Enumeration is the process of collecting information about user names, network resources, other machine names, shares and services running on the network. Although a little bit boring, it can play a major role in the success of the pentest. In the previous howto, we saw how to perform SMB enumeration and got some usernames on our target. So we don’t need to perform SMTP enumeration. But we may not be so lucky that SMB enumeration will be successful on every network. For networks like these, we may need to enumerate other services like SMTP.
First let me give you a basic introduction of SMTP. SMTP stands for Simple Mail Transfer Protocol. As the name implies, it is used to send email. It uses port 25 by default. If you ever sent an email, you have definitely used SMTP. SMTP servers talk with other SMTP servers to deliver the email to the intended recipient. Luckily this all happens behind the scenes and we don’t have to break our heads to understand this. But there are some things we have to understand about SMTP that will help us in enumeration.
As the term “simple” implies, SMTP server can only understand simple text commands. Sender of the mail communicates with a mail receiver by issuing these command strings and supplying necessary data. Some of the important commands are
1. HELO – sent by a client to introduce itself.
2. EHLO – another way of client introducing itself to server
3. HELP – used to see all commands.
4. RCPT – to identify message recipients.
5. DATA – sent by a client to initiate data transfer.
6. VRFY – verify if the mailbox exists.
7. QUIT – to end the session.
SMTP enumeration can be performed in many ways. The easiest way to do this is by connecting to the SMTP service port of the target with telnet (we have seen this in scanning and banner grabbing).
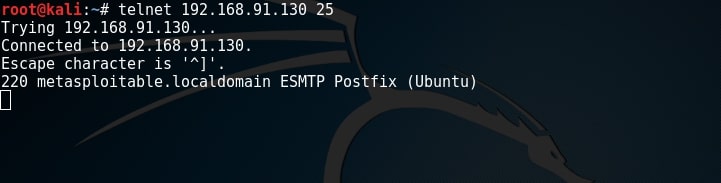
As you can see, we got successfully connected. From here, we can verify manually if each user exists or not. If you remember the article on SMB enumeration, we already have some usernames available. Lets use the VRFY command to check if users “user”, “msfadmin” and “root” exist in this system.
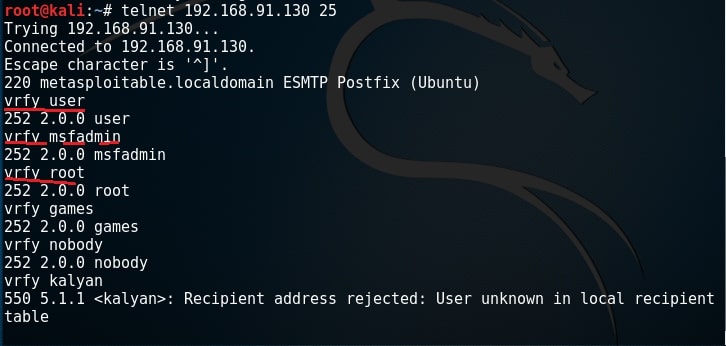
Yes, they exist. Similarly, let us test if user kalyan exists. As you can see in the above image, the user kalyan doesn’t exist. Nmap also has a script to perform SMTP enumeration. We can use the script as shown below.
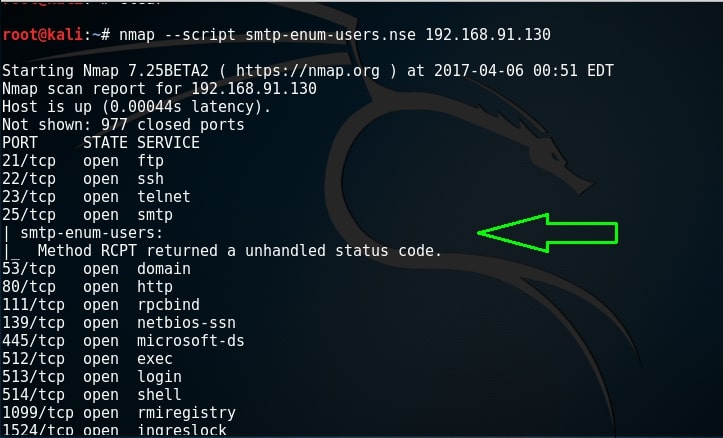
By default, Nmap uses RCPT method to check if a particular user exists. Unfortunately for me, it gave unhandled status code here. This Nmap script can be modified to use different methods. Here I changed it to use VRFY method to enumerate users. I have only scanned port 25 to remove the clutter. But still it gave me the same error.
