Vulnerability Assessment is the process of evaluating the weakness of a system or network. It identifies the vulnerabilities in a system or network and helps black hats to devise exploits to get access to a target system or network. We developed this Vulnerability assessment by hackers article to give readers an idea as to how hackers perform vulnerability assessment. For example, imagine I am a black hat who performed a Nmap scan on the target (in this case, Metasploitable). The target has displayed so many banners of the services running.
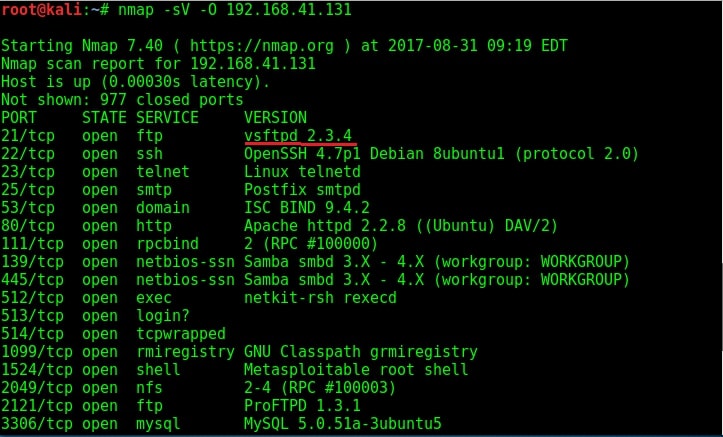
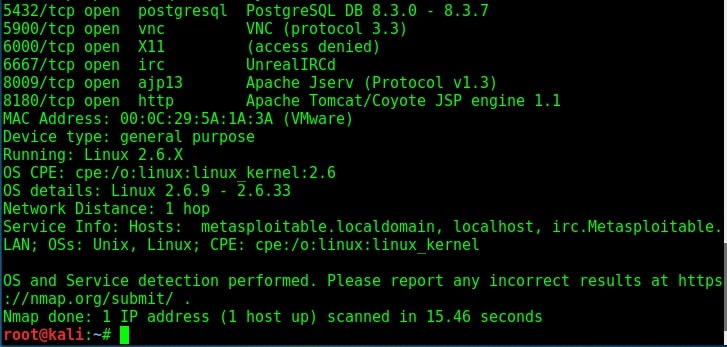
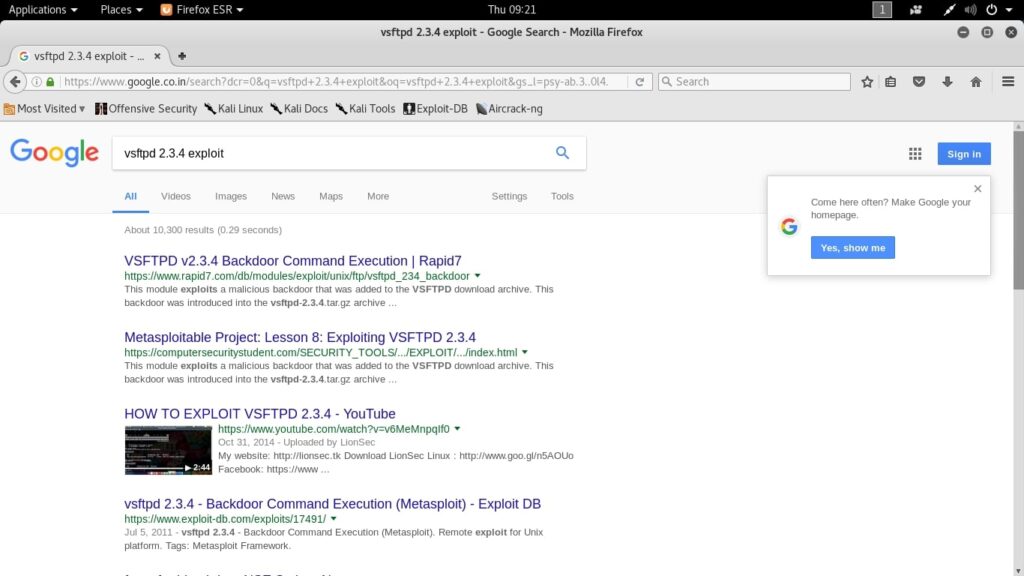
So the first thing I do is perform a Google search for any exploit or vulnerability for the service displayed. Luckily in the example below, we get an exploit for the aforementioned version of ftp server and that happens to be a Metasploit exploit. The only thing hacker has to do is download the exploit and run it.
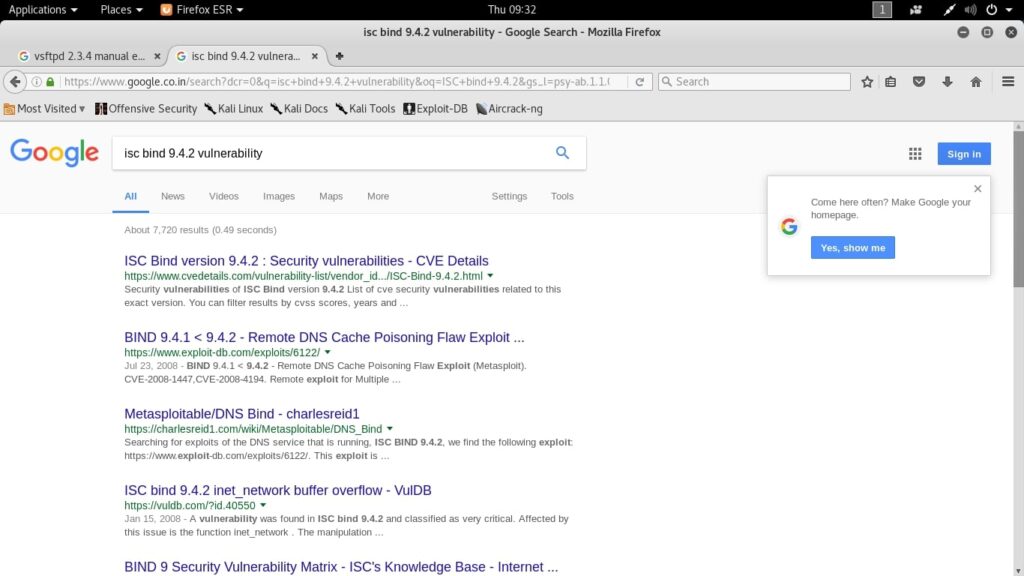
Here’s another example for another service. Here we have vulnerabilities listed. So we have to write an exploit for that vulnerability.
Displayed banners are like a godsend to hackers who are trying to breach the system or net -work. Searching for vulnerabilities or exploits for that particular service is the only thing hackers have to do. If the hackers are lucky, they might get an exploit or in the worst case a vulnerability. But what do black hats do if they don’t get any vulnerability or exploit for the service running on the target. Will they give up?. Well most probably no. If the service is running a open source version, they will download it and test it for vulnerabilities on their own system. Well if the service is running a commercial version, they will try to grab a pirated version of the software to test it. Once they are successful in finding a vulnerability, they will write an exploit for it. Python, Ruby, C and C++ are some of the common programming languages used to write an exploit.
Learn how to perform vulnerability assessment with OpenVAS
Follow Us

[…] This was about how to perform vulnerability scanning with OpenVAS Vulnerability Scanner. See how hackers perform vulnerability scanning. […]