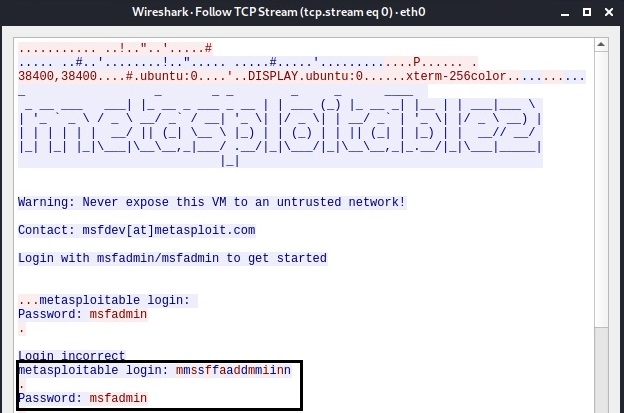
In this window, you can see the credentials we just used to login into the target system. Telnet is a plain text protocol which transfers credentials and other sensitive data in plain text. This allows sniffing of data. That’s the reason it has been mostly replaced by Secure Shell (SSH) nowadays.
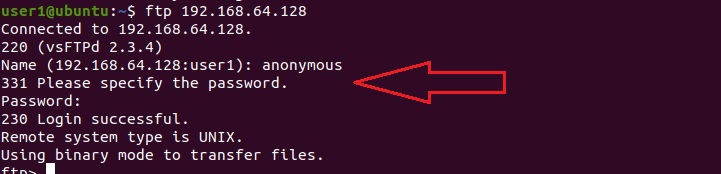
Let’s see another protocol. File Transfer Protocol (FTP) is a protocol that is used to share files. It is another protocol that transfers data in plain text. From our client, we login into the FTP server with credentials “anonymous:anonymous”.
Anonymous account in FTP is used to share files to anyone without the need for them to know credentials.
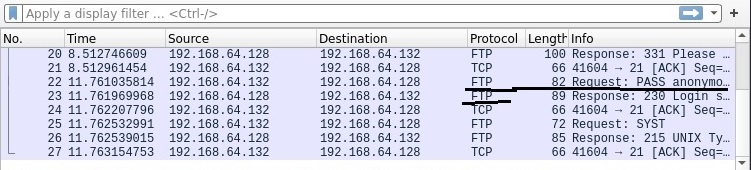
On the Wireshark interface, you can see FTP data being transferred.
We can view the TCP stream
This once again shows credentials.
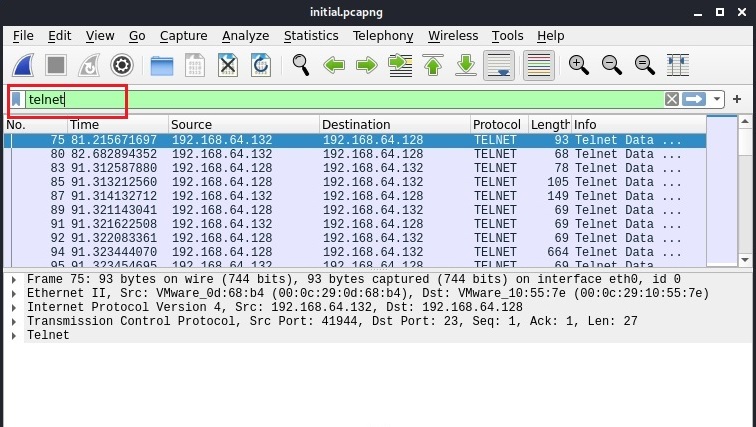
Instead of observing LIVE data transfer and following TCP stream from there, we can also just save the packet capture file and open the file later for analysis.
After opening the file, we can search for specific terms as shown below.
Then following the TCP stream gives us the credentials.
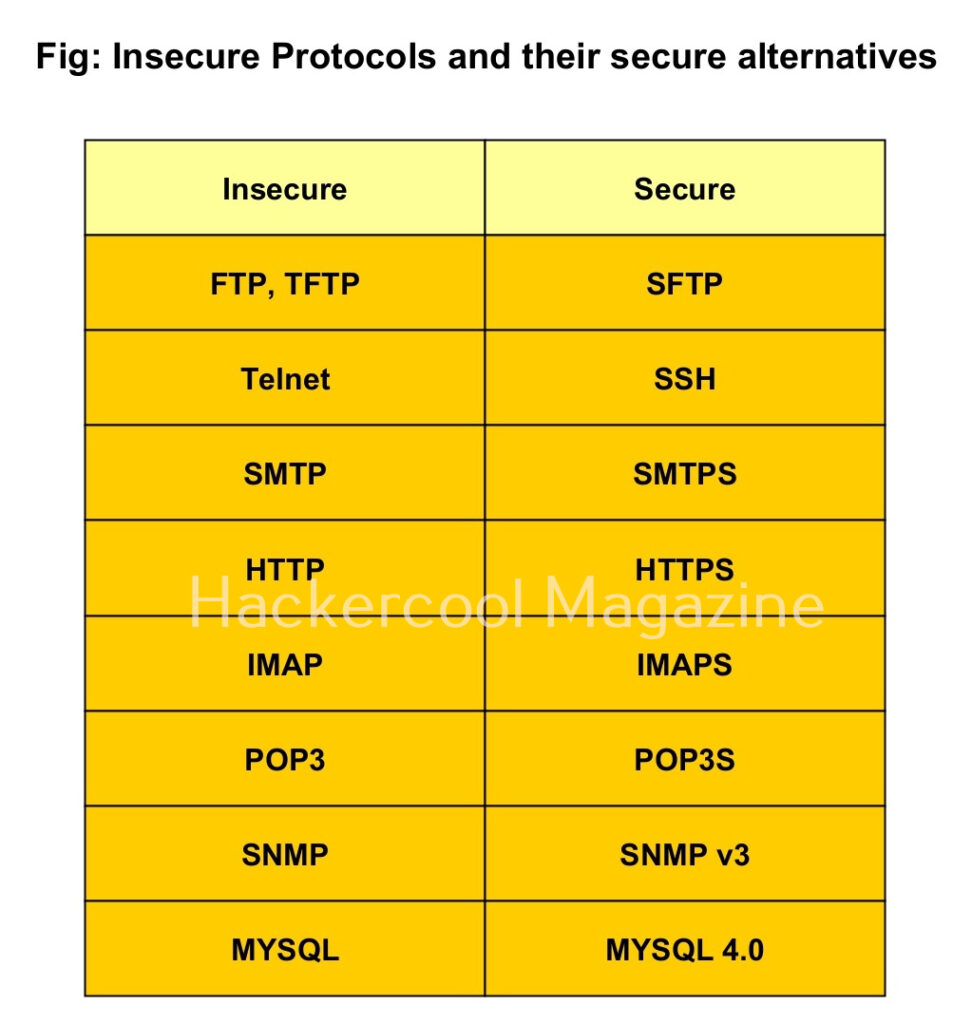
Seeing the vulnerability due to sniffing, many protocols have been replaced with secure protocols which transfer data in encrypted form instead of plain text form. These are given below.
Follow Us