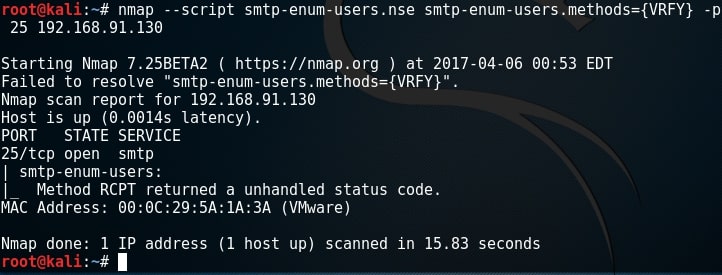
There is another tool in the arsenal of Kali Linux which is built specifically for SMTP enumeration. Its called smtp-user-enum. Here let us test if a user called “root” exists on the target system as shown below.
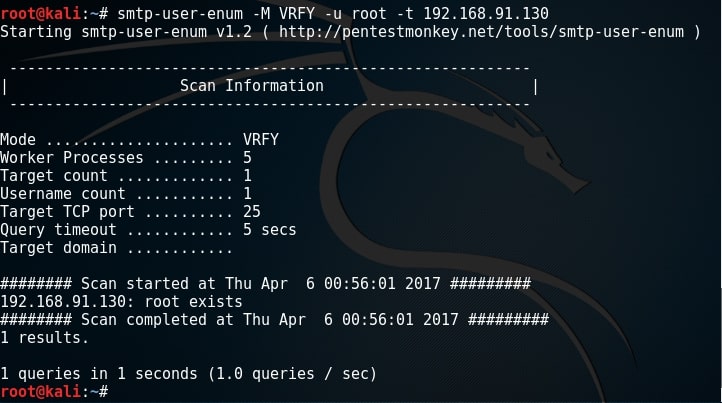
Since user “root” exists, I’m assuming other users like “msfadmin” and “user” also exist. While performing SMB enumeration, we created a wordlist which can be users on the target system. Now let’s enumerate if all the users in that wordlist exist. It can be done as shown below.
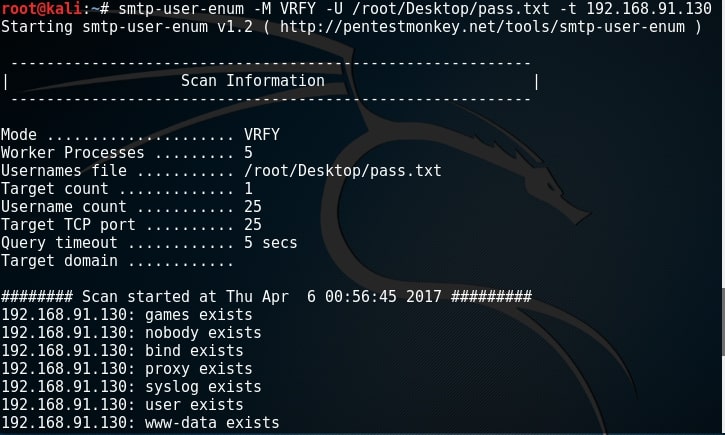
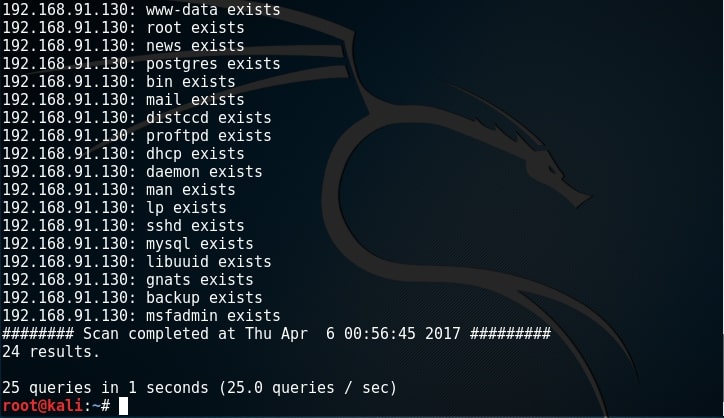
All the users we got during SMB enumeration exist. That’s good. In this case, we already have the wordlist of usernames (we got during SMB enumeratin). What if we don’t have the exact wordlist. We can use different wordlists present in Kali Linux. These wordlists are present in /usr/share/dirb directory.
What We Achieved?
We got some usernames which may be useful to us while exploiting the system in future. All these usernames have a recipient email address to them.
Follow Us
